Campaign targets UK publications to take advantage of increased readership volume during the UK Election period.
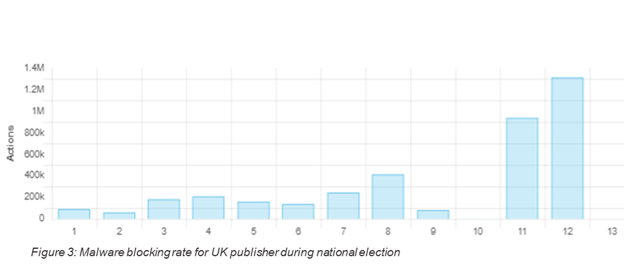
Elections have never given media publishers as many headaches as they do now. The Media Trust’s Digital Security and Operations (DSO) team detected malicious ads phishing for consumer personal data on at least 20 UK-based publications in the weeks leading up to the UK national election on December 12. Malvertising, the compromise of third-party digital code propagated through the digital advertising ecosystem, peaks during periods of high online volume. The UK national election is proving to be a perfect forum for malvertising, triggering a 300% increase in malware blocks on one UK-based publisher alone.
When Scanning and Blocking Collaborate
For unsuspecting online readers, “when it rains, it pours” as bad actors ride on a large-scale human event to wreak havoc on the digital advertising ecosystem. In this instance, they launched their attack by placing fraudulent sweepstakes popups through an ad platform that connects smaller technology providers. The popups were hosted on the simple-to-go[.]com domain (figure 1).
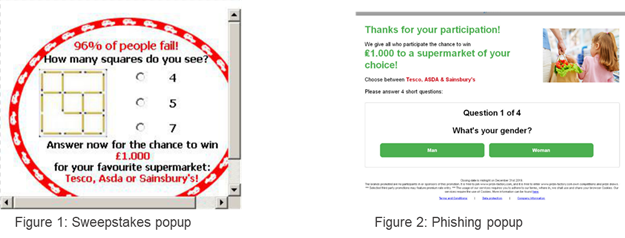
Users who clicked were redirected to yet another popup that asked for their personal information: gender, age, and thoughts on supermarket pricing and value (figure 2).
Created in 2018, the simple-to-go[.]com domain was first detected by The Media Trust on September 4 of this year. In-depth analysis revealed un-authorized phishing as its main objective, and the DSO blocklisted the malware. Over the past few months the DSO alerted more than 50 US and UK publisher clients and several prominent digital technology partners of the domain’s more than 2,000 attempted attacks.
This past week, the number of attacks doubled, in particular among UK publishers that drew larger audiences with national election. One UK publisher experienced a 300% increase in its malware blocking efforts (figure 3).
Malvertising: Devil is in the Details
At first blush, this campaign may not appear to be malicious. It is trafficked through a valid advertising platform and doesn’t harm the user’s device. In fact, the domain isn’t flagged by VirusTotal and only one security provider flagged its sister domain (the actual campaign website) prize-factory[.]com. However, these types of sweepstakes promotions rarely, if ever, offer the user a valid chance to win. In this instance the user is dumped to an invalid page after answering the four questions. The personal information is collected and used to re-target individuals in future advertising campaigns. Not only does the campaign present a poor user experience, it also exposes the publisher to potential violations of data privacy regulations.
Malware attacks are escalating around the world, targeting digital assets with high traffic as well as critical infrastructure like power grids, healthcare, and elections. The key to thwarting these attacks before they harness your digital environment to amplify their reach is to continuously scan your website and mobile apps for unauthorized code and then blocking its execution.

