StormMaize-3PC, a ROT13-enabled malware, disrupts dozens of brand websites to phish consumers
Notification popups wearing you down? It seems every time you visit a new site, you’re pressed to allow notifications—but those popups aren’t as innocuous as you may think. What’s the harm in allowing a website to show you notifications and keep you apprised of changes? Malware.
StormMaize-3PC is an evolving threat that targets brand websites to force an “allow notifications” popup that, if clicked, leads to the installation of backdoors or phishing—harmful tactics that can be used to execute future malware attacks. Leveraging the digital advertising ecosystem to drive consumers to these websites, the attack uses ciphers and performs a series of checks to evade detection.
The Media Trust initially detected this threat 18 months ago and notified clients and blocked its delivery to consumers. Since then, however, we’ve tracked its slow spread across more than 10 DSPs. What started with probing activity in late 2021 and again in 2022 has continued to escalate throughout 2023. [Figure 1]
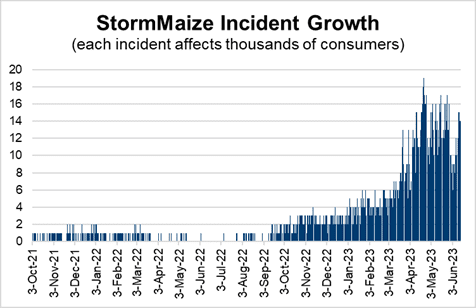
Figure 1: Dramatic growth in StormMaize incidents since initial detection in October 2021.
So far, this attack is 3x more likely to affect aging consumers than other age groups—likely the result of weaker cybersecurity instincts to avoid clicking the unknown and/or unnecessary.
Deciphering and Defining StormMaize
Similar to MudOrange-3PC, threat actors prey on content management system (CMS) vulnerabilities, typically via plugins. In this instance, several dozen WordPress websites have been compromised to force popups to appear over a brand’s website and initiate the delivery of more than 20 different malware payloads to unsuspecting consumers. While The Media Trust Digital Security & Operations team does not believe it is related to the current stripe payment gateway plugin flaw, they have not isolated these incidents to a specific plugin either.
StormMaize requires a compromised website which serves as a landing page for a digital advertising campaign. These websites are both legitimate brands and made-for-advertising (MFA) sites purely created to attract consumers and enable the malvertising process.
The compromised website is injected with a script that activates when a user accesses the page. [Figure 2] Using a ROT13 cypher, which converts the script letters into one that is 13 characters down in the alphabet (e.g., “a” in the code equals “n” in English, this malicious script performs a series of checks to verify a real user and determine device type.
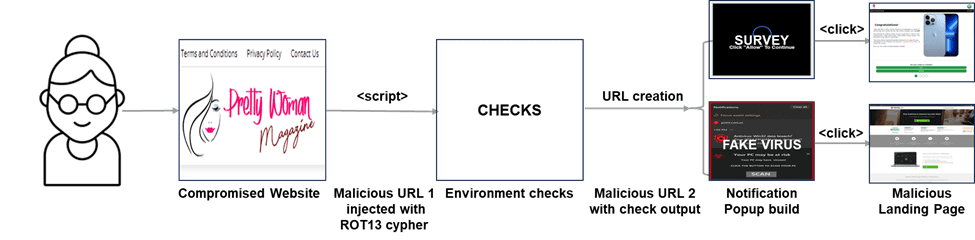
Figure 2: StormMaize flow from consumer click to malware delivery.
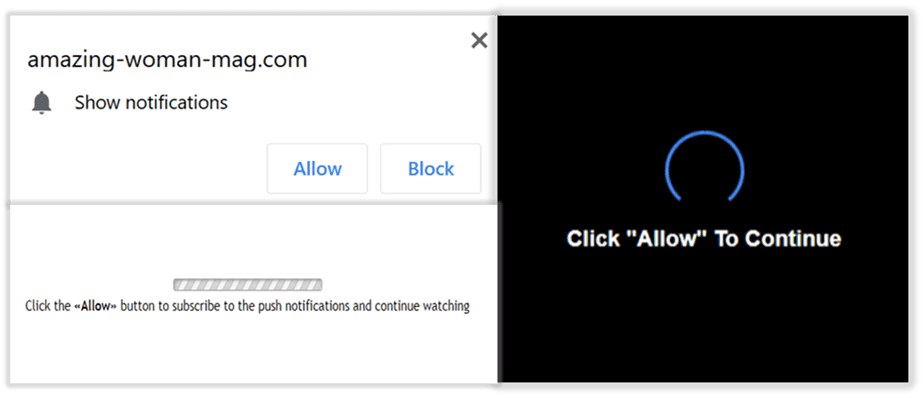
If the checks are passed, the user is then served one of several notification popups. [Figure 3]

Figure 3: Example of notification popups served to unsuspecting consumers
These malicious popups are typically fake virus alerts or surveys. If clicked, consumers are directed to one of two different landing pages that:
- Install backdoors: Prompt to download software onto devices which then root for additional vulnerabilities and make it susceptible to future attacks
- Phish: Request personal input by offering a free prize. The requested information is usually sensitive, e.g., physical address, credit card information, telephone number, etc.
Read about StormMaize in more detail
Unique Structure Enables Evasion
StormMaize uses a few characteristics that are not normally seen in malvertising schemes to evade detection and extend its life. First, it employs the above-mentioned ROT13 cipher, which is easy to decode but it masks the malicious string so it’s not immediately readable for domain-based creative blockers.
Second, StormMaize compromises a variety of domains across multiple industries. While many are legitimate, several are clearly MFA sites with cribbed or high-level content. Deeper analysis reveals that several sites mimic legitimate pages; however, the top-level domain references a different country—e.g., “.com.br” (bad) instead of “.com” (real). Or the top-level domain is purposefully misleading: e.g., “.UA” is a real website based in Ukraine, while “.AU” is a completely different website in Australia.
Third, the targeted websites exhibit an interesting pattern regarding the compromised status. Depending on the site, the compromise will disappear every 7-21 days, before reappearing. This is clearly an attempt to mislead website owners and security services into thinking the affected sites are clean
Thwarting notification popup malware
StormMaize-3PC, not only places consumers in harm’s way, but also it tarnishes the reputations of publishers and brands, and can cause acrimony between AdTech platforms and their downstream partners. With the ANA reporting that $13B-$20B is wasted on programmatic ad buys, protecting your digital ecosystem is a critical tactic to achieving revenue goals.
Thwarting notification popup malware schemes is not easy; however, there are a few basics for publishers and brands such as ensuring you keep plugins up-to-date and regularly applying the latest CMS security patches.
While you can add the payloads to your block list; however, StormMaize continues to evolve and introduce new payloads. To keep abreast of evolving threats, it’s best to continuously scan as a real consumer to elicit malicious behavior, track to the URL source, and notify your upstream partner.
It’s likely the attack stems from one or two buyers that have spread their campaigns across more than 10 DSPs. Scanning also keeps the landing page classification status updated so you can continue to earn when it’s clean and only block when it’s malicious.
Whatever path you choose, it’s important to keep the consumer experience in mind. In the long run, safeguarding their experience will yield benefits.
* Naming Convention Note: Phishing is represented by air-related themes. Color represents the gravity of the threat using the ROYGBIV scale, where red signifies major and violet signifies minor impact. 3PC refers to the use of third-party code to distribute the malware; in this instance, it involves two channels: a compromised CMS and the digital advertising ecosystem.



