This contributed article was originally published by Dark Reading on July 31, 2018.
Why website operators need to know with whom they are doing business and how to close the loop on third-party vulnerabilities.
In the digital world, a company’s website is a key touchpoint for its customers, but it also serves as an entry point for malicious actors. Thousands of websites operated by some of the world’s most recognized companies and government agencies have been compromised by malicious actors anxious to harvest web visitors’ CPU power for their mining operations. The root cause of these compromised websites in many cases is third-party code suppliers who usually have inadequate security and give access through a trusted connection to thousands of visitors of popular e-commerce sites.
The soaring number of cryptomining malware incidents reflects the growing interest in cryptomining itself. The most widely used tool is the Coinhive JavaScript for mining Monero digital currency, originally developed for website owners to make more money through mining. Immediately after Coinhive’s launch in late 2017, clones like Coinimp, deepMiner, Crypto-Loot, and Minr appeared in rapid succession to grab their share of a fast-growing market.
Today, cryptomining represents a new frontier for hackers to launch their attacks. One common hijacking method involves embedding cryptomining code under ad campaigns that appear on a webpage or run in a browser. Another involves the unauthorized installation of cryptomining code on a website. Regardless, whether victims browse the site or view the ad, the malicious code secretly harnesses the machine’s or device’s CPU power.
Cryptomining in Action
Recently, The Media Trust’s Digital Security & Operations (DSO) team sounded the alarm when they detected a spate of incidents involving:
1. A web analytics provider that we will refer to as “Webcount”
2. A popular car research aggregator, referenced as “Carsearch”
While the team spotted a few incidents of cryptomining malware in the past, more recent incidents are different because they involve more sophisticated campaigns using the digital supply chain as a distribution channel to target brands trusted by consumers and businesses
In the “Webcount” case, the DSO team identified the cryptomining code while scanning client websites for unauthorized code. Associated with a well-known file extension, the anomalous code was seen on every client website running the Webcount analytics. The same file extension coincided with previous Coinhive incidents identified and thwarted by the DSO team. The cryptojacking malware developers made no effort to obfuscate the malicious code. On the contrary, they avoided antivirus detection by using legitimate code throughout the entire file. Once the code made a call to a malicious domain never before seen in any major domain or IP verification analysis, the DSO team alerted the client and terminated the malware’s source.
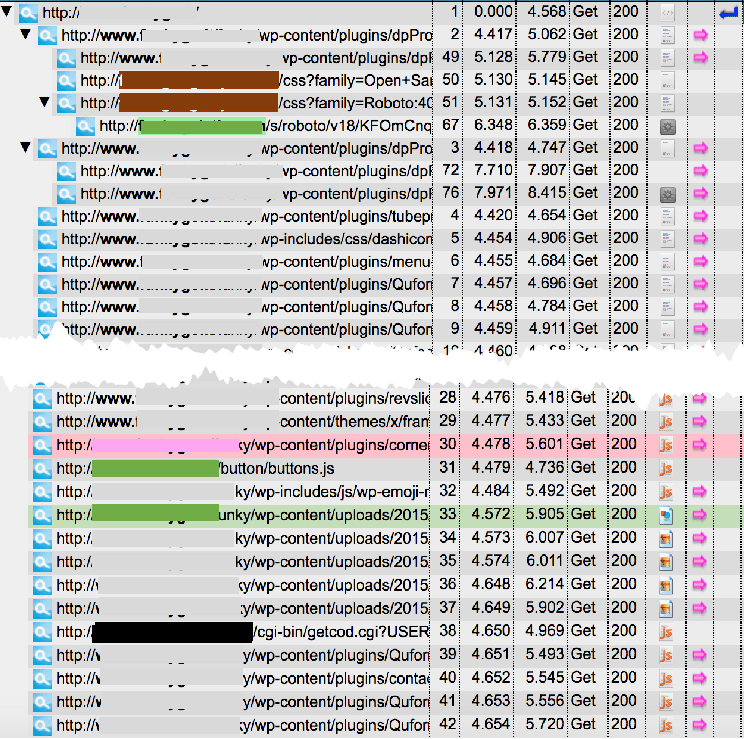
Figure 1 shows how the Webcount cryptojacker works. A web user visits a restaurant website that runs the compromised Webcount analytics. Line two starts the homepage’s creative elements being combined to render the page. Line 38 makes the JavaScript URL call to the Webcount site, which is followed by a call to the malicious domain. Several calls are made from this domain to malicious JavaScript files that take over the user’s browser and initiate the cryptomining process. Instances involving the Webcount cryptojacker are distinct by their higher-than-average number of domain calls. The cryptojacker runs for as long as the user is on the restaurant’s site. It is worth noting that while Webcount analytics are widely used, Webcount’s web servers previously have fallen victim to hackers. This poor track record highlights the importance of closely monitoring the activities — authorized and otherwise — of third parties used in the highly dynamic digital environment.
Figure 1
Image Source: The Media Trust
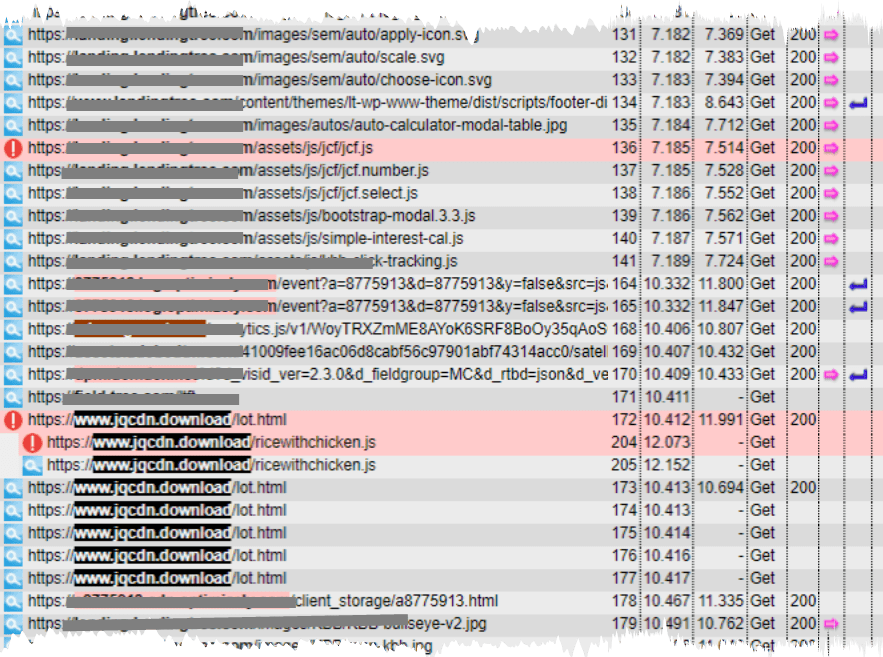
The “Carsearch” incident involves the same Coinhive code but uses a slightly different attack method. (See Figure 2 below). When users browse through the Carsearch website, they are led to “CarloansRUs” to learn more about their financing options. As users visit the CarloansRUs pages and meet key conditions, such as location, browser, time of day, screen size, etc. (line 204), CarloansRUs serves a malicious JavaScript file. Line 205 shows repeated attempts to verify conditions. The code calls to a known malicious domain, “jqcdn.download,” which then launches an attack on the users’ browsers (line 136). Line 172 shows the point where the attack begins.
Figure 2
Image Source: The Media Trust
Webcount and CarloansRUs are ideal attack vectors because they give access to a large number of site visitors who will linger on the sites and give hackers enough time to mine for cryptocurrencies.
How to Avoid Cryptojacking
Websites depend on the support of third-party code providers. A typical commercial website has an average of 100 third parties supporting its various features, such as analytics, content management systems, customer recognition platforms, social widgets, and more. Third parties account for anywhere between 50% to 95% of website code execution. In effect, more than half of all code on a website lies outside a company’s direct control. To further complicate matters, the inventory of third parties can change each day.
The Webcount and CarloansRUs cases demonstrate why website operators need to know with whom they are doing business and how to close the loop on third-party vulnerabilities related to analytics, data management, customer identification, chat, image library, and widgets. Companies must create and implement an in-depth digital vendor risk management strategy to identify and decrease the potential security risk associated with third-party vendors. Today’s digital environment requires vendor management strategies that are able to adapt to the ever-changing nature of digital assets and provide compliance with a myriad of new digital privacy regulations.