E-skimming domains are popping up on online retailers right as digital shopping picks up holiday steam.
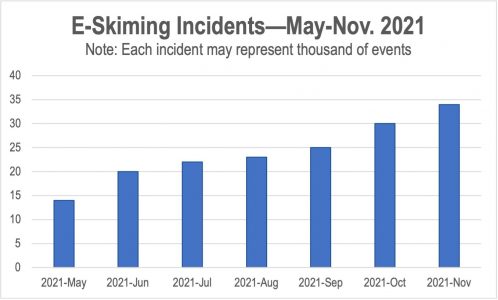
- 150% increase in e-skimming detected since May 2021
- Distinct e-skimming incidents are up 48% year over year
Recommendations
- Brand retailers need continuous scanning of properties with a variety of device and geographic profiles to identify e-skimming domains
- AdTech and publishers need clickthrough scanning to identify compromised landing pages
With a new Covid variant spreading fear instead of cheer this season, shoppers are hitting online retailers in stride to grab gifts for the holidays. But digital perils are just as abundant, starting with a major rise in scam ads from fly-by-night retailers selling trendy merchandise (e.g., outfits inspired by Squid Game) peppered with an egregious amount of data collection. These shady e-commerce companies have checkered track records delivering the advertised and purchased items let alone processing refunds.
The bigger danger, however, resides when consumers plunk down their credit card numbers. It seems bad actors are feeling especially spirited this year, unleashing e-skimming Grinches all over the digital ecosystem.
What’s E-Skimming?
It may sound like something for speed-reading books, but unfortunately an e-skimmer is website code operated by a third-party bad actor that snatches data shared by a consumer. While e-skimmers can grab any type of personal identifiable information (PII)—like name, email, or even (gasp) Social Security card—the real gold is credit card numbers, which is why payment pages are prime targets. (This is a good reason ecommerce companies should limit third-party code on payment and other sensitive pages.) The dark prince of e-skimmers is the dreaded MageCart.
Seasonal Affliction
As the holiday shopping season approaches, The Media Trust typically sees a ramp-up in e-skimming activity, but the amount seen in November 2021 is 48% higher than the year prior. Since May 2021, identification of e-skimming domains has jumped 140% (see Figure 1 above). These domains have been detected scraping consumers’ PII, and can steal credit card information when appearing on payment pages.
Beyond the pain they cause consumers, credit card compromises can be highly damaging or even fatal for the retailer, as Macy’s learned in 2019. Loss of customers and lasting reputational impact can cause a shop to shutter its digital doors. In addition, breaches can lead to civil suits and even massive fines by regulators.
It may sound like something for speed-reading books, but unfortunately an e-skimmer is website code operated by a third-party bad actor that snatches data shared by a consumer.
Advertising Impact
E-skimming on retailer properties quickly becomes a problem for AdTech and publishers alike, because what are online commerce companies known to do in the lead-up to the holidays? If you answered, “Advertise!,” get yourself a candy cane.
Fortunately, clickthrough analysis during creative audits helps inform advertisers that they have an e-skimming problem—especially small retailers with limited security resources. Informing companies of such malware challenges on their properties can actually endear an advertiser to an AdTech platform, with the promise of additional spend in the future. Key here is scanning from multiple devices and geos, as e-skimming domains are typically elusive, only showing up under target conditions.
But AdTech platforms also need qualified clickthrough scanning to protect their downstream publisher partners and consumers. Publishers can also look out for themselves—they need assurance that their ad-quality provider includes advertising with compromised landing pages (e.g., e-skimmers) on the malware list fueling its creative blocker. Without that data, publishers are potentially leaving their audiences vulnerable to pernicious traps.
Stay safe this holiday season—and help keep safe the personal data and credit card information of shoppers worldwide.