MimicManager-3PC infiltrates landing pages to attack consumers and steal data
Something about that display ad on your favorite website speaks to you, so you give it a click. But instead of a nifty product page, a redirect appears claiming that your device is chock full of viruses, call this number now!
You’re taken aback—the company advertising is a recognizable name, so why on earth is their website trying to defraud you and infect your device?
Chances are, the legit advertiser had its landing page hacked—and the company likely doesn’t even know. Through compromised landing pages, victimized advertisers actually become malware distributors—and can help threat actors broaden and improve their consumer targeting efforts.
An evolving malware attack is empowering them to compromise web pages and disperse backdoors and phishing at a never-before-seen rate.
Unsafe Landings Courtesy of MimicManager-3PC
Dwarfing a major increase seen in summer 2021, the amount of malicious landing pages has exploded over the last few months, and grown 4X since the beginning of 2022 [Figure 1].
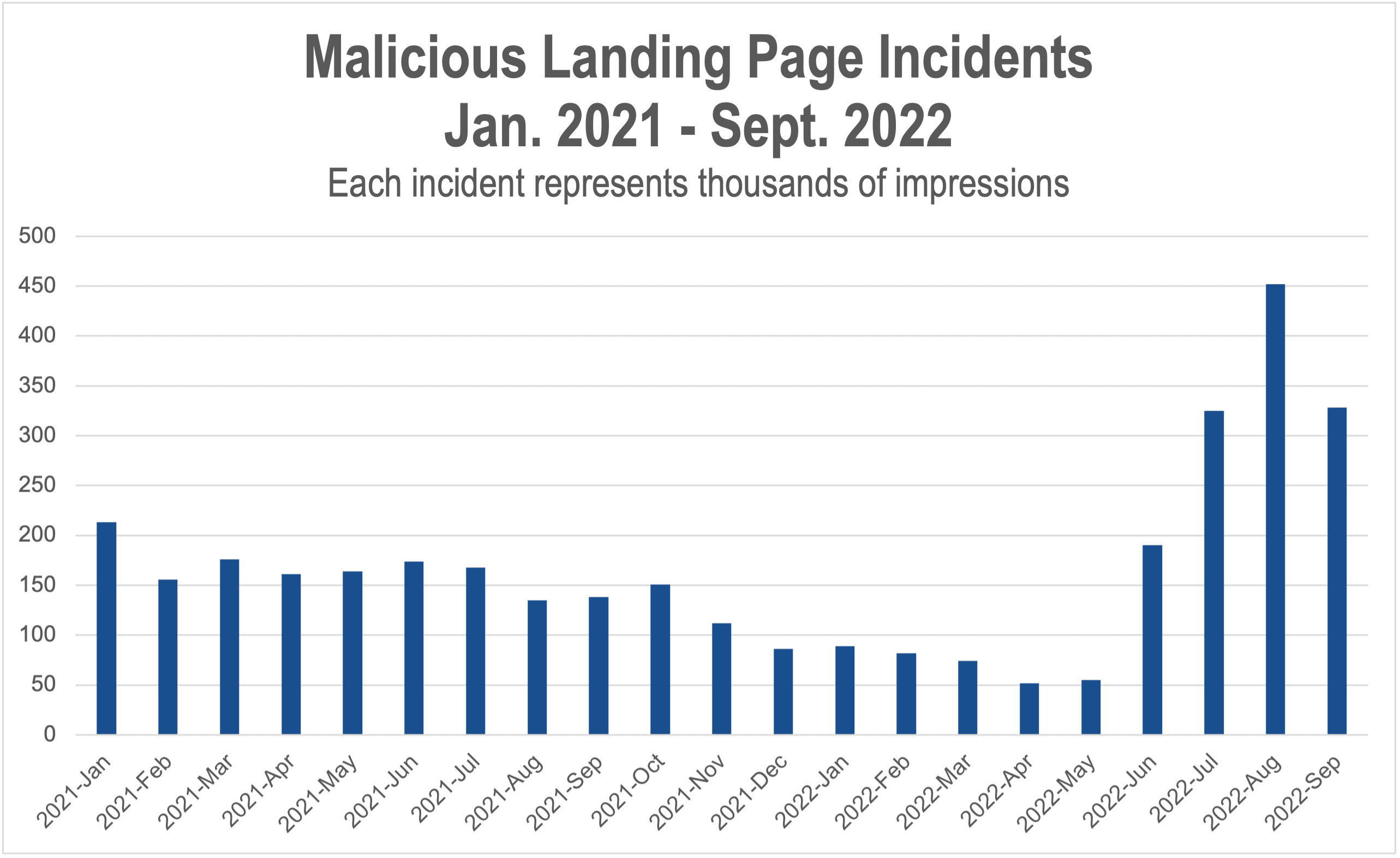
Even worse, these malicious landing pages are predominantly serving backdoors, which open lasting vulnerabilities on devices and leave consumers prey for more severe attacks such as cryptojacking and ransomware.

A chief culprit of the rise in compromised landing pages is a new attack that The Media Trust’s malware desk has named MimicManager-3PC. This elusive threat has already compromised hundreds of websites, from local real estate and travel agents to major e-commerce shops. It continues to spread like wildfire, with 3-7 new compromised domains appearing every day on average since June. MimicManager is using its scale not only to directly attack consumers, but also build repositories of vital consumer information for future assaults.
And potential targets seem limitless—The Media Trust has detected more than 30 AdTech platforms delivering campaigns with landing pages corrupted by MimicManager.
Frighteningly Flexible
Numerous attack types are launching from MimicManager, including backdoors and phishing [Figure 3]. Many threat actors leverage the malicious tool for a variety of devious purposes, and some take advantage of the malware’s flexibility to employ device-level targeting and extra layers of obfuscation.

Like other threats compromising landing pages and advertiser domains, MimicManager is primarily injected into vulnerable publishing software like WordPress via corrupted JavaScript libraries. However, the malware desk has also detected the malware outside the content management system (CMS), baked into source code.
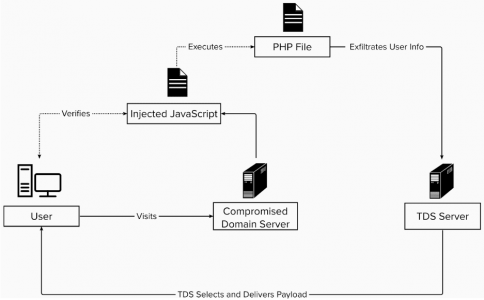
When a consumer accesses/visits a compromised website, MimicManager initially checks to make sure the user is human before deploying its malicious payload from a remote server. This tactic helps the malware evade detection by threat-hunting emulators. MimicManager then checks to see if the consumer has already been hit by one of its malicious payloads.
See, the malware isn’t just dropping backdoors and executing phishing—it’s also exfiltrating consumer data like IP addresses, user agents, and device information to add to a traffic direction system (TDS) [Figure 4]. After MimicManager marks a user as human, the TDS selects the specific malicious payload to deploy. More assaults by MimicManager expands the TDS’ target base and enriches its knowledge pool.
Download the full malware report on MimicManager-3pc [PDF]
What might be most unique—and most troubling—about MimicManager is that the malicious payload does not appear in call chains, making it far harder to detect. Identifying infected websites requires an examination of source code for key indicators of compromise. Many advertisers will be puzzled why their campaigns are being flagged as malicious—unless their platform and publisher partners help them excise MimicManager.
Fighting Back
Many advertisers—especially small and midsized ones—outsource landing page development and overall website design to agencies or freelancers. Sometimes they don’t even have access to the actual CMS. This degree of separation can become a serious problem—web publishing software is updated frequently due to security vulnerabilities, and out-of-date CMSs are ripe targets to hack.
Many advertisers have no clue their landing pages have been compromised by MimicManager. The malware is quite difficult to detect. Advertising platforms and publishers running ads can act as coal mine canaries, protecting consumers and also saving advertisers from embarrassment or worse.
Platforms need to be analyzing not just creatives, but also all clickthroughs and landing pages passing through their pipes. And because many of these malware attacks are highly targeted, a security provider should be scanning for threats with a variety of device profiles—e.g., different browsers, devices, geography. Once compromised pages are identified, platforms can endear themselves to their advertisers by alerting them to the malware and explaining the ongoing threat to consumers.
Publishers leveraging creative blockers need to be sure that their security providers are diligently scrutinizing landing pages; otherwise advertising with MimicManager will show up and invite their audiences to click. Blocklists powered by first-party data from in-house malware analysts tend to be stronger here than ones with third-party lists. Even better, publishers can warn advertisers about compromised landing pages, possibly using the opportunity to forge new and stronger relationships.
Legit advertisers care about the well-being of consumers. The idea of unwittingly distributing malware to potential customers is horrifying. It’s in platforms’ and publishers’ best interest—as well as the consumers’—to help advertisers identify compromised landing pages and take MimicManager down.