COVID-19 is driving exponential increase in malware
Each year brings new challenges to enterprise security teams, but nothing as drastic as the current Coronavirus or COVID-19 pandemic. Working from home is no longer a perk; it’s a necessity to maintain business continuity (and employee well being). Unfortunately, this telework surge is accompanied by a drastic increase in malware from in-home internet use. Safeguarding remote employee internet access has leapfrogged in priority for protecting the enterprise network. Now security and IT teams are discovering the gaps in their VPN, web application firewalls or other perimeter security tools.
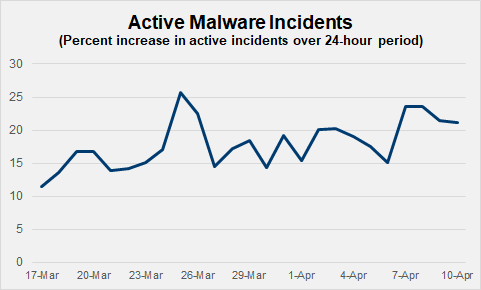
Daily malware threats increasing an average 18%
The current news cycle is driving increased web traffic as employees adapt to their new normal, causing a corresponding proliferation of malware. Since mid-March, the average number of incidents in a 24-hour period actively managed by The Media Trust’s 24×7 Digital Security & Operations team has significantly grown 18% during the period–sometimes this volume is 26% more than usual.
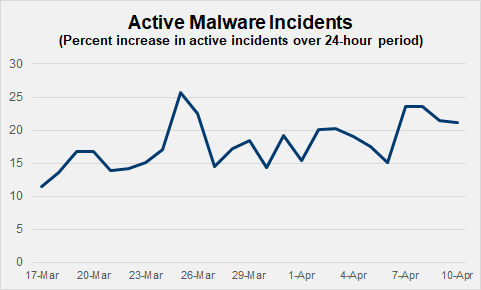
The increase is driven by Coronavirus-related activity, both scams and those looking to take advantage of increased internet volume to target users. Phishing and the spread of disinformation and/or misleading product claims characterize the majority of these incidents.
Specifically, the following trends were noted during March:
- 57% of incidents phished for user information
- 20% of incidents were attributed to scams or attempts to defraud users
- 2,600+ eskimming or Magecart events targeting enterprise websites, CartThief-3PC is a variation
- 11% of advertising landing pages contained overt malware
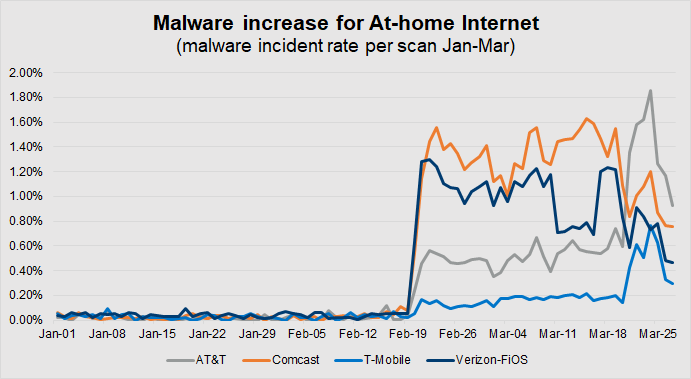
Telework activity drives 20X malware growth
The inflated volume of malware targeting at-home internet connections reflects the changed telework dynamic. Bad actors are focusing their efforts to deliver malware through AT&T, Comcast Xfinity, T-Mobile and Verizon FiOS services which has driven a 20X increase in malware since January–a typical 0.04% malware detection rate increased to 0.79%. As antivirus tools learn about and add the malicious domains to their appliances, the malware detection rate starts to decrease, a process that can take weeks while devices continue to be infected.
More sinister than fake Coronavirus maps or scams, organizations have to worry about malware that infiltrates a device to execute unwanted tasks like being used to orchestrate DDoS attacks, credential stuffing, cryptomining and more. This type of malware is readily found propagating via typical sites accessed by their employees in support of everyday business. From general news and industry research to social platforms and online games, employees are continuously exposed to countless advertisements, offers, and popups. These activities often encourage installation of toolbars or other unwanted programs–many auto-install without employee interaction.
These programs are frequently ignored by security teams which consider them more annoying than malicious. In fact, their ubiquity is often considered noise and blamed for alert fatigue. This approach is short-sighted, as state actors use these programs to phish for data and probe for vulnerabilities which can be used in future targeted attacks to the device and other devices associated with the employee.
Large-scale or risk-averse organizations use VPN or have policies dictating how employees can access the company network or allow personal use of company-issued devices. The problems arise once employees disconnect from the VPN, surf legitimate websites, encounter malware and/or adware, and then introduce that malware to the company network during the next VPN connection. Enterprise threat feeds need to include this at-home targeted malware in order to better protect the network.
Prepare today, Prosper tomorrow
One thing is clear, malware threats are on the rise. To defend against these attacks enterprises need to:
- Augment their web application firewalls and filtering appliances with real-time data on malware actively propagating in the digital ecosystem before it hits the network
- Understand which digital activity to pay attention to and which to delegate down. Assuming it is all noise is the worst thing you can do.
- Scan websites and/mobile apps from the user point of view to identify potential vulnerabilities
P.S. Test your knowledge of digital risks by taking the Digital Risk Assessment quiz .



