Spike in mobile-targeting Ghostcat malware draws attention to new evasive measures
Key Learnings
- 40% jump in Ghostcat-3PC sightings via additional DSPs throughout March 2021
- New variants stripped of creative and landing pages, only containing heavily obscured malicious code
- Variants search for creative-blocker Javascript signals to evade detection
Recommendations
- Continuous client-side scanning to uncover evolving threats
- Counteract fingerprinting and cloaking by executing scans from various geographic locations and devices
- Reconsider relationships with partners continually platforming Ghostcat buyers
Since first catalogued by The Media Trust in 2019, Ghostcat-3PC has kept up a steady presence in the digital advertising ecosystem. Leveraging multi-step campaigns involving fingerprints and advanced obfuscated code, Ghostcat continually targets mobile devices with redirects to scam pages, delivery of adware, and even drive-by downloads.
But this malware has not maintained its status quo—a recent spike in distinct incidents revealed that Ghostcat has evolved in troubling ways (see Figure 1).
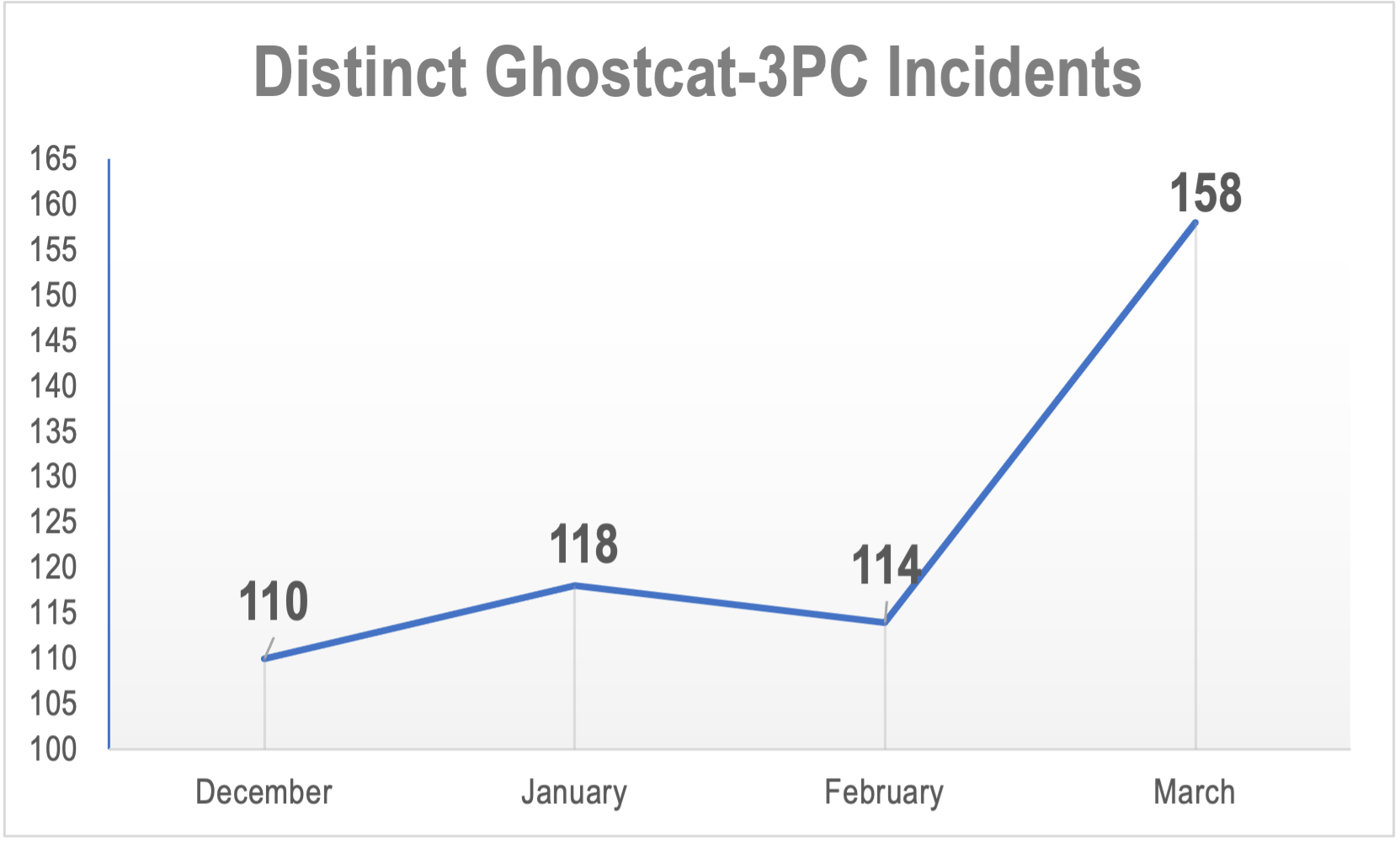
March saw a 40% month-over-month hike in Ghostcat incidents (note: a single incident can represent thousands of impressions) primarily in the US. While distinct incidents rose, the total number of scans declined, which can be attributed to platforms briskly shutting down campaigns as soon as the malware was detected.
In addition to a presence in numerous prominent buy-side platforms, Ghostcat is now detected across several new DSPs where it has not been seen before—some with large Asia-Pacific footprints. As realized in previous incidents (ICEPick-3PC in summer 2020), this activity is likely in preparation for a larger scale attack.
Ghostcat evolves to evade detection
Ghostcat uses giant blocks of inoperative code to hide its intent to redirect to scam pages or download malware. Fingerprinting is employed not only to determine whether Ghostcat is dropping into its desired environment—an Android device—but also whether it’s in a test environment or whether a blocking script is present. The latter is highly concerning because recently observed variants are actively sniffing for JavaScript variables used by several commercial creative blockers.
Newer Ghostcat variants leverage multiple host domains to send their malware—a primary URL that signals a secondary one to send the actual malicious payload. The Media Trust’s malware desk has observed Ghostcat cycling multiple primary hosts daily to evade detection.
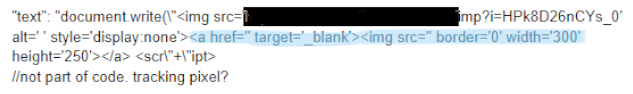
Missing ad elements aid in evasion
Ghostcat malware has changed into a streamlined malicious code delivery system by ditching creative and landing pages (see Figure 2). When served into a non-target environment, Ghostcat delivers nothing, often leaving an empty iframe or the occasional quixotic pink box (see Figure 3) This “obfuscation by omission” makes it difficult to not only detect a Ghostcat campaign, but also block it in real time.

Creative audits as first line of defense
The lack of included creative and landing page betrays an astonishing level of confidence bordering on arrogance regarding Ghostcat’s access to digital buying platforms. A campaign missing such critical elements—the most essential in digital advertising—should not pass an initial creative audit.
Platforms will have to reconsider their partnerships with upstream buying platforms that continually let Ghostcat slip through. Turning a blind eye to such obvious malware should have consequences.
Defensive Measures
- Continuous client side scanning to identify behavioral in known threats
- Counteract cloaking schemes through by variating geographic and device profiles
- Monitor upstream partners for repeated violations