Isolated and helped fix a major cookie sync error with a large DSP.
Eminem said it best: Guess who’s back? Back again. Redirects are back. And, they’re a pain.
Are customer complaints up? No surprise. A large-scale redirect campaign haunted the digital ecosystem, affecting hundreds of publishers and several AdTech providers across the U.S. and Europe starting on October 24. [Figure 1] From broadcast and news to entertainment and weather, this attack is attributed to a cookie sync error that directed thousands of consumers to a variety of unwanted content, including malware.
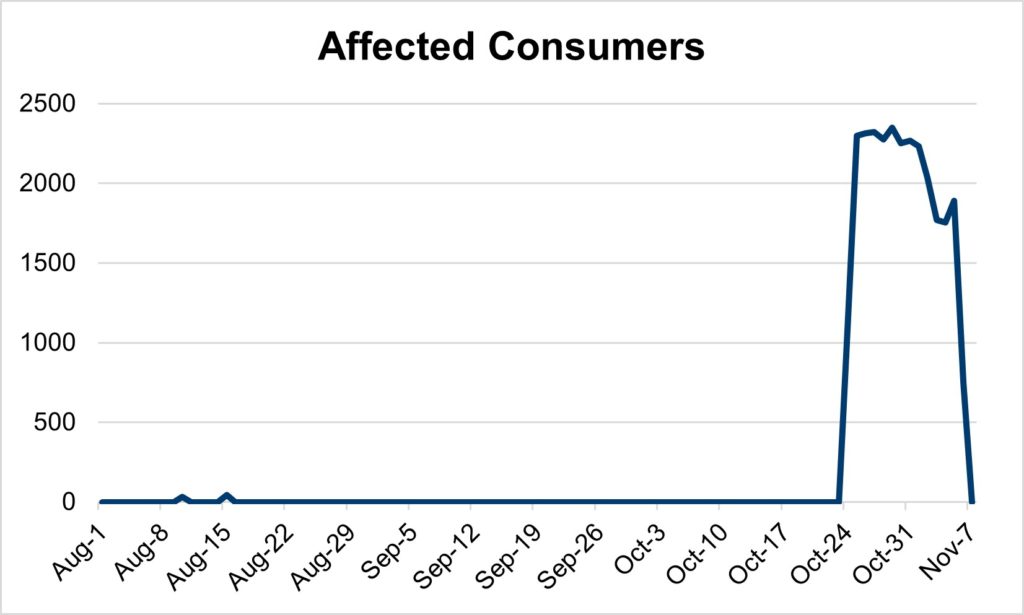
[Figure 1: Consumers confirmed to have their online experience affected by the cookie sync error. However, the number is likely significantly larger. Notice the blips in August. This was likely a testing period in preparation for the larger-scale October attack.]
Incidents like these—which bypassed every creative blocker—highlight the importance of evaluating the entire digital advertising experience, not just ads. Continuous analysis of web-rendering content provided the appropriate context to remediate the problem.
When a cookie sync error is dumb
An important AdTech process, cookie syncs match user IDs across platforms and publishers. This recent situation involved a broken sync process between two different AdTech platforms— contextual and content providers—that involved the use of dummy[.]com, a common test domain that should resolve to the platform url. However, for two weeks it redirected to a range of content and subjected consumers to tech support scams, ransomware exploits, parked domains, affiliate marketing/ unexpected pages with unwanted content, and more. These rotating payloads all involved a form of phishing.
This attack was widespread enough that there are no real conditional elements or patterns to it other than the sync event between the two platforms. It was also indiscriminate, occurring across multiple browsers/OS and affecting the elderly, children and everyone in between. It was also global, affecting consumers around the world, especially those in France, Japan, UK and the United States. [Figure 2]
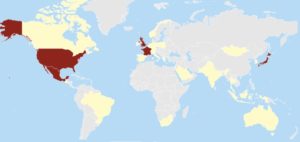
[Figure 2: Geography of consumers confirmed to be impacted by this cookie sync error]
In effect, consumers accessing hundreds of publisher sites afflicted by the cookie sync error experienced the redirect.
Towards the end of the campaign, the redirects resolved to more benign activity, e.g., affiliate marketing and popups. This is likely an attempt to extend its life (and reach) and penetrate websites with softer policies. However, it is still malware. It auto-redirects consumers to content to phish for sensitive data.
Every incident with this domain looked nearly identical; it was always the result of that same cookie sync URL. Thankfully it was corrected before things got worse: Dummy.com is for sale for $251k. This attack would have continued to escalate and draw more attention—this reporting sounds suspiciously similar; however, the story lacks the details to confirm.
Malvertising outside the bid request
Cookie sync errors driving malvertising isn’t new. However, this one exhibited a few unique characteristics:
- Uses one specific cookie sync url, not a range
- Attributed to a large DSP platform
- Redirected users to a wide variety of content—some malicious, some not
Don’t be a dummy
The cookie syncing process that triggered this redirection occurred after ad delivery, independent of any one ad tag delivered. As it was far removed from ad markup, it was not seen or stopped by creative blockers.
It could only be resolved with the affected parties since it occurred outside of the bidding process and was not related to any content they are serving. This is why it needs to be shut down at the point of origin. Continuous, client-side scanning not only confirmed the escalating nature of the incident but also revealed the call chain to pinpoint the affected parties.
The Media Trust’s malware desk repeatedly interacted and shared details with the impacted DSP who struggled to locate the appropriate parties to update the code. Finally, the DSP resolved the errors midday on Sunday. We can confirm that there are no longer any cookie sync errors associated with dummy[.]com
Like Eminem said…
Now this looks like digital trust and safety. So everybody, just follow TMT. ‘Cause we really need advertising. ‘Cause it feels so empty without loyalty.



