Malware uses compromised landing pages with out-of-date web publishing software to send users on a wild ride of credential theft and ad fraud
It’s an unspoken rule that software update notifications always show up at the most inconvenient times—right before an important presentation at a meeting, as you need your mobile boarding pass to get on an airplane, when you’re in the middle of an emergency call, etc., etc.
Thing is, you can’t afford to push off software updates as more and more of them address grave security concerns such as zero-day attacks. And content management systems (CMS) and publishing platforms are constantly under threat of zero-day vulnerabilities and need to be updated regularly.
But that doesn’t happen for many advertising landing pages—especially with small- and mid-sized businesses where landing page development may be outsourced—so the CMS and its various plugins are not routinely updated. Hackers are quick to find these vulnerabilities and turn innocuous landing pages into malware delivery centers. These are attached to creatives shot through the ad pipes, putting consumers a click away from dangers such as credential theft.
Analyzing compromised landing pages yields insight into threat actors’ latest tactics to spread harm, such as an intricate new redirect attack that The Media Trust has named Chronos-3PC. Targeting mobile browsers, Chronos uses several interesting methods of obfuscation to avoid detection, extend campaign life, and continue spreading pain to unwitting consumers.
Threat Anatomy
First identified back in November 2021, Chronos can be injected into a CMS or publishing platform via an actual site/page vulnerability or an out-of-date plug-in. A major differentiator from other redirects is that Chronos is actively looking for a mobile authentication token to ensure that malware is served only to mobile browsers.
The redirect also drops the _mauthtoken browser cookie to limit the amount of redirects pushed at a specific consumer, a tactic The Media Trust has increasingly seen on compromised landing pages. Strange enough, malvertisers seem to believe in frequency capping, perhaps to keep campaigns alive longer and increase reach.
The next distinction point is the use of Zeep.ly link shorteners to hide the redirect’s destination. This makes the malware harder to identify and track—as well as stop at the source. The malvertisers use this trick to push one more layer of obfuscation.
Instead of just hopping to the final malicious landing page, the malware sends the user to another compromised page, where it redirects to the ultimate landing spot. These middle pages can be easily switched in and out, especially as new vulnerable pages are hacked, making it even more difficult to track the malware source.
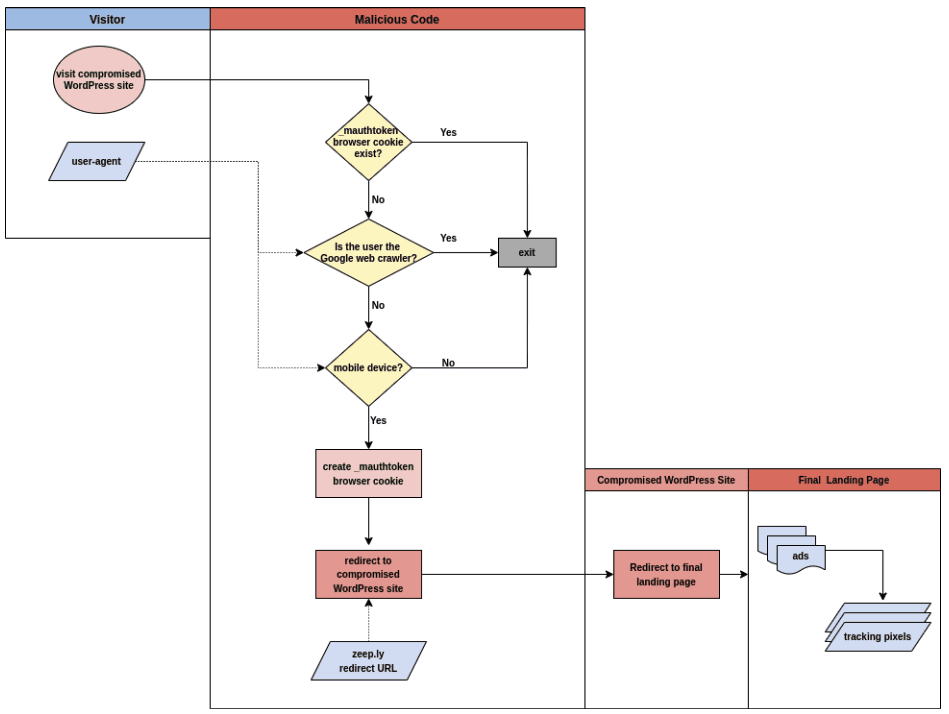
Figure 2: This flowchart highlights how Chronos leverages a redirect to another compromised site before sending the user to a malicious destination.
While Chronos has been employed to phish identification credentials such as logins from consumers, it’s also employed to proliferate ad fraud. Many consumers will be redirected to a page haphazardly filled with display ads, many on top of each other in classic ad stacking form. A plethora of tracking pixels fires as soon as the user hits the page.
Prevention With an Update
For advertisers with compromised landing pages, platform partners can be lifesavers. During audits, platforms should be analyzing tags, creatives, and landing pages. Corrupted pages can be identified immediately, with platforms informing their advertisers so they can remediate and get their campaigns rolling as intended.
Failing to update web publishing software on landing pages doesn’t just leave an advertiser vulnerable—it’s a threat to any consumer that may click on their ad.
Publishers can rely on The Media Trust’s continuous scanning of ad inventory passing through upstream partners to catch compromised landing pages pre-flight as well as during campaigns. Furthermore, “in-the-wild” ad analysis examines suspicious campaigns and heuristic signals to identify hacked pages.
The best form of prevention, though, is ensuring CMSs and their plug-ins are up to date—even if the software update notification arrives at an inconvenient time. Advertisers can’t publish landing pages and simply think they’re in the clear for a campaign’s life—or even an indeterminate amount of time. Anyone who owns or operates a WordPress should perform scanning with a tool like WPScan to unearth vulnerabilities and inform site administrators about plugins that need to be updated.
Failing to update web publishing software on landing pages doesn’t just leave an advertiser vulnerable—it’s a threat to any consumer that may click on their ad.
For more technical information regarding Chronos-3PC, download this detailed malware report [PDF].