Highly effective compromised landing page scheme seems legit enough to fool consumers and infect their devices.
SocGholish, a sophisticated malware family well known for its deceptive tactics and driveby download execution, is no new kid on the block when it comes making digital consumers miserable. Also known as “FakeUpdate” malware, It’s been a regular plague delivered via malicious emails, search results, and search marketing for a decade at least—it regularly tops the Multi-State Information Sharing and Analysis Center’s (MS-ISAC) of most prevalent malware.
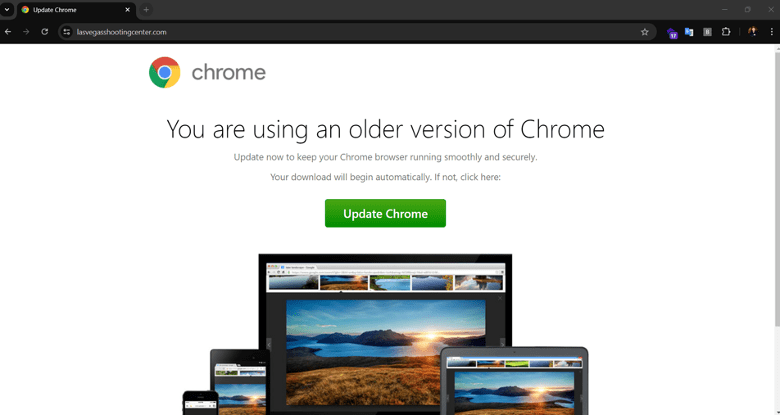
But it’s only in 2024 that SocGholish has become a massive thorn in the side of digital display and native advertising channels, with a stunning 22X growth in hits in the last six months alone. By exploiting CMS vulnerabilities to inject JavaScript into legitimate websites, threat actors are leveraging credible advertisers to spread SocGholish’s malicious creatives. If a consumer’s device meets certain criteria, a compromised site presents them with a fake prompt to update software such as Google Chrome or Microsoft Teams.
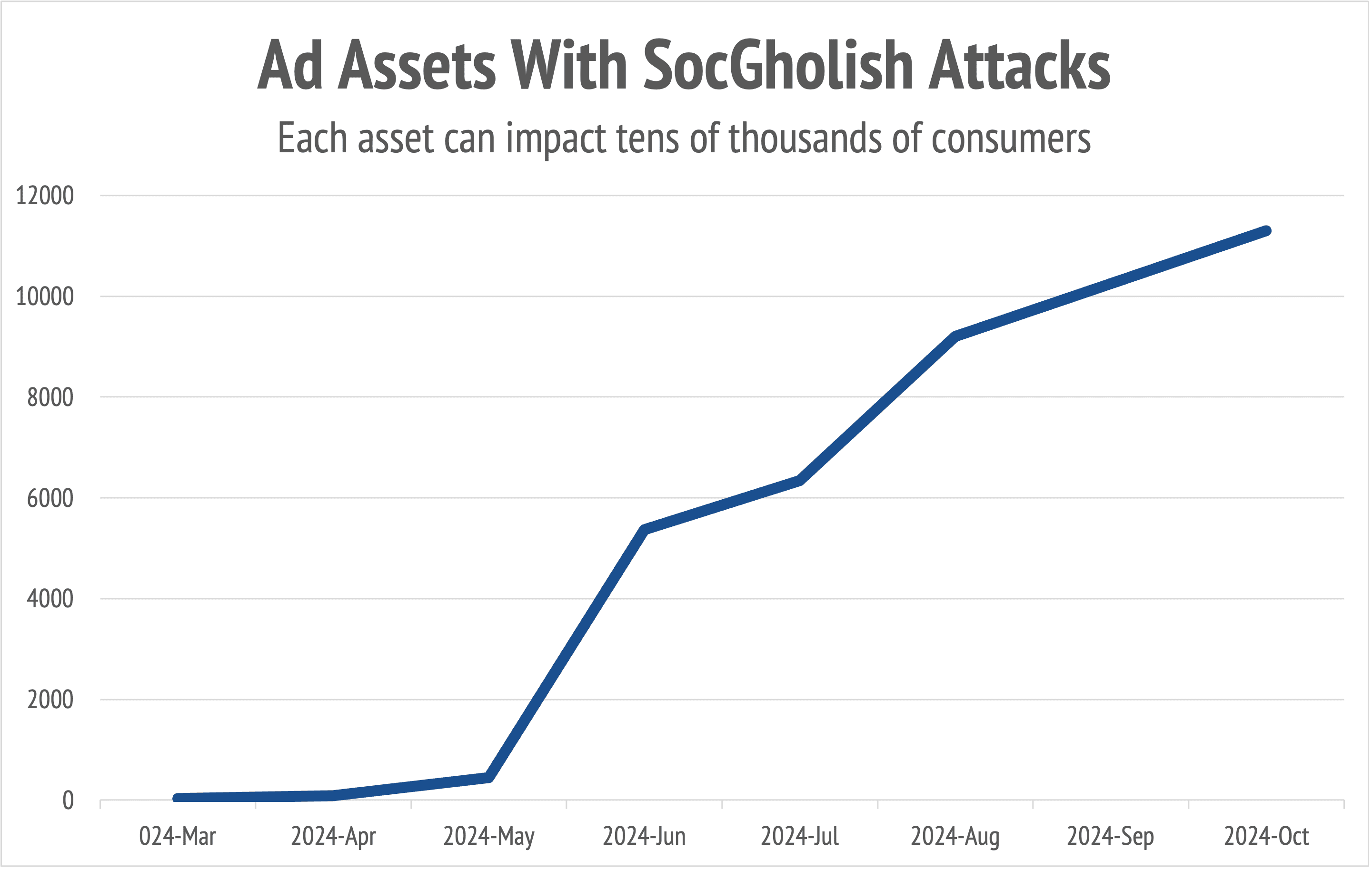
Advertising assets linking to pages containing the SocGholish driveby download attack have skyrocketed within the last six months.
Consumers electing to initiate this “update” unknowingly establish a command-and-control connection to the threat actor, who then has the freedom to unleash the final payloads: e.g., data exfiltration, remote access trojans, and ransomware.
The worst part: because SocGholish imitates software update notifications in such an uncanny fashion, consumers are more likely to be fooled and allow themselves to become prey for more devastating attacks that could impact their families, their employers, and more. And it all starts with a display ad tied to a compromised landing page.
Anatomy of an Attack
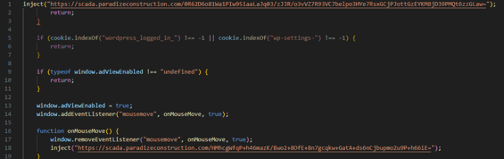
The vast majority of sites compromised to deliver SocGholish were infiltrated through vulnerable WordPress plugins, such as those for SEO optimization or easy site building. Each of these plugins have documented Stored Cross-Site Scripting (SXSS) vulnerabilities that allow attackers to inject a malicious dns-prefetch link. (Figure 1) in addition to malicious HTML script tags onto the site. (Figure 2) The two most common script tags seen, “jquery-init-custom-script-js” and “fop_custom_script-js”, contain a malicious URL call that fires under specific circumstances, (Figure 3) prompting the site to display the fake software update within an iframe. (Figure 4)
The first sign of compromise that a curious observer might notice is a suspicious DNS prefetch nestled among the others. This line of code is using the HTML <link> element with the rel=’dns-prefetch’ attribute to instruct the browser to perform DNS prefetching for the domain frontendcodingtips.com; this is a browser technique that resolves a website’s IP address before a user clicks on its link.
This strategy is used by attackers to perform inconspicuous data collection, since their browsers will automatically perform a DNS lookup for the attackers domain without the users’ knowledge or consent. This unsolicited DNS lookup could provide valuable info including IP addresses of visitors, approximate geographic locations, or the times when the compromised site is most frequently visited. Since this is just a DNS prefetch and not an actual resource load, it’s less likely to be noticed by casual inspection or some security tools that focus on loaded resources.
The domains outlined in Figure 2, apieventemitter<.>com and responsiveuikit<.>com, are two indicator of compromise (IOC) domains which have been injected into the site by exploiting a vulnerable plugin via Cross-Site Scripting (XSS). Vulnerable or outdated WordPress plugins susceptible to XSS attacks are the primary attack vectors malicious actors target for initial compromising which is further detailed below. These URLs contain a malicious script that initiates the first infection stage if specific criteria is met. Figure 3 is a deobfuscated version of the malicious script called by the URLs seen in Figure 2.
This code calls the URL, paradizeconstruction<.>com, which injects a malicious iframe that takes the form of the fake software update. An iframe is used to embed another document within the current HTML document. This can be thought as visiting a website within another website. The danger here lies in that the user is not redirected to another URL, but has their current page essentially replaced with other content—in this case a fake software update. This can deceive users into believing the update is legitimate as the URL displayed in their address bar has not been altered or replaced.
In this scenario, an iframe is loaded onto the compromised page, displaying a prompt to update to a newer version of Google Chrome. When the user clicks the “Update Chrome” button, they download a malicious zip file containing a script typically named “AutoUpdater<.>js” or “Update<.>js” (Figure 5). Upon execution, this script communicates with a command-and-control server, allowing final payloads to be delivered to the device.
The update.js file, upon initial activation, proceeds through three main stages to infect a computer. First, it downloads and installs a legitimate software tool from a trusted website, a clever move designed to avoid raising suspicion, as it appears to be a common program that many users utilize. Next, the malware deploys its own malicious code, disguising it as a regular file on the computer.
Finally, it creates an automatic task within the system, scheduled to run regularly. This task blends in with normal computer processes, making it difficult to detect and obscuring the connection to the attacker’s control center. This sophisticated approach demonstrates how malware is evolving, using trusted sources and common system functions to evade detection by security professionals. It’s like a burglar who not only picks the lock but also poses as a regular houseguest to avoid suspicion.
Pervasive By Nature
Currently, SocGholish is recognized as one of the most prevalent and observed malwares threats. In Q4 2023, the Multi-State Information Sharing and Analysis Center (MS-ISAC) reported that SocGholish accounted for 60% of the top 10 malware incidents, with Arechclient2 being the second highest at 9%.
Given the nature of how SocGholish infects a user, we expect these trends to continue into 2025 and the future. Currently there is no defined pattern to indicate the likelihood of one site being targeted over another based on industry.
That said, we did discover a shared trait across the vast majority of the SocGholish compromised sites. Our review of compromised sites found they were utilizing outdated versions of the popular WordPress Search Engine Optimization (SEO) plugins Yoast and Rank Math PRO. Older versions of these plugins have documented SXSS vulnerabilities due to lack of proper input sanitization which we believe to be the initial infection vector. Below are additional links to CVE.org that provide additional information regarding the severity and impact of these vulnerabilities.
- Yoast SEO: CVE-2024-4984
- Rank Math SEO: CVE-2024-3665
On July 9th, 2024, CVE.org published a newly discovered vulnerability for the WordPress site building plugin, Elementor, stating a directory travel vulnerability allowing for XSS/SXSS attacks on the platform. At the time of writing, Elementor version 3.22.1 and all previous versions are currently susceptible to this vulnerability.
- Elementor: CVE-2024-37437
Publisher and User Impact
For companies in the programmatic advertising industry, the presence of SocGholish on landing pages poses a severe threat. Compromised landing pages can lead to:
- User Trust Erosion: Users who encounter malware through advertised links may lose trust in the platform, leading to decreased engagement and potential loss of revenue.
- Reputational Damage: Associations with malware can tarnish a company’s reputation, making it harder to attract and retain advertisers and users.
- Financial Losses: The costs associated with mitigating malware infections, including system recovery and legal liabilities, can be substantial on top of potential revenue loss.
Infections like SocGholish are often highly targeted and will only deliver malicious payloads to specific devices, geos, or audience profiles, making them difficult to identify and remediate before they impact consumers. Rotating device and audience profiles can unearth these threats before they attack potential customers—or stall out a time-sensitive advertising campaigns.
Take Action
The Media Trust recommends taking a few basic steps to identify and prevent this malware from compromising your environment. These methods are just as effective for digital media publishers as brands of all sizes—especially advertisers—with consumer-facing websites.
First, consider leveraging a security monitoring service that leverages client-side scanning. Infections like SocGholish are often highly targeted and will only deliver malicious payloads to specific devices, geos, or audience profiles, making them difficult to identify and remediate before they impact consumers. Rotating device and audience profiles can unearth these threats before they attack potential customers—or stall out a time-sensitive advertising campaigns.
Next, if you are an administrator or owner that suspects your site may be compromised, review the HTML to see if malicious code has been injected into the site. If present, remove the offending code and ensure all plugins are using the latest version. In some instances where vulnerabilities are still present, even in the latest version of a theme or plugin, it may be necessary to remove it and also delete anything that is not recognized or is no longer in use.
In addition, administrators can set up supplemental measures including input sanitization and content security policies, which are an effective means of preventing these sorts of cross-site scripting attacks.
For end-users, if presented with a redirect or a popup claiming that a piece of software you engage with requires an update, close out the tab immediately and disregard the message. If you are unsure if your software is currently up-to-date go directly to the developer’s website and check if you’re running the latest version.