Hotel websites are vulnerable to malware and data leakage
The hotel industry is poised for continued growth in 2015, coming off a stellar 2014 which saw occupancy rise to levels not seen in more than 20 years. With the World Tourism Organization projecting more than 1.4 billion international journeys in the year 2020, you can bet that hotel websites will play a central role in fulfilling these travel needs.
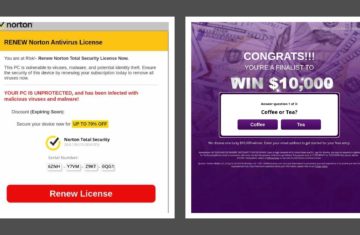
What are hotels doing to secure a share of this volume? Many incorporate video, add feedback collection and recommendation features, leverage blogs, or enhance the content management system. These various services provide for a more interactive and engaging website, as well as enable the site to be optimized. But, did you know that they also represent an entry point for malware and data leakage that can expose a customer’s personally identifiable information?
Yes, hotel ecommerce sites are rife with third-party vendors. As outlined in our recent blog post, brand and ecommerce site managers are not doing enough to protect the online and mobile environment FOR their customers. And hotel websites are no different. In fact, current industry rumors point to a manipulation of an account-checking tool used by a major hotel chain. The compromised tool, in concert with stolen passwords, allowed fraudsters to open new accounts and transfer rewards points which were then exchanged for gift cards. So that got The Media Trust thinking about other website vulnerabilities faced by hotels.
In early December, The Media Trust analyzed the 34 top hotel websites, as listed in STORES magazine’s annual “2013 Top 250 Global Hotels” report published in January 2014. Analysis involved the scanning of all public-facing website pages and the capture of all third-party vendors, domains and cookies present on each hotel’s site.
Over a seven-day period, The Media Trust’s Media Scanner scanned each hotel’s website homepage and major sections 250 times a day—a total 1,750 scans across each site. Each scan executed the web page as if being viewed by a typical consumer, and collected and analyzed all third-party code, content and text for security, latency and data leakage issues. Leveraging our presence in more than 500 global locations, The Media Trust replicated a true user experience as if a real consumer visited the website, and therefore did not have the ability to collect actual visitor data.
The results were interesting. The average site utilized 47 different domains, 31 vendors and 65 cookies; however, some outlier hotel sites used as many as 134 domains and 148 cookies.
Average High
Domains: 47 134
Vendors: 31 57
Cookies: 65 148
What does this mean? That’s a good question. In theory, low numbers are preferred from a manageability perspective as each domain, vendor or cookie represents an access point to or action on a site—the fewer utilized in site operation, the fewer to manage. However, the reality is that a sizeable number of third-party vendors, domains and cookies are found on most sites as they provide the interactive and engaging functionality executing on browsers.
This functionality comes at a cost. Each third-party vendor represents an access point that could be compromised and serve malware; or, redirect visitors to another, possibly malicious, website or app; or, secretly collect website visitor (first-party) data. In addition, each third party can call dozens of fourth or fifth parties which exponentially increases the risk to site visitors.
Browser cookies provide essential site functions, including the ability to navigate without repeating data entry such as destination, travel dates and room requirements. However, the process of dropping the cookie can easily be compromised by an unauthorized party piggybacking on the cookie. In addition, some third-party vendors drop cookies to collect website visitor/first-party data without website owner/operator knowledge. Known as “data leakage”, these cookies track valuable user behavior—data about guests, their interests and travel periods—which can be resold into the online ecosystem for customer targeting by competitors or industry partners. If that data includes personally identifiable information (PII) the website owner/operator could be subject to data privacy violations. With state attorneys general and the federal government cracking down on PII, hotels must be mindful of public-facing website properties and what is executing on visitor browsers.
Hotel websites are vulnerable to data leakage and malware, and this vulnerability opens the door to litigation and significant brand damage. For these reasons website owner/operators need to thoroughly identify, approve and monitor third-party vendors and their activities at all times.
The big question is: How are the major hotel chains managing their public-facing websites to protect their customers?