Key Learnings
- 3X growth in FizzCore incidents across North America and Europe since beginning of 2021
- Increased leverage of native units, causing obstacles for detection
- Other named malware are now incorporating FizzCore techniques
Recommendations:
- Continuous client-side scanning, with special scrutiny on native units.
- Landing-page scanning from a variety of geographies and devices to discover hidden malicious schemes.
Celebrities tend to be an endless reservoir for clickbait—especially the malicious variety, which The Media Trust saw rise 15X in 2020. The UK’s National Cyber Security Centre reported shutting down more than 730,000 sites leveraging celebrity personas to push scams, with personal finance guru Martin Lewis and billionaire Richard Branson making the most appearances.
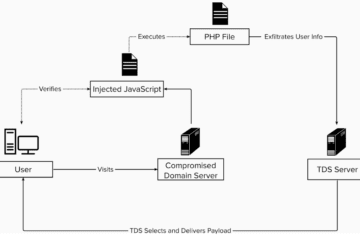
FizzCore is a malware attack that lures consumers into cryptocurrency and financial scams as well as phishing traps. Since the beginning of 2021, FizzCore incidents have more than tripled [Figure 1], with 54% detected in North America and 25% in Europe. April 2021 alone saw more than fivefold month-over-month growth, with FizzCore accounting for 36% of all the malvertising detected.
Evolution on two fronts
First catalogued as fairly straight-forward clickbait, Fizzcore features a variety of regional-specific celebrities. Clicking through on the advertisements led to malicious landing pages designed to impersonate premium publisher properties. These campaigns propagate financial scams, often leading with bitcoin messaging. [Figure 2]
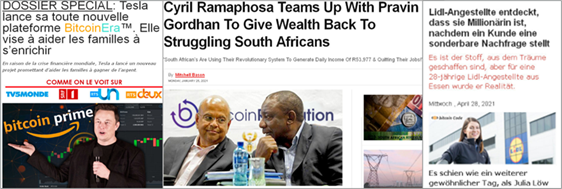
FizzCore has evolved in both its technical deployment and creative format. Throughout 2020 the creative grew more diverse, expanding to include well-known figures from politics and business. Sometimes campaigns will ditch the personalities altogether; what ties FizzCore actions together is the focus on financial scams such as get-rich-quick schemes. By the end of 2020, these campaigns began to regularly leverage cloaking elements, serving click-throughs to an innocuous landing page but then using fingerprinting to redirect users in the target environment to a malicious page featuring a scam or phishing lure.
In early 2021, a great deal more FizzCore began appearing in native ad units, almost reaching parity with standard display incidents. Native units feature text and image files that are dynamically rendered to match a publisher’s site. This dynamic capability in turn makes malvertising difficult to detect as there’s more opportunity to obscure text and use non-distinctive imagery.
Borrowing a cup of FizzCore
ICEpick-3PC, a major malvertising campaign, is now supplementing attacks with FizzCore payloads. ICEPick typically focuses on stealing user information (e.g., IP addresses) from Android devices. These ICEPick campaigns serve an HTML5 ad with hidden malicious code injected within to steal user data and invoke server side cloaking to deliver a second FizzCore creative that overrides the original legitimate creative, which on click will deliver FizzCore-style landing pages promoting financial scams. Such supplementing has created a new category of malvertising tentatively dubbed “FizzCore-like” that is currently being discussed and strategized among TAG Threat Exchange members.
Clickbait can’t be ignored
It can be tempting to dismiss concerns around malicious clickbait because “There’s no harm unless a user clicks!” but the ultimate consequences can still be devastating. The chief threat for the advertising ecosystem going forward is a continued escalation in FizzCore’s goals: adware downloads, credit-card skimming or even ransomware, which is causing consumer pain in the wake of the Colonial Pipeline attack in the U.S.
To minimize FizzCore threats consider adopting the following strategies to thwart FizzCore campaigns:
-
- Landing Page reviews: Pre-flight review of ad tags should include click through to landing pages to verify the authenticity of the content.
- Content analysis: Increase scrutiny of native units
- Ad Quality policy update: Evaluate your current policy regarding the treatment of clickbait ads to ensure it addresses celebrity bitcoin scams.
- Digital security expertise: A proactive team of 24/7 dedicated security analysts need to constantly evaluate new creatives, domains, and tags for malicious activity.
- Geographic profile scanning: Execute client-side scans from continuously changing geographic locations to ensure creative, tags and landing pages are clean.