Super sophisticated phishing redirector marks a frightening evolution in malvertising.
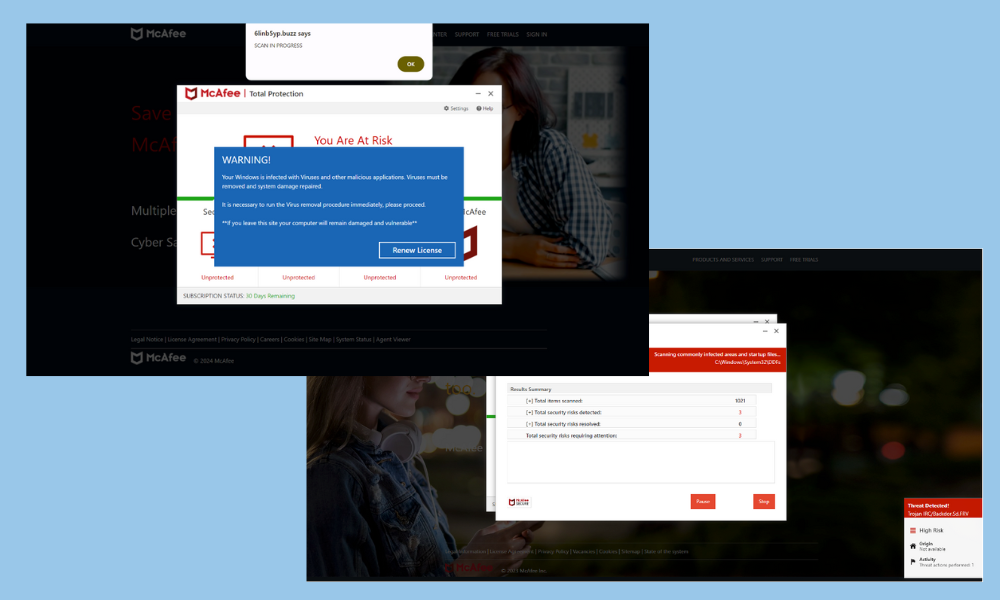
Unlike the Grinch trying to steal holiday cheer, threats actors have set about spoiling the season with an incredible barrage of unwanted presents. For the past several months, The Media Trust has been battling StringRipper, a fierce evolving malicious campaign forcing redirects and delivering phishing attacks via scareware.
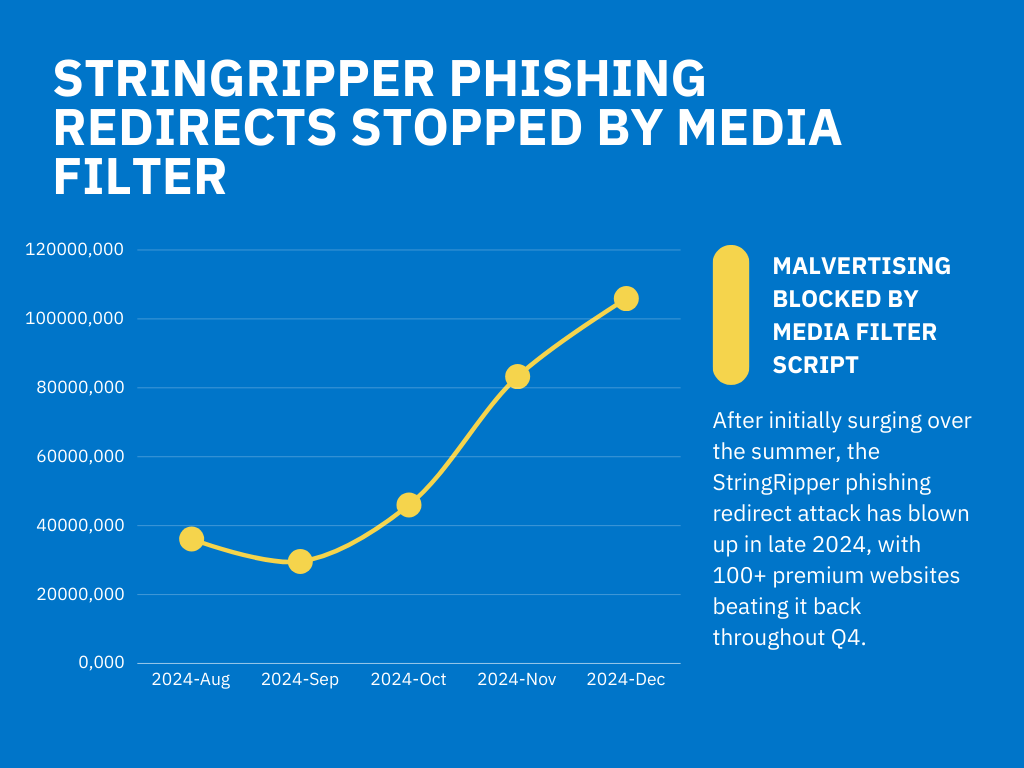
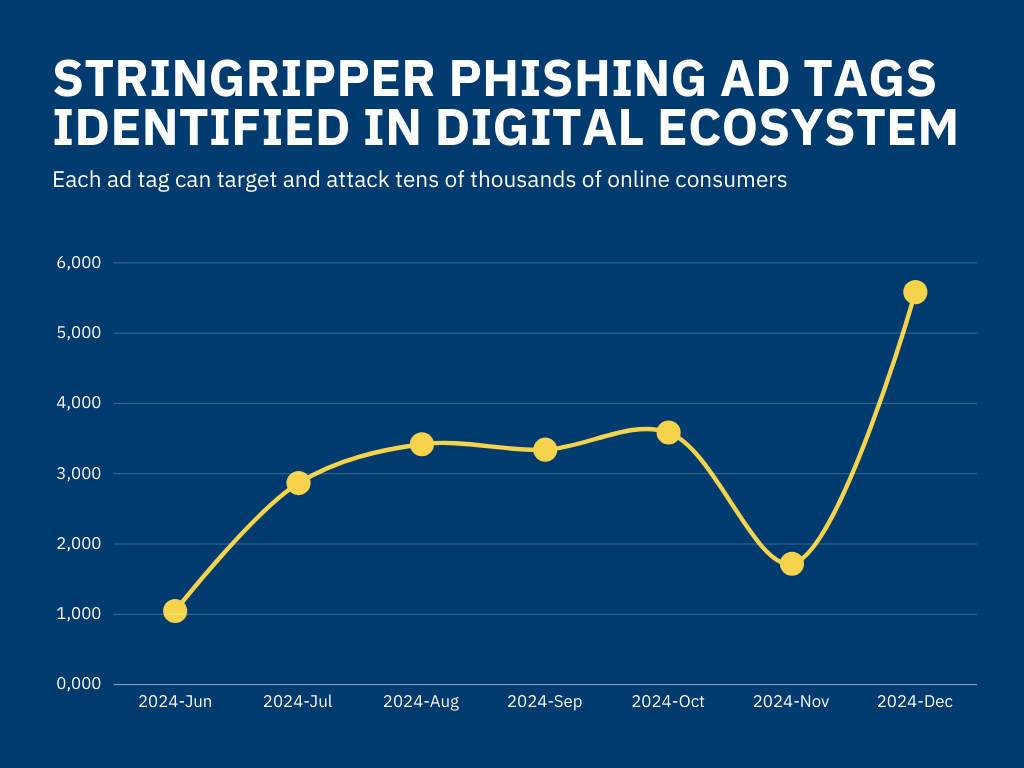
To illuminate how fast this StringRipper is growing, the amount of phishing redirects prevented by real-time ad-blocking script Media Filter in the first half of December is 30% higher than the entire month of November. The number of infected ad tags neutralized across the internet is twice as much as when StringRipper was first identified in the summer.
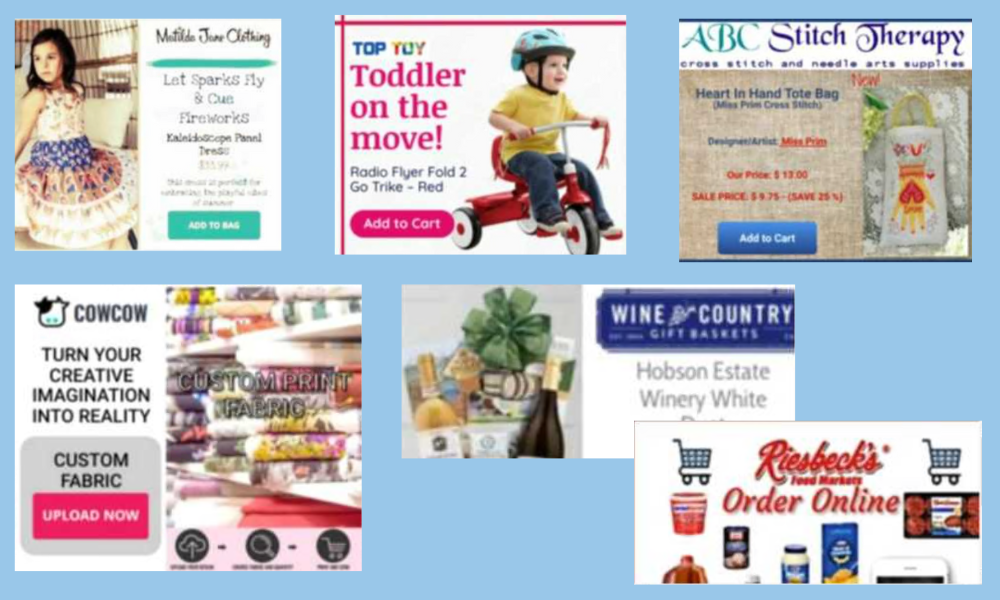
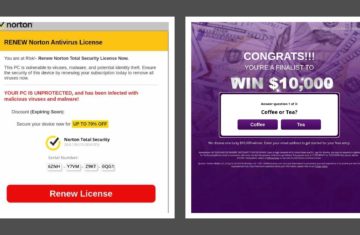
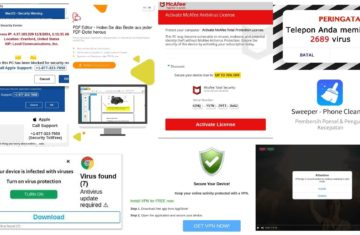
Equally worrisome is StringRipper’s sophisticated attack, which is ad-tag based and exploits legitimate advertisers. Unlike attacks that hijack advertiser landing pages to distribute malware, StringRipper takes advantage of existing, legitimate ad campaigns by infecting their associated ad tags. Threat actors leverage the reputations and credibility of major advertisers to bypass buying platform/DSPcreative audits. Many of these ads appear perfectly benign even under mild scrutiny—below are just a few examples of creatives for legitimate businesses that were unknowingly hijacked by StringRipper.
The infected ad tag contains a small section of obfuscated code, which acts as a discrete launcher for the real payloads that are called externally. Using external hosted payloads allows attackers to keep their signature to a minimum—like a tiny incision by scalpel in the body of the ad tag code.
But StringRipper also leverages advanced obfuscation and a multi-stage process to conceal itself within infected ad tags. It employs a novel approach to redirection, which combines dynamic function creation with randomized timing. This allows StringRipper to closely mimic legitimate user interactions, making it increasingly challenging for automated systems to identify its behavior as malicious. The malware is constantly fingerprinting its environment and listening for user signals (e.g., scrolling) to ensure it’s attacking target consumers and avoiding audits or security checks.
The combination of these techniques—obfuscation, dynamic function creation, and randomized timing—represents a significant evolution in malware sophistication. StringRipper underscores the ongoing cat-and-mouse game between cybercriminals and security professionals, and highlights heightened vigilance and advanced detection methods in the digital advertising ecosystem. In addition, StringRipper further highlights the impact of malvertising on legit advertisers—it’s a new kind of brand safety problem.
The Media Trust’s Digital Security and Operations team has assembled an in-depth report on StringRipper’s complicated execution. To avoid spreading valuable information to malicious parties, it is only available by request and with a verified email. (You must submit a company email to receive the report.)