Registration and deployment of Zoom-like domains help defraud consumers thousands of dollars
While some are taking advantage of Zoom’s ubiquity by advertising complementary goods like speakers or background apps, many are banking on the pandemic’s increased web traffic to hock consumers non-existent goods or those with dubious legitimacy. The end game is revenue. In this day and age, scammers are successfully bypassing defenses to defraud consumers—in one instance up to $1,700 a day.
Breakdown of a scam
The changing work environment has been a boon to video conferencing providers like Zoom whose daily participant figure topped 200 million in March—a staggering 535% increase in March alone. It also paved the way for the creation of thousands of Zoom-related domains whereby bad actors register domains containing the word “Zoom” to ride the company’s (legitimate) brand coattails in addition to parlaying off of industrial provider zoomwipes[.]com.
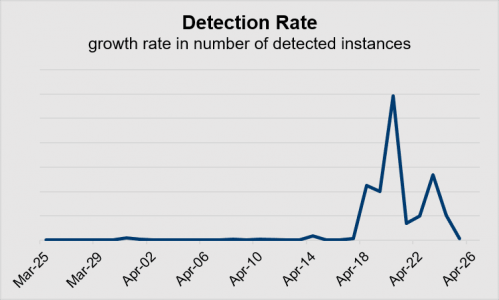
Reviewing thousands of Coronavirus-related domains yields several interesting scams. A recent favorite involves a campaign that successfully evades several malware blocking tools. Registered in August 2018, the “zoomequipmentwipes[.]com” was detected via in-the-wild scanning on March 17, 2020 and, due to its scam nature, immediately added to our block list. (Figure 1)
The domain continued to be detected sporadically over the next few weeks, before becoming a more regular presence in our client advertising ecosystems around April 5 where the creative is increasingly blocked before serving. The campaign offers a hospital-grade formula to disinfect industrial surfaces. (Figure 2)

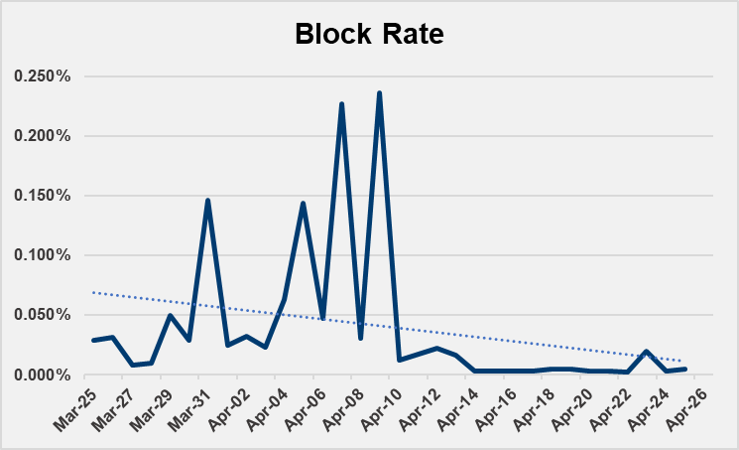
While the majority of the traffic is attributed to Google Marketing Platform, the incident also relies on 3 DSPs and SSPs to traffic the scam ads to premium publishers. With a $299 price tag it’s estimated the scammers attempted to earn $1,794 in one recent day just across a few publishers (earning an estimated 0.5% click thru rate and assuming a 10% purchase). The escalating nature of the scam and continued serving of the ad means this number is exponentially higher. (Figure 3)
Slippery slope between a scam and malware
While neither the ad nor the associated landing page are overtly malicious, they do attempt to defraud consumers through the promotion of an unproven or sketchy product. Our experience working with premium publishers provides guidance for activity that could potentially harm our clients’ reputations and revenue. For these reasons our malware taxonomy includes a scam/fraud type to account for those situations where a domain and/or creative purposefully attempts to mislead and/or extort consumers for financial gain.
Criteria for evaluating a scam could be subjective; however, The Media Trust team relies on at least 15 different (and proprietary) data points before classifying a domain as a scam. The “zoomequipmentwipes[.]com” ticks several boxes including:
- Short domain history: newly trafficking in the advertising ecosystem
- Poor quality creative & landing page
- Unsubstantiated claims
- Contact information is not legitimate; phone number is disconnected and the address is a Burger King location in New York City
- Changed IP addresses to avoid antivirus detection
In fact, our analysis of thousands of COVID-19 and Coronavirus-related ad campaigns confirms that 60% of sketchy campaigns do contain scam content, thereby recommending campaign termination with upstream partners and also blocking from serving to the user via Media Filter. These overt scans are also reported to federal authorities to supplement their investigations.
Scam or not to Scam: Is that the question?
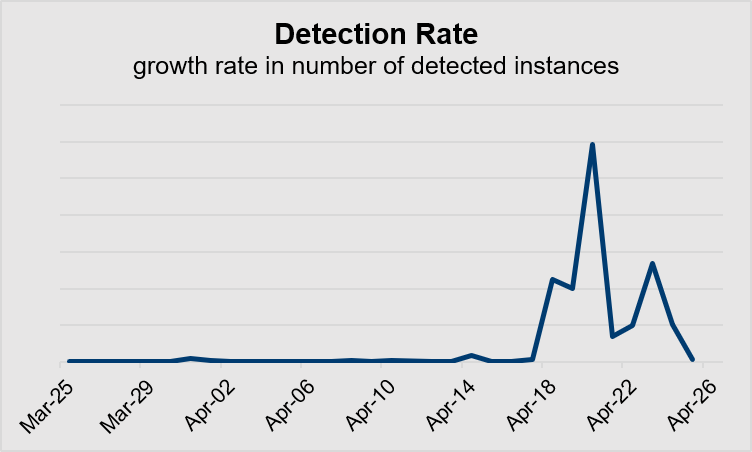
Various initiatives aim to shut down these fraudsters—especially in the US and UK—but the task is large. The Media Trust’s Digital Security & Operations team continues to see abnormally high amounts of web-based attacks. Unfortunately, Zoom’s name recognition is being abused by fraudsters in this instance. But, they aren’t the only ones. Coronavirus-related ads run the gamut from normal medical equipment supplies to outright predatory shams. (Figure 4)

Our job is to help remove the subjectivity from the process so our publisher and adtech clients can serve brand-appropriate content and keep their revenue channels open. And, flexibility must exist as one client’s poor creative is another’s bad ad.
To assess your approach to scam ads you need to:
- Determine the acceptable experience for your audience
- Review the percentage of Coronavirus ads trafficking through your environment
- Evaluate click-thru to landing page coverage (for adtech)
- Calculate revenue impacts for both campaign termination versus limited/restricted runs
- Develop policy and communicate to upstream partners. Policy should cover threshold for Coronavirus ads, examples in increasing restriction:
- Allowed, no special treatment
- Allowed-bounded, block scams
- Limited, only allow ads from designated partners
- Restricted, no Coronavirus or COVID-19 referenced ads
6. Monitor and enforce policy compliance via ad quality tools
With an eye to maintaining a positive user experience, The Media Trust recommends blocking campaigns classified as Scam/Fraud. Disabling the ability to defraud consumers is a critical step to building a healthier—and more rewarding—digital ecosystem.