Threat actors exploit CrowdStrike outage to deliver ad-based tech support scams and anti-virus scareware to vulnerable consumers.
It’s been less than a month since a problematic update to the CrowdStrike Falcon platform took down millions of Windows devices around the world, leading to flight cancellations and delays in the air travel industry and mass disruptions across healthcare, financial and retail sectors.
But while most organizations have since recovered from “the largest IT outage in history,” the fallout is still spreading—including malicious ad attacks targeting Windows users across desktop and mobile devices, hoping to exploit the chaos.
Bad Actors Smell Opportunity
It’s no secret that cybercriminals are opportunistic: they never let a good disaster go to waste, and the CrowdStrike outage is no exception.
Since July 19th, The Media Trust has observed a rise in fake tech support and antivirus (AV) pop-ups around the world appearing across trusted Web destination; targets include universities, large corporations and small governments across key geographical regions.
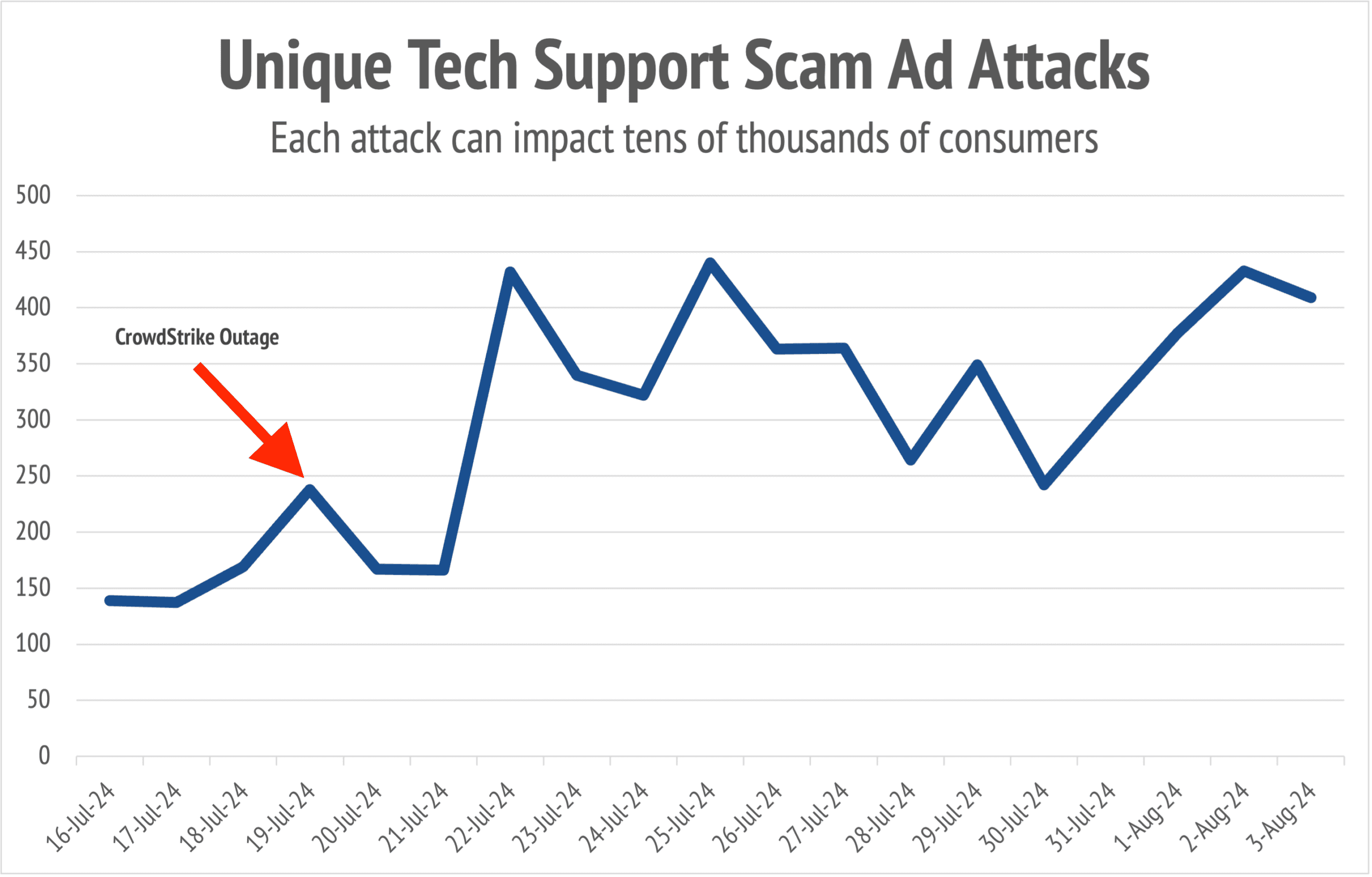
The Media Trust detected a massive surge in fake tech support attacks following the CrowdStrike Falcon update outage.
The timing of these incidents tracks with a notice from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warning consumers and corporations that threat actors were using the outage as a hook for social engineering and malware attacks.
The follow-up attacks mentioned by CISA and the Web-based attacks observed by The Media Trust are two-sides of the same coin: both seek targets who were likely to be affected by the CrowdStrike outage, and both exploit awareness of the incident as a way to attract engagement.
CISA Sends a Clear Warning
On July 19th, CISA published an advisory regarding the CrowdStrike outage and noted that “threat actors [are] taking advantage of this incident for phishing and other malicious activity”.
Over a series of updates published between the first day of the outage and July 26th, the agency observed:
- Attackers were sharing a malicious ZIP archive promising to help users recover from outages related to the CrowdStrike Falcon update.
- Some attacks were primarily concentrated in specific geographical regions, such as Latin America.
- Dozens of domains impersonating the CrowdStrike brand were created to gain the confidence of victims and deceive them into believing they were visiting an official CrowdStrike website.
CrowdStrike continues to monitor follow-up cyberattacks on its Counter Adversary Operations Blog. The latest update documents a spear-phishing attempt on a German company that utilized a fake Falcon Crash Reporter.
Web-Based Follow-Up Attacks
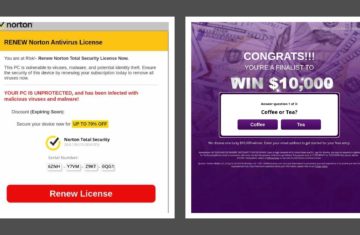
During the same time frame The Media Trust has tracked a rise in Web and Mobile-based attacks that follow a familiar format. For instance, the following advertisement—targeting businesses in France—is an instance of Dolos-3PC, the most prevalent method for delivering Tech Support scams to vulnerable consumers, including senior citizens. There has also been an uptick in fake AV popups, such as McAfee Security scareware.
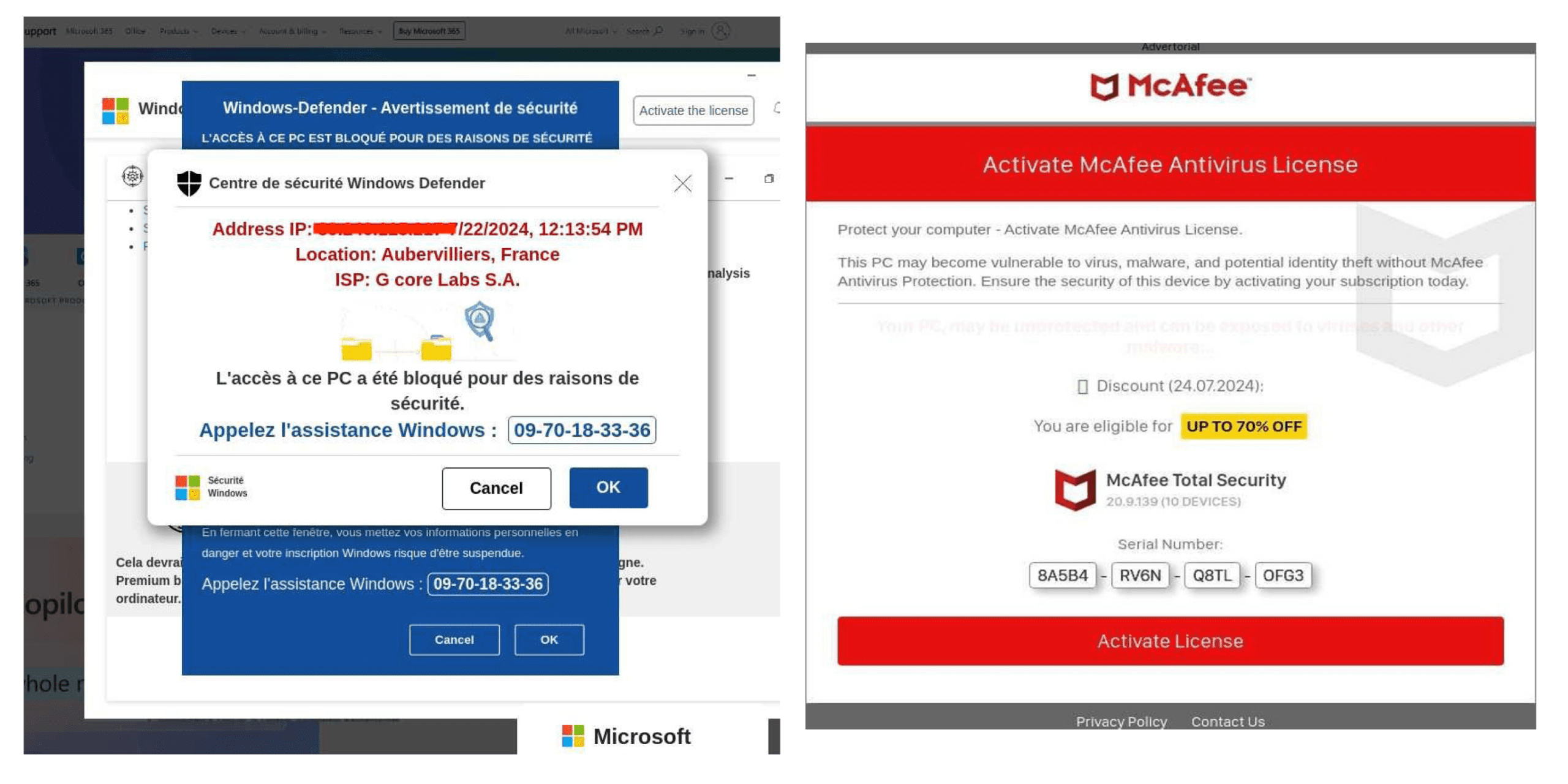
Redirects used by threat actors pushing fake tech support scams hijack brands like Microsoft and McAfee to fool vulnerable consumers into sharing personal data.
The uptick in these attack formats is easy to account for: in the aftermath of a headline-dominating IT outage, nothing could seem more natural than a call from your IT department, or an AV pop-up telling you there’s a problem with your system. That’s how cybercriminals think anyways, and so do many of their victims.
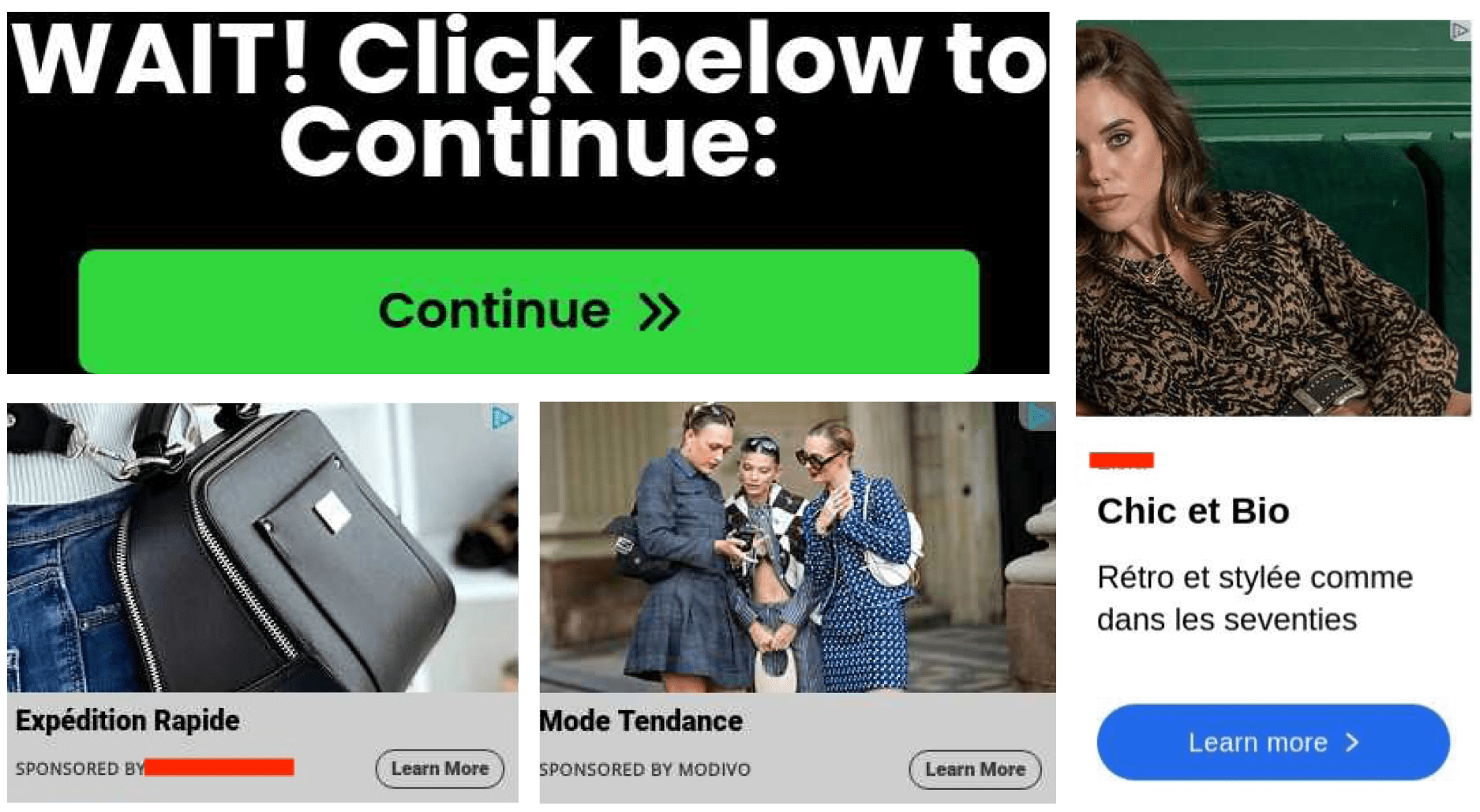
Innocuous creatives hide malicious redirects with tech support and other phishing scams. These are designed to pass buying platform audits.
Key Takeaways
Slowly but surely, follow-up attacks to the CrowdStrike outage are surely winding down, but malicious cyber actors are not—they are at work every day, and The Media Trust is constantly monitoring to protect businesses from being used as the delivery mechanism for their attacks.
For cyber professionals and victims alike, here are a few key facts to bear in mind:
- Digital attacks are highly targeted. today’s malicious actors aren’t throwing darts at a board until one hits the bullseye: the same technology behind targeted advertising enables cybercriminals to deliver a malicious ad or pop-up with the accuracy of a tactical strike. In the aftermath of a catastrophe, they will piggyback off organizations where an attack can do the most damage.
- Digital channels are overlooked. While CrowdStrike and CISA carefully documented follow-up attacks to the CrowdStrike outage, neither emphasized attacks occurring through Web or Mobile advertisements. Both focused on social engineering, phishing and malware campaigns targeting victims by email and phone. Meanwhile, organizations devote a lot of energy and attention to these attack vectors, but very little to the digital ecosystem.
- Digital channels provide a foothold for larger attacks. Cyber professionals often assume that malicious ads target individuals rather than organizations. But just like email, malicious ads provide a foothold for larger attacks impacting governments, corporations and other large institutions.
- Trusted brands lend legitimacy to malicious actors. In nearly every case of a web-based follow-up attack, we have seen attackers exploiting trusted names like Microsoft or McAfee to gain a victim’s trust and create a sense of legitimacy. This is all the more true in the aftermath of a disaster like the CrowdStrike outage.
Organizations who want to be perceived as safe and trustworthy can’t afford to ignore the activity of cyber actors who use their websites and apps as a weapon against customers. At The Media Trust, we work to help our customers take control of their digital assets and protect their customers—learn more today.