Mobile users targeted to fingerprint devices for future attacks
Cloaking has become a favorite tool of malvertisers, and a new malvertising campaign highlights how the tactic is leveraged to ensure malicious delivery only executes for proper audiences. Using digital advertising to propagate, LuckyBoy-3PC is a heavily obfuscated, multistage, tag-based malvertising campaign targeting users on mobile and other connected devices.
Penetrating malware blocking tools, the attack has been confirmed on iOS, Android, and Xbox devices. First detected in early December, LuckyBoy quickly escalated to penetrate more than 10 smaller, primarily Europe-based Demand Side Platforms (DSP) with campaigns affecting U.S. and Canadian users. [Figure 1]
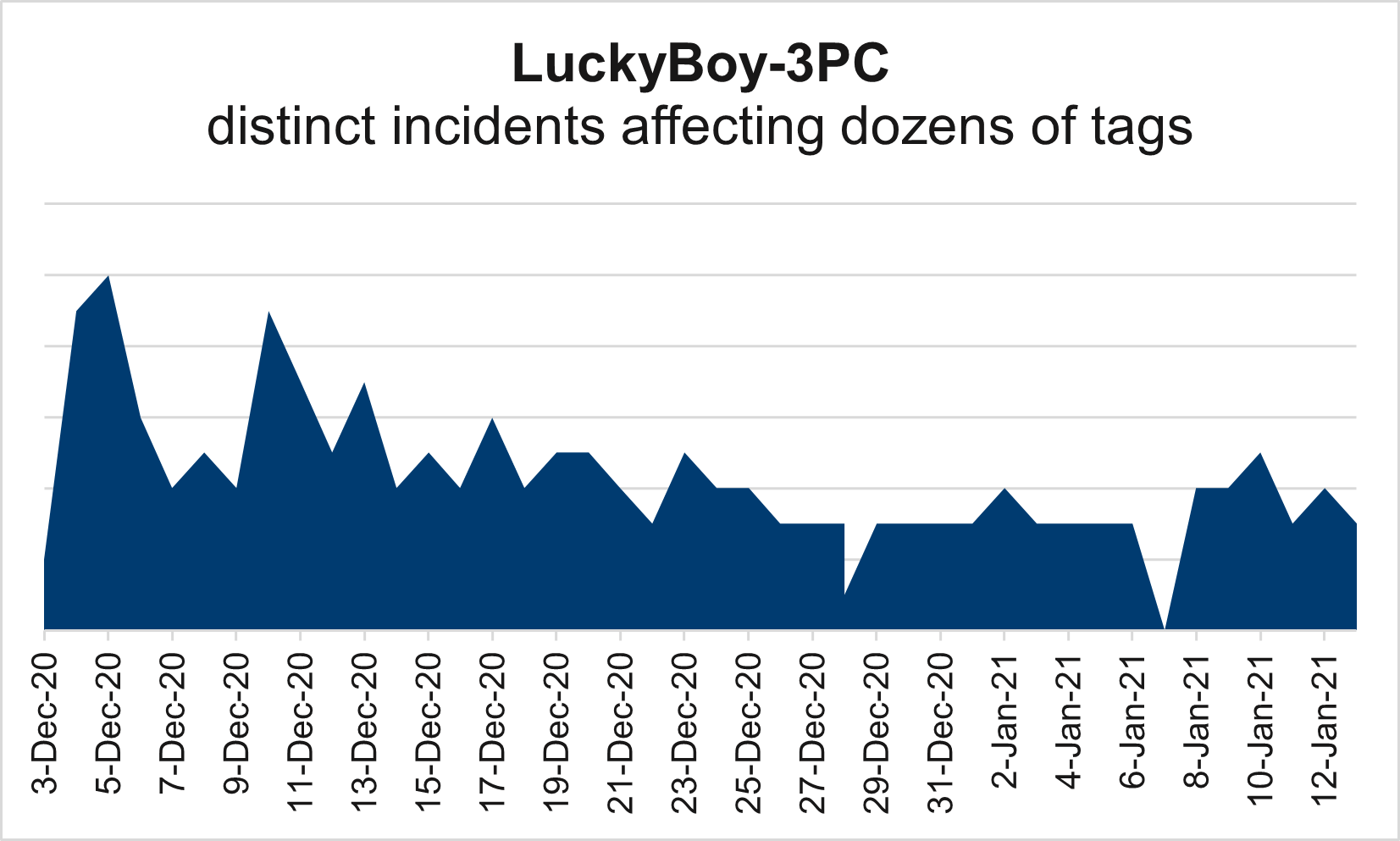
The malware uses multiple cloaking tactics that detect the presence of blockers, testing environments, and active debuggers. It ensures it’s not running while one of those features are activated by checking for a global variable with the value of “luckyboy”. When the correct environment is identified, the cloaked malware executes a tracking pixel and then redirects to malicious content—such as phishing content and fake software updates.
Sophisticated malvertising beats malware blockers
LuckyBoy operates in bursts, launching small campaigns with a few tags on Thursday nights and continuing through the weekend. Unlike Trickstack-3PC, the tags are compromised instead of the creative, and the malicious code is hosted by either tpc[.]googlesyndication[.]com or s0[.]2mdn[.]net.
Attesting to its unique character, it continuously conducts checks as it moves through stages; uses extensive code obfuscation and exclusion domains; and extracts device-specific information. The extracted information—including current domain, battery level, window size, plugins, country code, webdriver present, “touch-enabled” device, graphics information, number of CPU cores—is likely identifying devices for future attacks.
While The Media Trust has detected ad-delivered malware on Xbox in the past, this is the first time Xbox users have been affected in a significant manner.
Due to its pervasive and sophisticated nature The Media Trust is working with TAG Threat Exchange to shut it down across the affected parties.
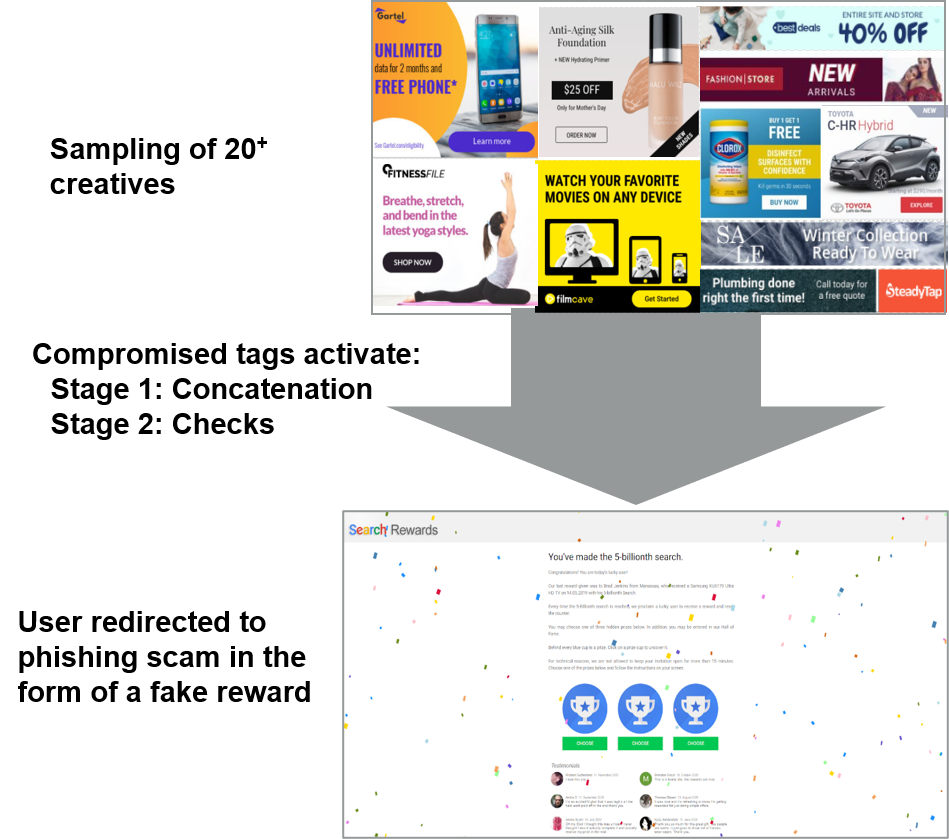
LuckyBoy-3PC: How it works
The heavily obfuscated code is delivered in two stages.
- Stage 1: Concatenates or links together 2,000+ base-64 encoded strings into one long string. This long string is then converted into ASCII code that is run in Stage 2.
- Stage 2: Using the JavaScript eval() function, the newly-created ASCII string checks:
- if the referrer URL contains malware-blocking domains,
- if it is running in a test environment, and
- if the domain is on a list of 940 publishers—a list defined in the obfuscated script.
When all checks are passed, the malware gathers device information and appends it to a URL based on one of the following domains to serve a fraudulent tracking pixel and then redirects to a malicious page (with phishing content):
- Impression Fraud: https[:]//furical-quipping[.]com, which redirects to the fraudulent tracking pixel https[:]//dailybreakingnews[.]today/impression[.]gif
- Phishing Redirect: http[:]//bestads[.]online, which then redirects to pointsprize[.]site, pointsprize[.]club or valuepoints[.]host
Below is a sample appended URL redirecting the user to a phishing-based redirect:
https[:]//furical-quipping[dot]com/340ec3fe-c167-4e94-b759-4feb2f7fcb20?d= [SITE_DOMAIN_APP_NAME]-&h=win32[-]3 cores[-]google inc.[-]google swiftshader &b=charging-100&p=3[-]Microsoft Edge PDF Plugin[-]Microsoft Edge PDF Viewer[-] NativeClient[-]&br=10&an=&sz=1920-1080-24&su=saa723aaa-[SOURCE_ID]-par;domain;dsp;cpu1;cpu2;gpu1;charging100%;plugin;ances2-[site_domain_app_name];untouchable;ok&sc=0-0-0[-][-][-][-]untouchable[-]5[-]en-US,en[-]no-webdriver[-]2[-]inIframe[-]uninit&td=[-][-][–][-][-]
In this example, extracted information associated with the user’s device confirms Microsoft Edge browser, non-touch screen, and battery level.
And the checks keep coming
Throughout the entire process, the ‘debugModel_Goodluck’ global variable is continuously checked to see if its value remains ‘luckyboy”. If it doesn’t, the script stops execution, serves a clean creative, and exits. This check is made numerous times during different sections of the malicious code.
When your luck runs out
LuckyBoy is likely executing tests, probing to gauge their success before launching a broader attack. Campaign was confirmed to execute on tags wrapped with malware blocking code, bypassing these defenses as further evidence that its sophistication is impressive.
While updating your exclusion list with the known domains will help, it won’t be too effective. The heavy obfuscation and multistage process means that the malicious domains won’t be read by your malware blocking appliance. Real-time, client-side scanning will help as it captures evolving threat patterns and signatures.
However, it’s best to terminate the buyer from the digital advertising ecosystem. That’s why The Media Trust is working directly with Google and TAG Threat Exchange to isolate the buyer and prohibit their ability to launch these malicious campaigns.

