
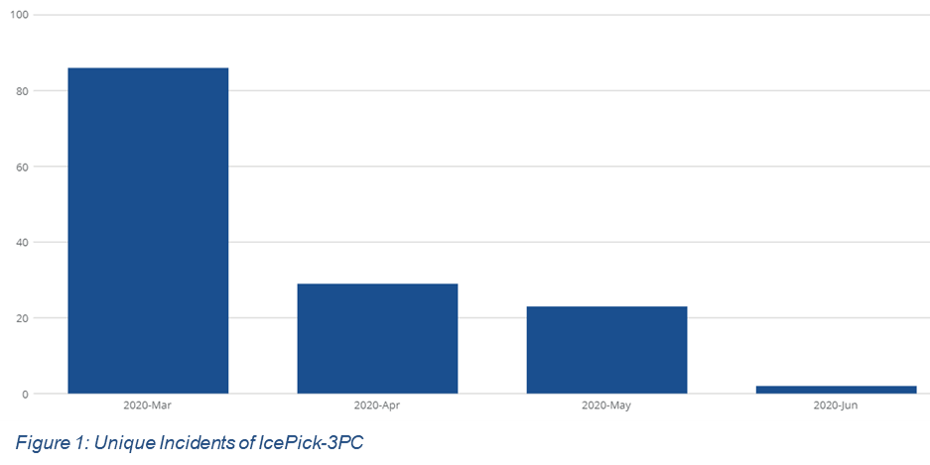
The number of monthly unique ICEPick-3PC incidents managed by The Media Trust’s 24×7 Digital Security & Operations (“DSO”) team increased by 300% or greater beginning in March, compared to Q4, 2019 levels. A single incident could impact hundreds of thousands of website or mobile app visitors. And while an overall increase in malware this year has been reported by many organizations, including The Media Trust, this percentage increase was well above the norm. ICEPick-3PC is highly obfuscated third-party code that targets Android devices and harvests device data for malicious purposes.
ICEPick-3PC attacks fueled by COVID-19
Like other scammers during this period, the bad actor implementing these ICPick-3PC attacks took advantage of much lower CPMs brought on by the pandemic to purchase a range of ad slots across a number of exchanges. Also, many of the malicious ads were served over the weekend.
Why focus such a high percent of the attacks over the weekend? First, many of the at-home consumers that this threat actor targets were likely to be online over the weekend. And second, adtech staff were often not working over the weekend, making it less likely they would quickly react to the attack. In March, 92% of the ICEPick-3PC attacks occurred during the peak days listed below, and in April 66% occurred on peak days.
The highest levels of attacks (peak days) often occurred on Saturday:
- March 7 – Saturday
- March 13 – Friday
- March 21 – Saturday
- March 28 – Saturday
- April 4 – Saturday
- May 2 – Saturday
The Media Trust partners with industry to stop ICEPick-3PC
In early March, upon detecting the elevated ICEPick-3PC signature through continuous scanning, The Media Trust DSO alerted adtech customers and many reacted quickly to shut down this attack and block against future attacks. As a result of these responsive and ongoing efforts by our adtech customers, the number of attacks have decreased each month, in April, May and June.
After the initial attack the DSO continued to see new implementations of this signature, and in addition to notifying customers, we also shared intelligence with other key players in the digital ad ecosystem through the Trustworthy Accountability Group (TAG) Threat Exchange. By presenting information about persistent and malicious third-party code in the TAG malware group, there is a network effect that occurs. Working together with customers and the industry, our goal is to greatly reduce the impact of these types of large-scale attacks across the advertising ecosystem.
The dangers of ICEPick-3PC
ICEPick-3PC was first identified and named by The Media Trust in the fall of 2018, and often targets Android mobile devices. This malware is robust and can break through VPNs in order to intercept IPs. Once the malware determines it has infected an Android device and has cleared the other checks, it makes an RTC peer connection between the infected device and a remote peer, then sends the extracted device IP to the remote device.
ICEPick-3PC is delivered primarily through advertising code, and executes two stages of deobfuscation to deliver the final payload, and as a result is difficult to detect. Through its initial collection of IP information and more detailed personal information being collected through pop-ups and redirects, it can have a devastating impact on a media publisher and its visitors. For example, one of the initial ICEPick-3PC attacks in 2018 detected by The Media Trust DSO involved a redirect to content that congratulated a visitor for winning a well-known retailer gift card and prompting the person to enter sensitive information to receive the card.
For publishers, an ICEPick-3PC attack can lead to a poor visitor experience, loss of ad revenue and exposure to regulatory fines and lawsuits due to sensitive personal information being stolen from their site or mobile app. For adtech, it can lead to loss of business with that publisher and perhaps other publishers.
Anatomy of a successful malware shut down
Malvertising and scams are on the rise due to the pandemic, and it is expected to continue to increase as we enter the last months of the election cycle, where heavy digital ad spending will occur on both the national and state levels. As an industry, we need to work together to shut down these attacks. Based on the recent successful response to ICEPick-3PC malware attacks, here are the steps that make up an effective malware defense:
- Identify – the attack quickly, determining the malware as well as its source. Scan the ecosystem around the clock to quickly identify threats. Ensure new buyers and high-risk partners are scanned prior to going live and given the desired attention from security analysts to monitor the code closely.
- Research – the malware if it is not a known threat to avoid false positives and to understand the potential impact.
- Notify – all parties impacted by the attack. For any high-risk attack, alert via email or text to ensure a rapid response. If an attack involves sensitive personal information (e.g., Magecart), the publisher must consider informing impacted customers to stay in compliance with privacy and state breach reporting regulations.
- Act – to stop the attack immediately. Ensure your company has a game plan for “after hours” attacks to remediate quickly and have a phone/text number provided in case of large scale attacks.
- Protect – against future attacks. Make certain your blocker is up to date.
- Involve – the community. Get the word out to the advertising ecosystem so others can shut this down as well.
About TAG
Trustworthy Accountability Group (TAG) is a first-of-its-kind cross-industry accountability program to create transparency in the business relationships and transactions that undergird the digital ad industry, while continuing to enable innovation. A joint marketing-media industry program, TAG was created with a focus on four core areas: eliminating fraudulent digital advertising traffic, combating malware, fighting ad-supported Internet piracy to promote brand integrity, and promoting brand safety through greater transparency. For more information on TAG, go to www.tagtoday.net



