Magecart attacks hit center stage in 2018 when it became public that the websites of several large, well-known organizations such as Ticketmaster, Newegg and British Airways had been breached by Magecart hackers. While there had been Magecart attacks before 2018, the size and scope of the 2018 breaches brought it to the attention of regulators, retailers and consumers.
What is the origin of Magecart?
Magecart originally was defined as attacks by a small number of cybercriminal groups (“Magecart groups”) that gained access to consumer data on websites, often by way of malicious third-party JavaScript code that steals consumers’ personal information from a checkout page, including credit card numbers, email addresses and passwords. Originally, Magento (a commonly used open-source ecommerce software platform) was the primary target of these attacks – combining “Magento” with “shopping cart” resulted in the name “Magecart”.
In the last few years Magecart has become an overarching term for credit card skimming breaches on ecommerce and other sites that collect credit card payments (also known as “web skimming” or “e-skimming”), expanding beyond its original meaning to include any attack by cybercriminals to gather and monetize consumer information across a wide range of ecommerce platforms. The same style of attacks targeting e-commerce platform vulnerabilities penetrate WordPress, Shopify, WooCommerce and more.
Anatomy of a Magecart attack?
The Media Trust’s 24/7 Digital Security and Operations team has analyzed Magecart and related attacks over a number of years and identified commonalities which make this type of malware difficult to discover and remediate. Overall, these attacks are perpetrated by bad actors who are well organized and carefully plan in advance, customizing each attack to maximize success.
- Carefully Planned: In many cases Magecart hackers may test the attack in advance, initially researching your website to determine the best attack vector and then carefully place code on your website for a limited time to see if it is detected. They may even purchase items on your site to see if their code is performing well and collecting the proper information.
- Evolve Over Time: Even if a Magecart attack is detected, the malware profile changes over time so it is much harder to find. The breach that occurred just last week on a major ecommerce site may look very different than the attack taking place on your site today.
- Multiple Attacks: In a number of cases Magecart groups will launch a multi-pronged attack, with more than one attempt to steal personal information occurring simultaneously or in direct succession. Stopping a single attack may still leave you open to a major breach.
- Sophisticated and Disguised: These attacks often mirror the payment page and checkout process functionality, so that consumers do not recognize the attack. Magecart attacks have been so well disguised that they continue for many months. And while some attacks immediately send the credit card data back, other attacks may write the data to local storage and retrieve it later to make it harder to determine a breach has occurred.
- Delayed to Avoid Detection: In certain cases Magecart code is designed to exist on your website without executing, checking to see if it has been discovered. After determining it has not been identified, the code will then execute the attack.
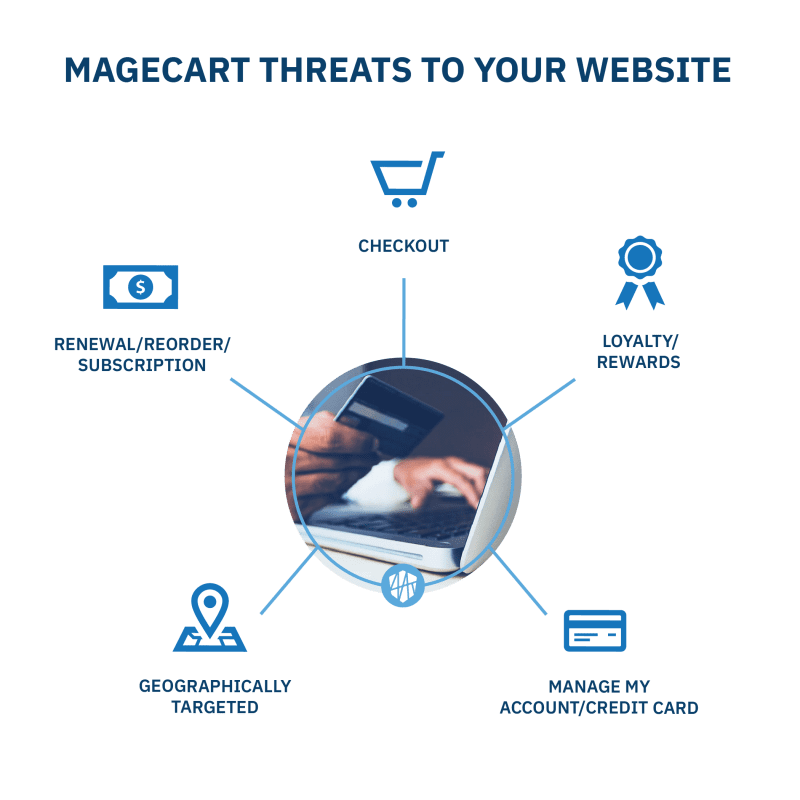
What are the dangers associated with Magecart?
The most obvious result of a Magecart breach is consumer fraud – the consumer’s credit card information is stolen and used in fraudulent charges by cybercriminals. Other related dangers include, but are not limited to:
- Brand damage: If the Magecart attack becomes widely known, the company’s brand suffers damage as consumer confidence in the company drops.
- Lost revenue/customers: Not only does the ecommerce vendor suffer the original loss from the Magecart attack, but as consumers avoid shopping online with the company, additional revenue losses occur.
- Impact to brand valuation: Any public company suffering a significant Magecart attack will run the risk of a drop in stock price for at least a period of time.
- Government fines and lawsuits: Fines and lawsuits resulting from significant Magecart attacks have exceeded $200 million for a single company.
- Compliance violations: CCPA, GDPR and other compliance regulations allow for fines resulting from companies not providing reasonable security practices protecting a consumers’ personal information.
Why don’t traditional cybersecurity tools stop Magecart attacks?
Traditional cybersecurity tools are designed to protect the data “inside the castle”. In other words, protect the data on systems inside the organization, such as employee computers and corporate servers housing sensitive information such as consumer credit card information or passwords. Even today some of the most harmful and publicized breaches occur when bad actors get access to a company’s internal servers and steal millions of passwords, credit card information and other sensitive personal data.
When it comes to a company’s website or apps, traditional cybersecurity is most often designed to protect system uptime or response time from being impacted by Denial-of-Services attacks.
While traditional cybersecurity has continued to advance in protecting what is inside the castle, it was not protecting against hackers attacking “the end point” or those customers and visitors coming to the company’s websites or apps. Many organizations think the user is responsible for the security of their own device and browser.
Magecart groups take advantage of this gap – if they couldn’t get access to credit card information through a company’s highly protected and encrypted servers containing this information, they could collect it by accessing the data when consumers were entering credit card information on the company’s website. Magecart is one of the most effective attacks put forward by bad actors to take advantage of this gap.
Given the significant incentive for Magecart groups to innovate and modify their attacks, it is important to constantly monitor and remediate these new threats with tools or services that come from vendors other than your traditional cybersecurity solutions.
Magecart Breaches
| Company | Date | Breach | Impact |
|---|---|---|---|
| Hanna Andersson | 2019 | Magecart style attack collecting credit card information, September-December | CCPA class action lawsuit filed in 2020, claiming lack of reasonable security practices |
| Macy's | 2019 | October attack collecting person information, including credit card data from the checkout and Manage my Account pages | Multiple class-action lawsuits filed in 2018 and 2019 claiming damages from stolen information |
| British Airways | 2018 | Attack active for 15 days and 380,000 customers data stolen | BA hit with $26 million GDPR fine from 2018 Magcart breach (originally faced $230M fined) |
| Ticketmaster | 2018 | 40,000 customers’ credit card data stolen; attack remained active for 5 months | Ticketmaster named in a $6.5 million lawsuit following the 2018 breach |
The cost of a data breach is significant, including lost revenue, regulatory fines and lawsuits. Larger firms can expect an average cost of $3.92 million from a breach, with firms under 500 employees experiencing an average cost of $2.5 million.
