
As Apple requires opt-in consent for app use of the IDFA identifier for ad tracking and measurement, The Media Trust’s Gavin Dunaway writes that advertisers are likely to pull out of the in-app programmatic market and open a giant opportunity for scammers.
A lot of mobile app developers are looking toward March and sighing something along the lines of: “It’s been fun, but the salad days are coming to a close.”
As promised in the iOS14 update, Apple will begin enforcing the user consent requirement for apps to share its Identifier for Advertisers (aka IDFA) in March. This was delayed from September; however, it’s been a dark cloud rapidly approaching for anyone advertising or monetizing in the mobile app space.
IDFA was a giant boon to mobile advertising. Arguably, it kick-started in-app programmatic by enabling cross-app targeting and measurement for advertisers similarly to the way third-party cookies function in browsers. While third-party cookies are (reportedly) hitting the end of the road in 2022, Apple’s IDFA will live on. However, advertisers, adtech companies, and publishers alike are pessimistic about the percentage of users who will opt-in due to a rather negative permission window from privacy-centric Apple.
Eric Seufert, who has become somewhat of an IDFA whisperer with his Mobile Dev Memo blog, predicts that only 20% of app users will opt in to sharing IDFA. While Facebook and Google are both expected to take billion-dollar revenue hits in the next 12 months due to the privacy switch, this will be a calamity for app developers of all shapes and sizes.
Unfortunately, those developers may get hit with a double whammy. They face severe revenue loss and a storm of malvertising and malicious ads taking advantage of a drooping programmatic marketplace and mobile vulnerabilities.
Publishers’ incessant mobile troubles
Mobile has been a long, hard road for digital publishers. As more and more of their traffic creeped over to smartphones and tablets during the last decade, publisher revenue opportunities dwindled. Less screen real estate was available to show display ads, visitors scrolled by impressions at warp speed, and the available formats not only failed to satisfy advertisers, but also alienated audiences.
And that was before Apple’s Safari, the most widely used mobile browser in the US, introduced Intelligent Tracking Protection (ITP) and cut off third-party cookie support. Eventually, Apple plans to put even tighter restrictions on first-party collection.
At AdMonsters Publisher Forums, ad ops professionals described their mobile web environments like ghost towns. “Oh yeah, the advertisers know that iOS users skew more affluent and that we have solid first-party data segments. But they won’t bite without client-side measurement capabilities and attribution.”
Scammers step in
No surprise then that the scammers saw a weak mobile programmatic marketplace and came to play. The current age of ad quality challenges started with omnipresent mobile redirect campaigns. For a while in 2018, it seemed like every weekend you could be greeted by scam announcements that you’d won a gift card if you dared to brave the mobile web.
Much has changed since then. Publishers have creative blockers at the ready for redirect barrages. But bad actors now seem to be favoring malicious clickbait slathered in cloaking code over the ol’ redirect.
And their interest in compromising mobile users has only grown. The biggest named malvertising threats of 2020, including LuckyBoy and IcePick, used fingerprinting to pinpoint mobile devices.
Late 2020 and early 2021, The Media Trust saw a dramatic rise in malicious ads on mobile devices. (And when we refer to an incident, we mean a specific malvertising campaign; the amount of infected impressions is exponentially higher.)
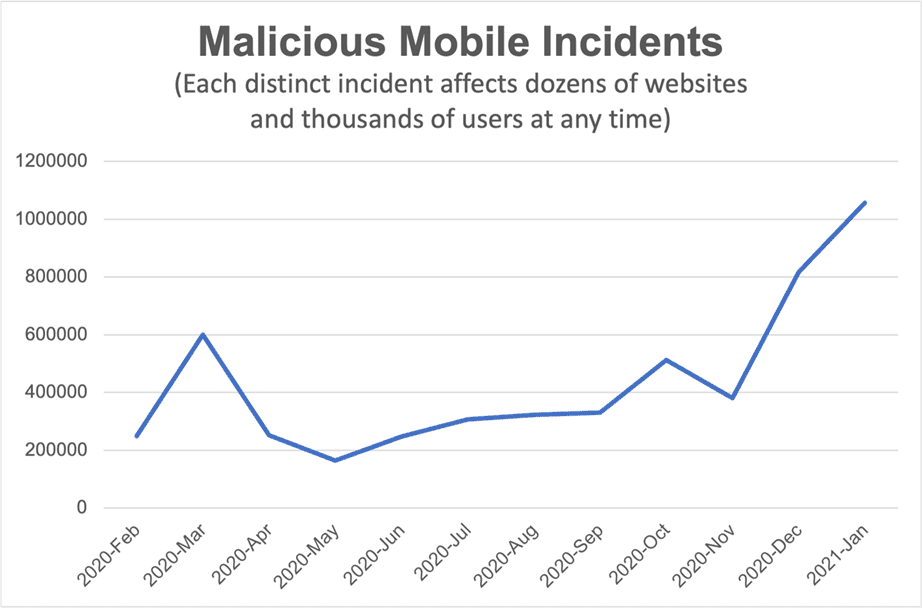
As Pat Ciavolella, Digital Security and Operations Director at The Media Trust, explained on a recent webinar, “Mobile is a juicy target for bad actors…. Most people access the Internet through their mobile devices and malvertising is harder to detect. Malicious actors are starting there to make sure their code is working before expanding onto desktop and reaching anyone and everyone.”
A significant slide in in-app programmatic CPMs—due to unidentifiable or unmeasurable traffic— will simply open up new testing grounds for malvertisers.
Double whammy
So, the enforcement of consent for IDFA—with Apple messaging that’s likely to dissuade users from opting in—couldn’t come at a worse time. As noted elsewhere, even rosy opt-in predictions could have devastating consequences on app developers’ revenue. We know because we’ve seen how advertisers pull out when users are unidentifiable and unmeasurable on Safari. (On mobile and desktop).
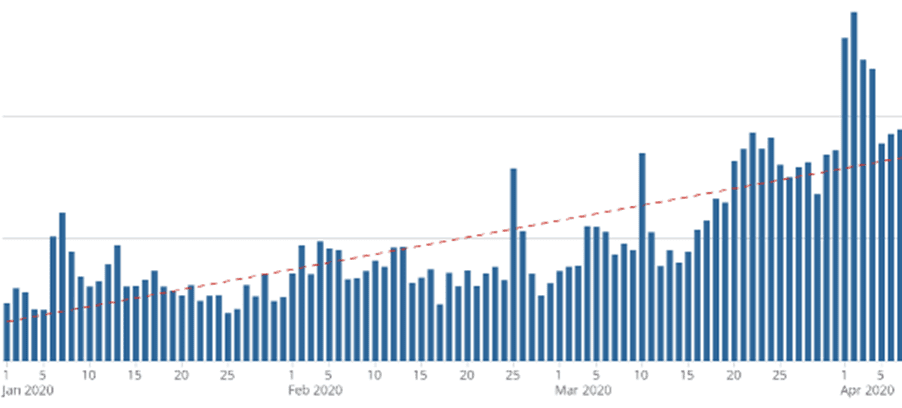
And when benign advertisers step back, we’ve then seen how the malevolent ones step forward. A simple examination of the rise in malicious advertising during the early days of the pandemic is enough to set your hair on end. An explosion in supply with lowered CPMs is a scammer’s paradise. The scam opportunities around Covid will once again hit fever pitch as bad actors try to capitalize on vaccine distribution.
App developers face a dual threat. First, the are likely to see a serious drop in revenue as in-app programmatic CPMs decline when users fail to opt-in to IDFA-sharing. And then a host of bad advertisers will try to infect their users with malware or rope them into some kind of scam.
As tempting as it may be to send the programmatic bid floors to the basement, app developers – and mobile publishers in general– have to keep their guards up against malvertising. The must also demand better protections from their upstream demand partners. It’s never been more important to scan and track where bad ads are coming from.
In the long run, infecting your users with malware or a credit card skimmer could have far worse ramifications than a revenue shortfall.



