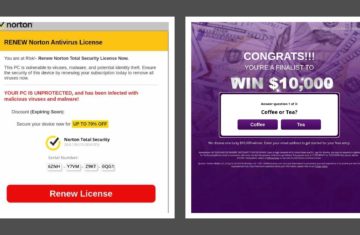
HTTPS code does not mean a site is encrypted
Today is D-Day for ecommerce and IT professionals, basically anyone with a revenue-generating digital property. June 30 marks the day that Google’s ad networks move to HTTPS and follows previous statements indicating HTTPS compliance as a critical factor in search engine rankings.
From Google’s announcement to the White House directive mandating HTTPS-compliant federal websites by December 2016, encryption has become the topic du jour. And, rumors abound that browsers are getting into the encryption game by flashing alerts when a site loses encryption. Why all the fanfare?
Encryption adds elements of authenticity to website content, privacy for visitor search and browsing history, and security for commercial transactions. HTTPS guarantees the integrity of the connection between two systems—webserver and browser—by eliminating the inconsistent decision-making between the server and browser regarding which content is sensitive. It does not ensure a hacker-proof website and does not guarantee data security.
Over the past year, businesses worked to convert their website code to HTTPS. With Google’s recent announcement, ad-supported sites can sit back and relax knowing their sites are secure, right? Wrong.
To have a truly encrypted site you must ensure ALL connections to your website communicate through HTTPS, including all third-party code executing on your site, not just advertising. This means sites using providers such as content delivery networks, data management platforms, hosting services, analytic tools, product reviews, and video platforms, need to ensure connections—and any connections to fourth or fifth parties—are made via HTTPS. Just one break in any call chain will unencrypt your site. Considering 57% of ecommerce customers would stop a purchase session when alerted to an insecure page, the ongoing push to encrypted sites should not be ignored.
What’s a website operator to do? By its very nature, third-party code resides outside your infrastructure and is not detected during traditional web code scanning, vulnerability assessment, or penetration testing. To ensure your site—and all the vendors serving it—maintains encryption you must scan it from the user’s point of view to see how the third parties behave. Only then can you detect if encryption has been lost along the call chain.