Authored by Matt O’Neill, General Manager, Europe, The Media Trust.
The way the cookie crumbles
Today’s websites and apps (your corporate website included) are powered by sophisticated technology. After all, in order support consumer expectations—content consumption, search, social networking, shopping carts, travel booking, banking, news, gaming and so much more—websites incorporate robust solutions on the backend.
These solutions aren’t news to most InfoSec professionals, but it is where security problems start. Think about it. Almost 80% of a typical website’s functionality is outsourced to vendors providing specialized services such as data management platforms, marketing analytics, customer identification, image or video hosting, payment processing, content delivery and more. This third-party code operates outside the purview of your IT and security infrastructure, which means that you control less than 25% of the code executing on your website. As the website operator, you have no insight into when this code is compromised to act as a conduit for malware propagation and unauthorized audience data collection. Considering the current regulatory environment around data compliance, the above statistics should make you nervous.
Cookie crumbs
To put it bluntly: You can’t control what you don’t see, and the third-party code enabled functionalities on your digital properties are compromised more often than you think. Also, you have more third-party code than you realize.
As the security provider of choice for the world’s largest digital properties, The Media Trust scans websites for security and policy violations and actively manages more than 500 incidents at any one time. Some of the simplest websites average 10 third-party vendors, but most have dozens. The vendors continuously change and so do their actions.
The Media Trust’s website security and scanning team often detects persistent or unauthorized cookies with a lifespan of 30 years or more; one brand name ecommerce website recently dropped a 7,000+ year cookie. This is a huge issue with the EU’s General Data Protection Regulation (GDPR) which goes into effect in less than a year. Compliance to GDPR requires detailed, real-time, knowledge of executing digital partners and their activity, including the type of data collected and how long the partner remains on the user’s device, i.e., browser, phone, tablet, etc.
If you are wondering how GDPR affects your business, then you’ve got a lot of catching up to do. GDPR supports the data protection rights of every EU resident, therefore every business with EU interests—in the form of customers, legal entities, business infrastructure, etc.—needs to comply. And, the global nature of the internet means any business with EU website traffic or app users needs to comply as well.
Clearly, enterprises should make some changes to digital operations in order to reduce exposure to GDPR violations. At a minimum, you need to do the following for all your digital properties—websites (desktop and mobile) and mobile apps included:
1. Communicate privacy policy
- Write a clear privacy policy that explains use of third-party code and outlines any data collection activity
- Place banner on homepage
- Deliver Internal training
2. Provide easy-to-use opt in/ opt out mechanism
- Explain need for tracking and how cookies are used to drive digital operations
- Share links to individual privacy policies of all in-scope vendors on your site
- Allow individuals to explicitly agree and/or refuse tracking
3. Understand how website/app-generated data is acquired, used & stored
- Identify data: Registration, Cookies, IP addresses, device IDs
- Assess the legal basis to collect data and determine if consent is necessary, e.g., Personally Identifiable Information (PII) vs. transaction functionality, etc.
- Evaluate need for a specific policy regarding data collection of minor activity (16 years old in GDPR; under 13 years old in U.K. and U.S.)
4. Support data portability
- Provide mechanism to easily satisfy a data subject’s request for personal data in a commonly used format.
5. Incorporate website intrusion in data breach reporting
While the GDPR mandate for websites has been clearly laid out, meeting it is easier said than done! With the fines for noncompliance enumerated in the regulation (between 4% of global revenues or €20 Million), InfoSec is under pressure from internal risk and compliance professionals to ensure all data elements are documented, assessed and controlled.
Ignorance is real. So is anarchy.
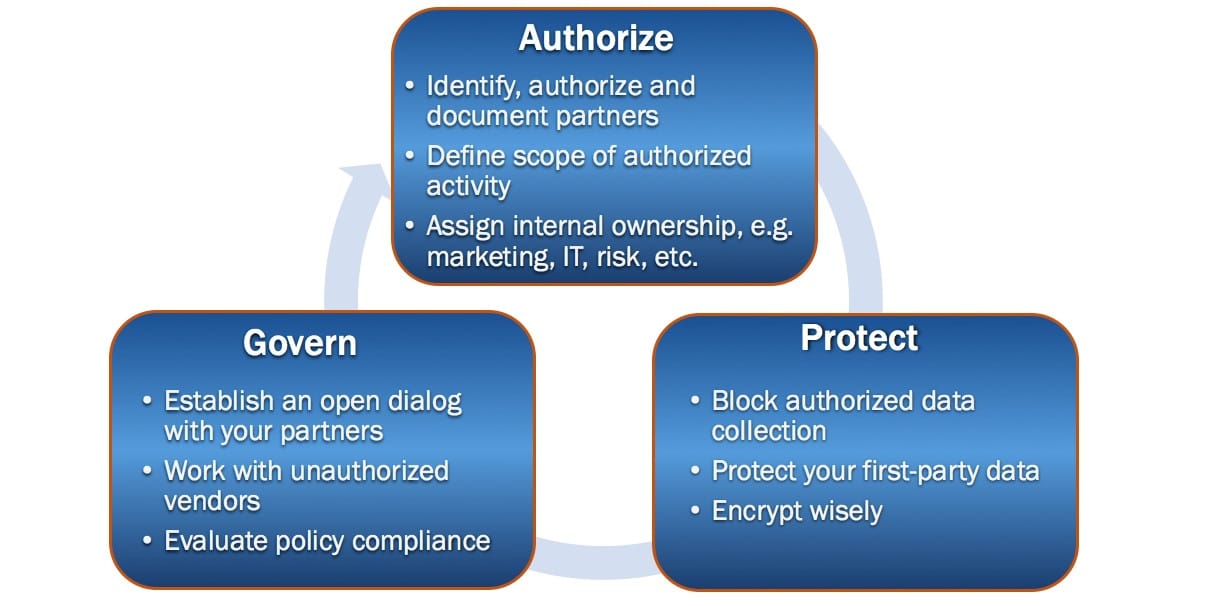
With such a tall order, it is disturbing that so many InfoSec professionals overlook the perils of third-party vendor code going unchecked. Companies desperately need to incorporate digital vendors into their vendor risk management program. Most website/app operators are in the dark about how many direct and indirect vendors contribute to code on their site and who these vendors are, let alone know how many domains and cookies these vendors use to track website visitors.
Digital vendor risk management will highlight the security and compliance gaps inherent in the digital environment. For example, there really isn’t a clear chain of command when it comes to authorizing the presence of third-party vendors executing on a website. It is a fairly decentralized process, with departments like marketing, sales, IT, risk and legal all making decisions regarding the vendors they would like to use for various website functionalities. This makes creating accountability challenging, with most issues relegated to the IT and security departments to solve.
Putting the “Digital” in Vendor Risk Management
Yes, the odds are stacked against website operators, but creating a holistic digital vendor risk management program isn’t impossible. To create a risk management and GDPR compliance program for your digital properties, you should be able to answer the following:
Within 2 weeks:
- How many third-party vendors execute in websites and mobile apps
- What are the names of these vendors?
- What exactly are they doing, i.e., intended purpose and also additional, out-of-scope activity?
Within 1 month:
4. Do we have contracts to authorize the scope of the work?
5. How does third-party vendor activity affect overall website/app performance?
6. What are the risks to data privacy?
7. What is my exposure to regulatory risk via vendor behavior?
Within 3 months:
8. Am I maintaining encryption throughout the call chain?
9. As these vendors change over time, what is the process to identify new vendors and their activity on websites and apps?
10. If the corporate website isn’t fully secure, what happens when employees visit the site? Is the enterprise network at risk?
Once you’ve been able to answer the above questions, within a year’s time, you should be able to create comprehensive digital vendor governance process that looks like this: