Startling rise in malicious landing pages draws attention to honest advertisers unknowingly hacked
- 5X increase in malicious and compromised landing pages over last six months, dominated by software install prompts
- Legit advertisers using out-of-date publishing software have landing pages compromised by bad actors
Recommendations
- Continuous client-side scanning for malware, including click-throughs to detect malicious and compromised landing pages
- Stress to advertisers importance of ensuring content management software is up to date and domain status is in good order
Protecting consumers from ad-delivered malware often focuses on the imminent threat—for example, a malicious redirect served as a browser lands on a page. But just as important is the danger lying in wait—a malicious landing page driving a fake software update, phishing for personal data, or perpetrating some other nefarious activity.
This is all the more treacherous when a creative comes from a legit advertiser unaware that their landing page is compromised.
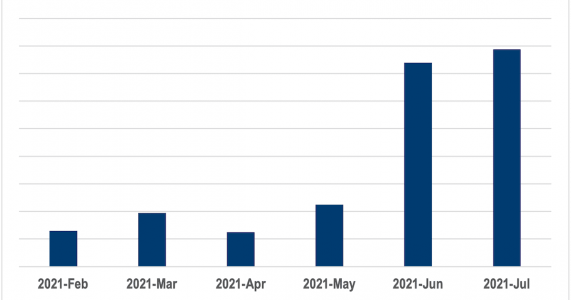
Since February 2021, The Media Trust’s Digital Security & Operations team has detected a startling 5X rise in malicious landing pages. (Figure 1) Interestingly, the unique incidents or malicious campaigns have actually held steady over this time period, suggesting these bad actors have a massive footprint across the web.
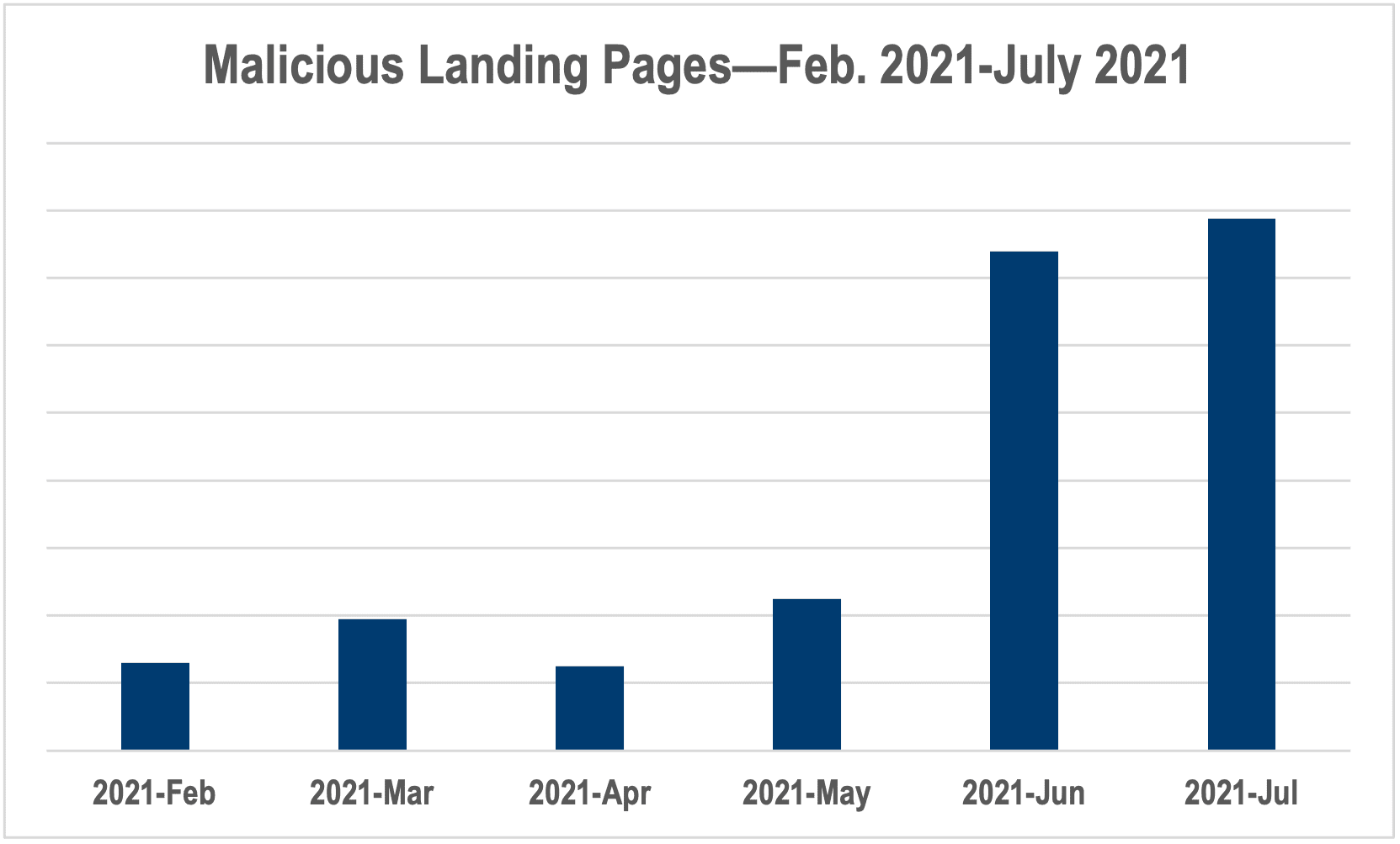
Two-thirds of the malicious landing were prompts for software installs. (Figure 2) Often these are fronts for adware, which can be used to serve additional malvertising or be leveraged for even larger attacks such as ransomware campaigns. Phishing lures and scams made up another quarter of the malicious landing pages.
Unknowingly Compromised
What makes many of these landing pages particularly pernicious is that they are attached to genuine creative from advertisers with no malicious intent—they’re just trying to sell stuff. Advertisers large and small can find their landing pages hacked by malicious actors, but smaller ones are particularly vulnerable as they tend to outsource web development, lack resources to review in-flight campaigns, and have limited control over maintenance.
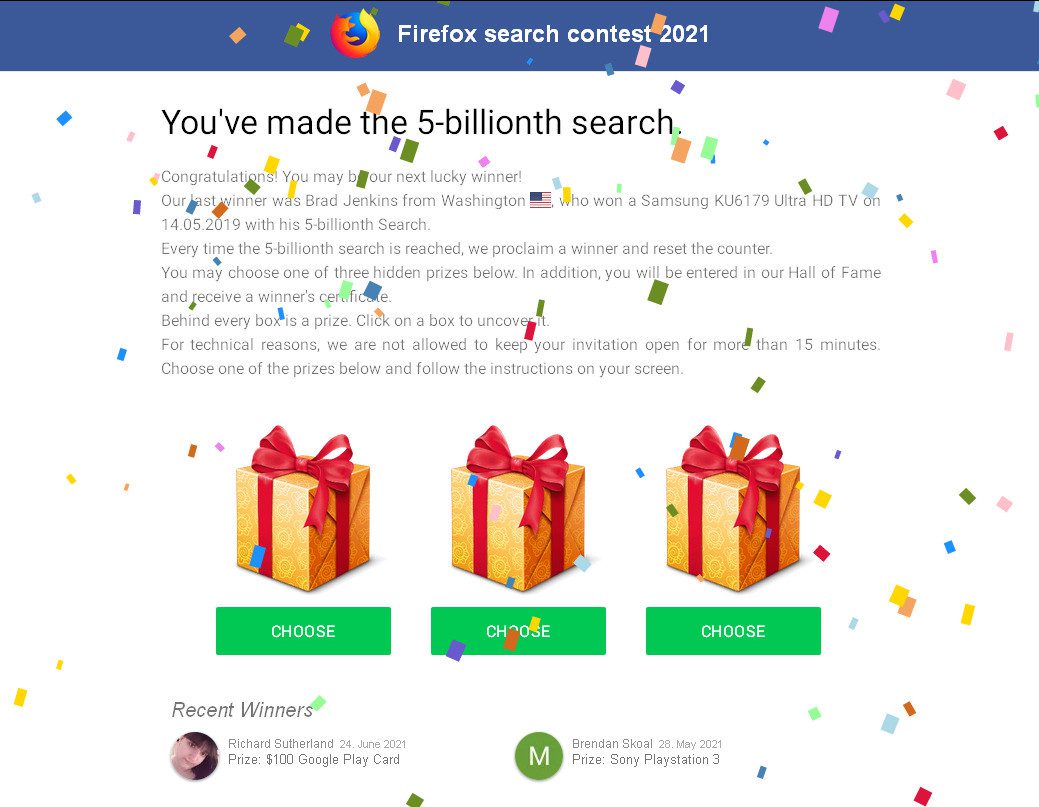
Publishing platforms such as WordPress are constantly under attack from bad actors, and regularly release software updates to close vulnerabilities and thwart prevalent attacks. If advertisers aren’t keeping their publishing software up-to-date, they can fall victim to hackers—specific landing pages can be turned into depots for fake software installs or phishing lures (Figure 3) with the advertiser unaware.
Also, if an advertiser outsources web page development, they can lose track of domain registration and end up with landing pages using expired domains. As seen in the recent user-sync-hijacking episodes, bad actors can grab parked domains—sometimes just for short periods of time—of respectable advertisers to serve malicious content. This can be particularly problematic if an advertiser is running ad campaigns without realizing their domains are parked.
Team Effort
Not only are compromised landing pages a threat to consumers, they cheat advertisers out of business and soil a brand’s reputation. This in turn could lead to less advertising spend coming through the ad pipes. It’s not just ethical to speedily inform an advertiser of a compromised landing page—it’s also good for business. In addition, alerting an advertiser to landing page issues is a solid way to tighten a relationship, as well as show you value them as more than another revenue source.
Beyond just using click-through scanning to find malicious and compromised landing pages, encourage the advertisers you work with to make sure their content management systems are up to date and that their domains are in good standing. Even one compromised domain causes ripples throughout the advertising chain.