Consumers unknowingly install backdoors, lose money, and are subjected to continued attacks
It all started with a pop-up warning about a computer virus. Alarmed, Laurie’s aging father called the “technical support” number on the pop-up—soon enough his laptop was riddled with malware and his bank accounts had been drained of $27,000.
After buying a new laptop and spending countless hours arguing with the banks to recoup the money, Laurie’s father fell for the same scan again. It’s devastating to realize her elderly parents—and other at-risk groups—are easy prey for bad actors.
Even worse? Websites with household names, serving content to millions of people daily, are spreading these scams, putting the masses at risk.
Unfortunately, this scenario isn’t new or isolated. In fact, The Media Trust presented a real-world case at RSA 2020 with the U.S. Secret Service. Fake technical support scams have been around since the dawn of digital, but they started to diminish after the successful extradition and prosecution of a leading threat actor in 2018. However, these attacks rose to levels that hadn’t been seen since 2020. [Figure 1].
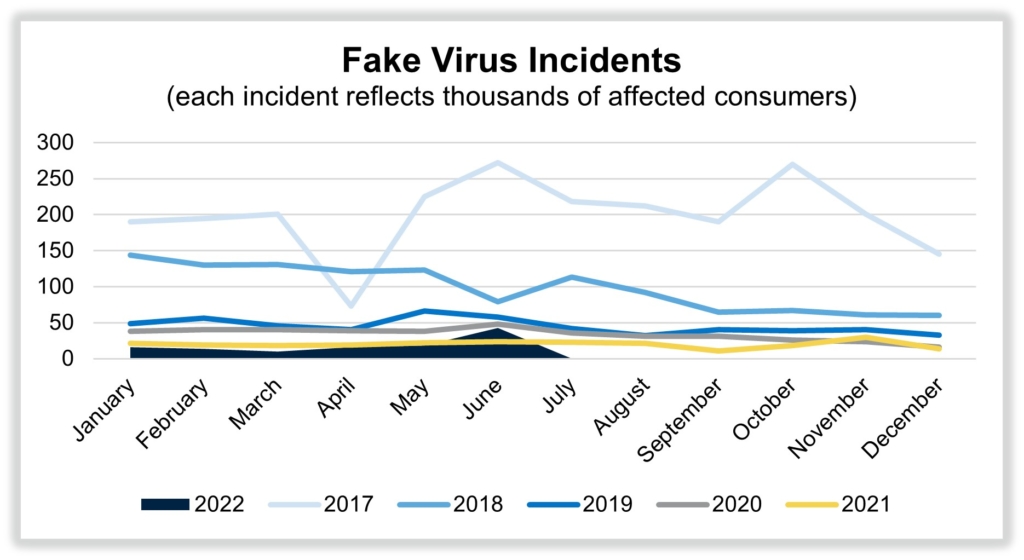
Figure 1: Volume of fake virus incidents from 2017-2022
Understanding a fake technical support attack
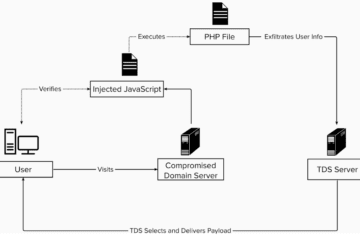
Consumers encounter malware through a variety of channels, not just email. Domains are the core element of digital malware as they host and/or enable the delivery of malicious content. [Figure 2]
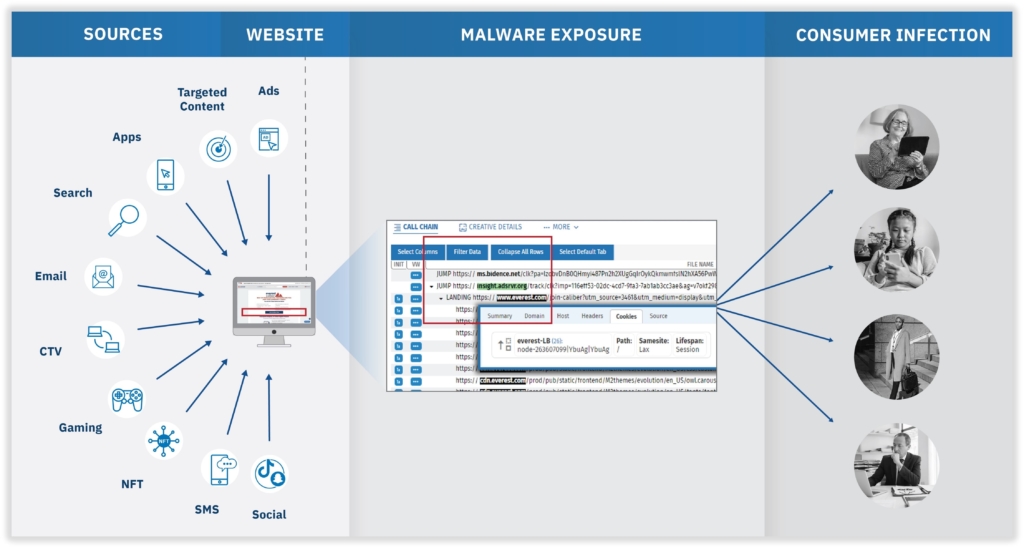
Figure 2: How consumers encounter malware
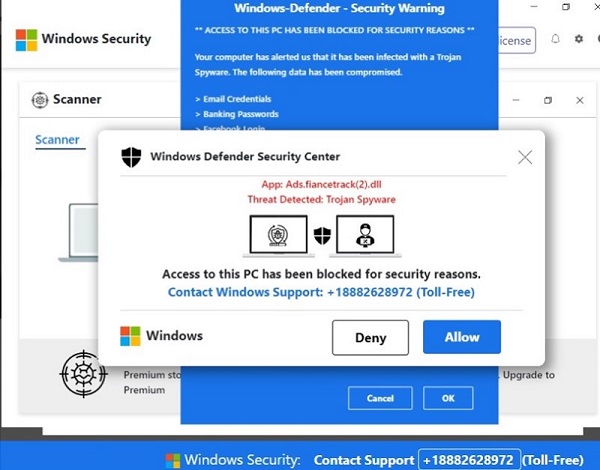
In fake technical support attacks, the user is presented with a series of popups (hosted on a domain) signaling device infection and directing them to contact the technical support number listed on the popups. Claiming to represent a well-known brand, the technical support individual offers to clean the machine remotely for a fee, and then uses this access to surreptitiously install backdoor programs for ongoing attacks. [For fun, check out Mark Rober’s YouTube channel on exacting revenge on scammer call centers.]
Targeted attacks? Not really. Contrary to other reports, we typically see these malicious activities affect consumers of all ages, across multiple geographies, accessing a range of news and entertainment websites. However, it’s important to note that the groups that tend to fall for these tricks are usually not technologically savvy, which may lead some to believe that targeting is involved.
The main goal of these fake virus and technical support malware campaigns is to infect a target device with malware. For connected environments, all it takes is one device (phone, desktop, laptop, gaming console, etc.) to become infected and the entire network is at risk.
Introducing Dolos-3PC
The uptick in the recent fake virus technical support scams are labeled Dolos-3PC due to the heavy use of cloaking in the digital advertising ecosystem and the stealth harm they cause to consumers. With at least 30 creative and landing page pairs and growing, these incidents use Windows operating system virus alerts to reach as many devices as possible (dominant operating system with ~75% market share).
Leveraging the digital advertising ecosystem as an attack vector, the bad actor places campaigns with creative images that encourage consumer engagement. Once clicked, the malware initiates a series of fake virus popups or uses a cloaking technique to redirect users that meet certain conditions to a compromised site. The end result is the same: a screen taken over by popups claiming a fake virus infection and directing the user to call technical support.
In addition to the coordinated volume of creative and landing pages, what makes Dolos interesting is the variety of cloaked landing page formats:
1. Fake: Blog-like pages are likely created for the campaign and contain minimal content, experience low site traffic, and are created and/or updated within days of each other
2. Generic: Sites have a more formal structure with navigation and contain seemingly more relevant information for the user.
3. Spoofed: Mimic the design, structure, and copy of legitimate brand websites.
More details on Dolos-3PC
Why technical support popups are on the rise
To increase the odds of success, bad actors are motivated to infect as many devices as possible, highlighting the fact that everyday web surfing can be dangerous for everyone. These efforts are being stymied by increased regulatory scrutiny, better detection, and successful prosecution.
The UK Online Safety Bill and recent FTC announcements highlight a focus on protecting consumers from online scams, which come in many shapes and sizes. In addition to cloaking landing pages to minimize detection, it’s likely that bad actors aim to avoid running afoul of regulations by distancing themselves from the actual harm. Instead of auto-downloads and subversive malware propagation, they are asking the consumers to install the malware themselves.
It remains to be seen if these tactics will shield bad actors. Regardless, it’s clear that all digital assets—websites, mobile, apps—need to defend against these types of threats that not only harm consumers financially and emotionally, but also provide an entry point to potential larger attacks on enterprise networks.
Ensuring digital trust and safety should be a priority for everyone.