
Enduring named threat spreads from new demand sources in massive January-February outbreak.
With all the bad vibes in digital advertising around a weak fourth quarter, shuttering AdTech operations, and jaw-dropping amounts of layoffs, the last thing the industry needed was a tsunami of mobile phishing redirects.
Alas, when it rains, it pours—the threat actors behind long-running GhostCat-3PC stormed the digital ad marketplace and flooded platforms, publishers, and consumers in mobile-targeted phishing schemes.
The Media Trust’s Digital Security and Operations team have become something akin to GhostCat whisperers, able to determine from the malware’s long testing periods with numerous variants when the threat actor has found suitable vulnerabilities and is ready to go on a redirect rampage. As seen in Figure 1, GhostCat incidents (which each impact thousands of consumers) ramped up sharply at the end of January to spread mobile misery throughout February.
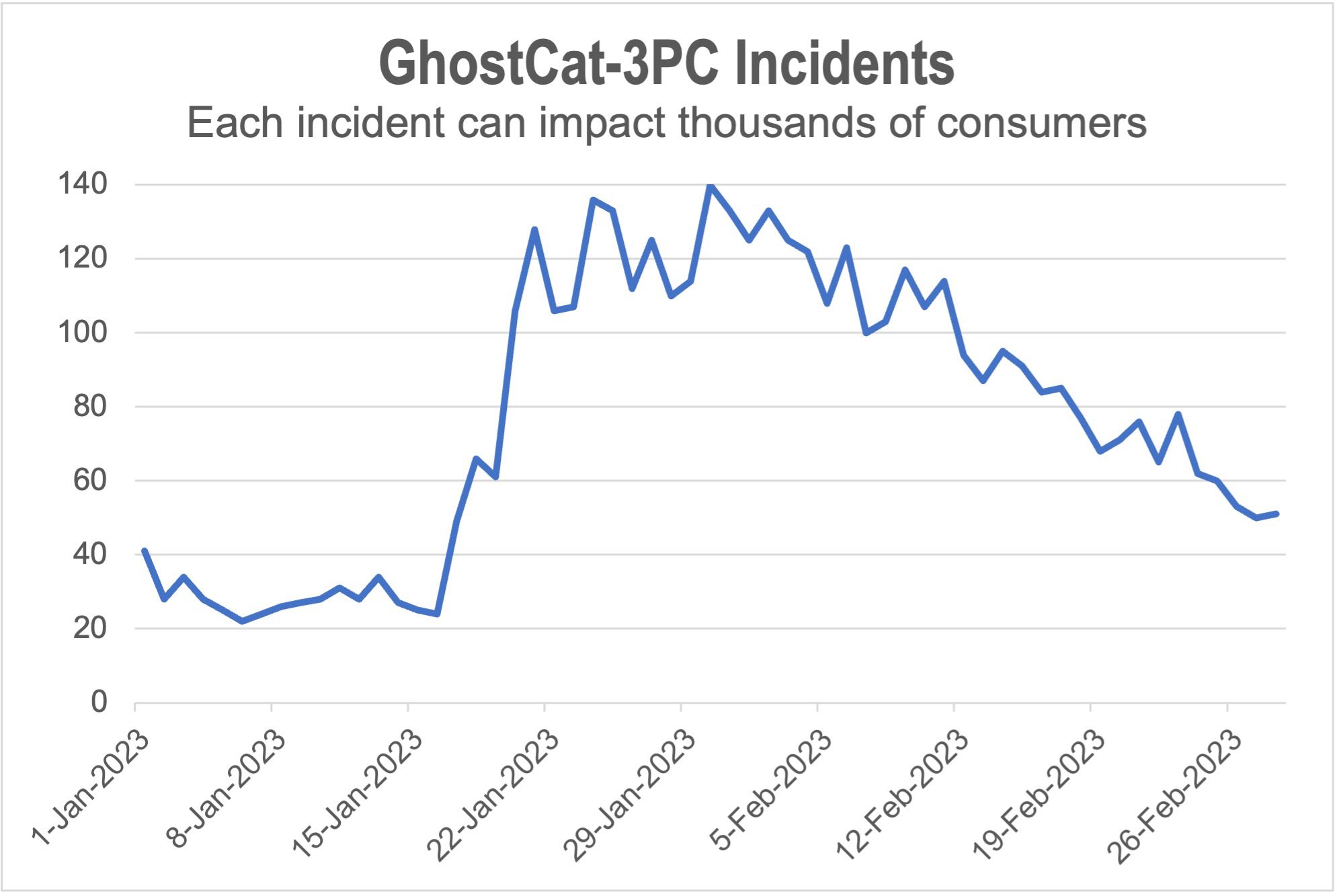
Figure 1: Appearing on several new ad platforms, GhostCat dramatically ramped up in mid-January for a sustained barrage that didn’t taper off until the end of February.
The number of GhostCat incidents increased by 2.5X between December 2022 and February 2023, while GhostCat blocks by Media Filter jumped by more than 15X over the same period. The redirects hailed from dozens of ad platforms and affected consumers on hundreds of premium publishers. Particularly worrisome, GhostCat was delivered through numerous new demand sources, highlighting that threat actors are expanding their reach and the breadth of the attack.
A Threat to Meet the Moment
Since 2019, GhostCat has been menacing the digital advertising space—Many specific incidents appearing in the February splurge have been lurking in the ad ecosystem for more than 600 days, with one approaching 1,000 days. The streamlined malware delivery device is highly targeted and infamously features no creative or landing page URL. A malicious payload (i.e., phishing redirect) only appears when GhostCat is served to a mobile device; when delivered outside that target, either nothing renders or a mysterious pink box appears.
To further avoid detection and domain-based blockers, GhostCat rapidly cycles through JavaScript in cloud storage rather than domains, making it all the more elusive to pin down. As noted during The Media Trust’s CYA 2023 webinar in January 2023 (where we warned of this imminent attack), GhostCat appears to be operated by threat actors with deep knowledge of ad industry workings—and vulnerabilities.
Which means they may have seen major tech layoffs as an opportunity to launch a sustained assault. It’s questionable whether this latest barrage was more painful and harder to shut down because security and marketplace quality professionals at ad platforms were among those downsized. This easily caused communication gaps within companies and between partners, hampering efforts to shut down outbreaks and enabling GhostCat to lengthen its assault.
Security Strategies
GhostCat will rise again; periods between major assaults are shrinking. And the threat actors behind GhostCats malevolent ways are actively looking for new avenues to attack consumers and maximize the spread of its mobile phishing attack. No ad platform or publisher will be spared.
Here are some key recommendations for detecting and shutting down this elusive malware before it wreaks havoc:
- Continuous analysis of ad creative. GhostCat’s operators will run innocuous campaigns for months to avert suspicion before switching in malware. Just because you checked an ad once doesn’t mean it’s in the clear.
- Analyzing ad creative from a variety of device profiles. GhostCat only deploys on mobile devices and, like many other contemporary threats, is quite good at detecting test environments. Scrutinizing from several different types of devices (real ones when possible!) will help lure the cat out of its hiding place.
- An on-page/in-app creative blocker with constantly updated malware blocklists. GhostCat rapidly cycles through JavaScript hosted in cloud storage. New JavaScript is appearing all the time, so your on-page/in-app creative blocker needs to be steadily fed the latest updates. Oh, you’re also going to need a crack malware team finding that JavaScript and updating those blocklists—3rd-party data ain’t gonna cut it with GhostCat.



