
Mobile-specific malvertising campaign targets devices in motion and explodes its reach in four weeks among Demand Side Platforms
Malvertisers have deployed a unique twist on their campaigns that involves multiple checks and redirects to deploy phishing content to unassuming users. Detected and tracked by The Media Trust’s Digital Security Operations team since January, this campaign used dozens of domains to target mobile-web users, tripling its reach in four weeks.
The campaign was isolated to seven—several well-known—Demand Side Platforms and The Media Trust worked quickly to stop its propagation to the broader digital advertising ecosystem. To date, the campaign has not affected our media publisher clients.
How it works
The campaign followed a unique pattern that proved difficult to decipher. In an effort to obfuscate the malicious intent, the campaign involves the injection of JavaScript into digital advertising code to verify the:
- Mobile device is in motion by checking for changes to its longitude/latitude coordinates, acceleration and gravity
- Creative is in a live environment and not just from a synthetic ad tag scan
If both conditions are met, the same JavaScript creates and injects the malicious element (i.e., velvetvacation[.]com) onto a publisher’s page. It then redirects (i.e., to toparticlehub[.]com), hijacks the browser session, and changes the page address.

For campaign tracking purposes and ensuring the redirect has occurred, the domain sends information regarding the Demand Side Platform, publisher domain and campaign ID to the command and control server and, finally, serves the user a phishing landing page.
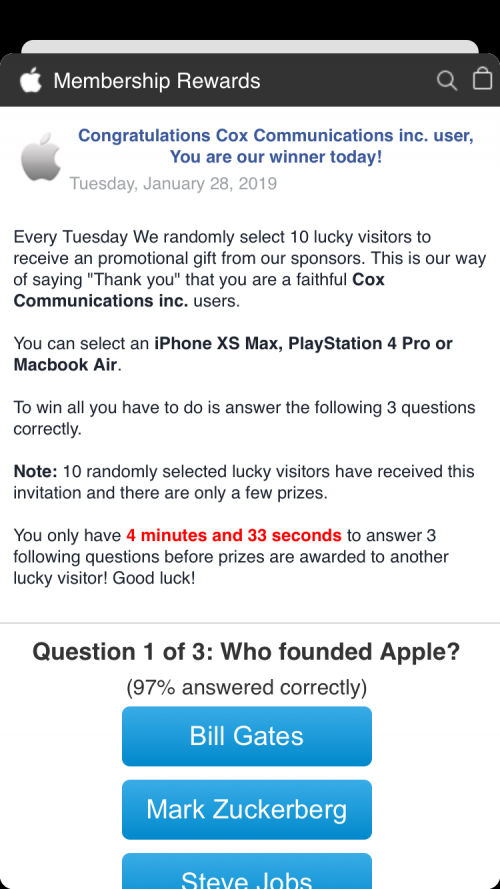
In an additional final attempt to appear legitimate and ensure execution on a mobile device, the landing page performs additional checks to determine the ISP, mobile device model, and display the applicable message to the readers. If the reader is on an iPhone, the content served would be related to Apple. While these examples are for Apple devices there’s nothing in the code pattern to indicate that Android devices are safe from this attack. To further remove their tracks, the final action removes the event listening code.
How you can protect your digital advertising ecosystem
Continuous scanning and analysis helped catch Vertigo-3PC due to its sophisticated and multi-stage operation. The Media Trust’s Digital Security and Operations team leveraged one scan’s results to identify additional code signatures and hunt for related malicious campaigns. Once confirmed, the indicators of compromise are automatically added to our blocklist which feeds Media Filter, our malware blocking solution for media publishers.
Vertigo-3PC is another example of how continuous, client-side scanning identifies highly obfuscated malware and quickly refreshes our malware blocking list.



