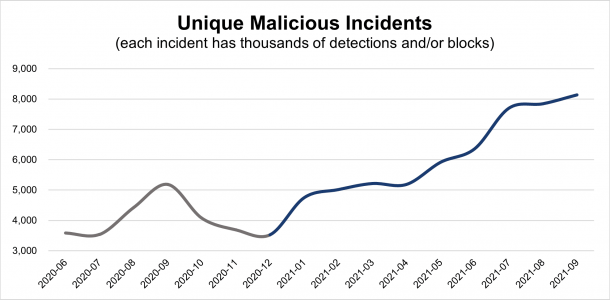
Heading into the busy holiday season, the digital ecosystem is rife with malware. September recorded 8,133 active incidents, a 4% increase over August and more than double the same period in 2020. Key incidents included a small surge in cloaking activity associated with Fizzcore incidents. Long the plague of Europe, these recent incidents mainly affected U.S. publishers.
Typically, malware dips in the final months of the year. This is primarily due to the increase in digital advertising spend which makes it too expensive for bad actors to deploy malicious campaigns. So what’s going on? Take heart; it’s not as bad as it looks.
- Rapid domain cycling: Attacks are quickly rotating through domains to evade detection and increase their chances of success. In some malicious campaigns we’ve detected the use of similar creatives of varying formats attached to 20+ domains in a matter of hours. Instead of launching an attack and modifying its parameters as it loses effectiveness (hitting consumers), some bad actors are trying dozens of domains at the start. An incident is created according for each malicious domain; the more domains in play, the more incidents created.
- Outbreak period decreasing: Incident lifespans are getting shorter. Brands/Advertisers are taking quick action to address malware on their pages and also the campaigns they place.
- Ads.txt enabling malvertising: Recently, malware has been concentrated among small media publishers with large Ads.txt files. With an aim to drive transparency and minimize fraud, Ads.txt is an advertising initiative where publishers list the providers that have authority to sell inventory (e.g., ad slots on a publisher’s page). Bad actors are gaining access to more publisher pages by placing campaigns with these Ads.txt providers.
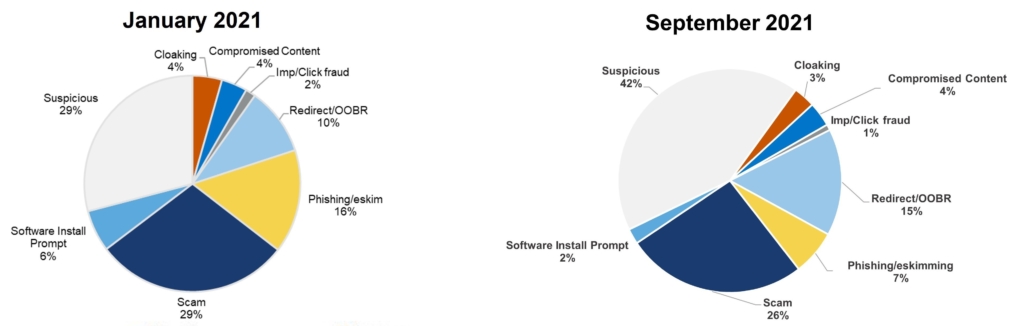
Malware Composition
As the year progressed, the consumer impacts have changed. As a percentage of all malware detected, the summer scam and phishing scourges appear to be abating. However, redirects and suspicious malware continue to grow. Don’t be fooled by the decrease in cloaking. These events are sporadic; several attacks occurred at the beginning of September and were quickly shut down by our Digital Security & Operations team working with the affected AdTech providers.