Imagine this: it’s the beginning of Spring, and you’re excited to begin a long-needed home renovation project. You select Bob, a trusted and well-known contractor.
On the first day, Bob shows up with a handful of subcontractors, many of them expected. But as the days wear on, the number of subcontractors grows substantially, several of them questionable in need, skill, and character. Even if you fire the bad ones, new ones appear. By the end of the following week, your property is littered with trash, the newly installed toilets aren’t working, and things are starting to go missing—silverware, jewelry, and even a painting.
By the end of the month, the unvetted subcontractors that Bob brought to your home are knocking on your door daily trying to sell you things. Even worse, they’ve sold your address to others who are also calling on you with unrelated offers. It’s clear that Bob hasn’t done a great job vetting his subcontractors and you hesitate to recommend his services to others. [Figure 1]

The unfortunate reality of digital risk
This same scenario occurs on enterprise websites and mobile apps: hundreds of unmonitored third-party domains are present every time your consumer interacts with your mobile apps and website. This is a betrayal to consumers, who reasonably assume they are dealing directly with your business and maybe a handful of trusted vendors – not hundreds of unknown third parties that regularly cycle in and out.
Domain drift drives digital attack surface
To make matters worse, this variability leads to increased risk in the form of domain drift, meaning that new and unknown domains appear on a daily basis and change the way your website operates—it’s not uncommon for websites to experience domain drift of up to 45% per month. It’s as if a new set of unknown subcontractors show up to your home every day.
This ever-changing situation contributes significantly to your digital attack surface, and if unmanaged, old and emergent tracking technologies such as cookies and digital fingerprinting, will target your customers for nefarious purposes—including competitive or fraudulent offers. More than 100 third-party domains can be found on an average website—3-5X more than most IT teams expect—and many of them remain active for years. Think of Bob’s unvetted subcontractors targeting you with offers and selling your name to others.
Mitigating Digital Risk Requires Client-side Insight
Third-party domains are driving a massive rise in fraud, malware and disinformation across the web – leading to lost customers, missed revenue, and regulatory violations.
Enterprise IT teams typically focus on first-party code that is owned and/or directly operated by their organization. However, ~90% of today’s digital assets are comprised of third-party code that is written and managed by someone outside of the enterprise. This third-party code—analytics, virtual appointments, online chat, libraries, payment systems and more—only executes client-side on consumer devices.
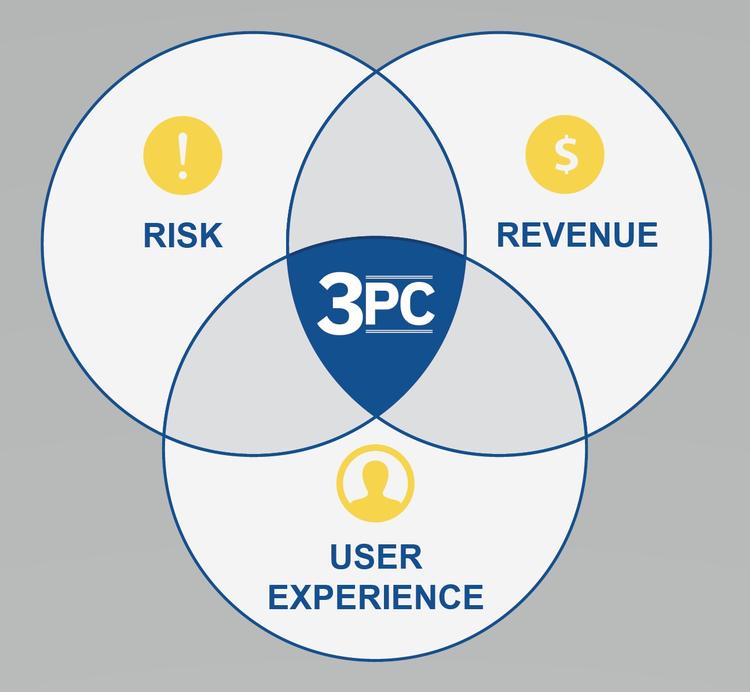
In the grand scheme of things, unmonitored third-party code lies at the intersection of risk, revenue, and user experience. [Figure 2] The ability to identify and control third-party code leads to improvement in all three of these areas. Unfortunately, companies who have attempted to gain control are often misled by false promises and vendor assurances.
Knowing your digital attack surface is first step to defense
Understanding your digital attack surface requires analysis of executing domains and their activities. Any domain—including those owned by authorized vendors—determined unnecessary for functionality or enhancing customer experience should be removed and blocked. Pursue strategies to monitor digital properties in the long-term and remediate threats as soon as they surface.
Tactics include:
- Scanning: continuous, client-side scanning captures the code executing on simulated user sessions
- Digital attack surface map: document your core executing code and relevance to site functionality
- Lockdown reports: alert on new domains and cookies that appear outside your map
- Scorecard: generate thorough reports to inform executive decision-making regarding digital risks
Don’t let your consumer-facing digital properties become a threat to your business. You can take control of the vendors and third-party code operating on your websites and apps and mitigate your digital risk—for the sake of your customers, and your bottom line.
Learn about digital risks present in 8 consumer-oriented verticals: Get report