As malvertising advanced alongside Russia’s invading forces, AdTech platform Admixer heeded the call to protect Ukrainian citizens and infrastructure with the help of The Media Trust. Download the case study here.
Since February 2022, Russian forces have laid siege to Ukraine by air, sea, and land, with the death toll already in the hundreds of thousands. But the battle also rages online, as Russia employs an army of cyber soldiers to try and destabilize Ukraine’s infrastructure.
Some of these are well-known attacks such as distributed denial of service barrages, but one vector that repeatedly flies under the radar is the spread of malware through advertising pipes. It’s well known among cybersecurity experts that Russian government operatives moonlight as malware spreaders for profit, with the state looking the other way as long as the malevolence doesn’t affect Russia.
These state actors have brought their malvertising skills to assault Ukrainian citizens struggling to find some kind of normalcy while under constant threat. Phishing attacks, scams, and backdoors are all being employed to gain access to crucial personal data and devices in order to cause mass havoc—in the digital and physical worlds.
Often successful malvertising attacks will supply the login/credentials or the backdoor device access to fuel more drastic incursions such as ransomware. But Russia isn’t looking for a quick bitcoin payment—it aims to use malware to hold the whole of Ukraine hostage.
Ukrainian citizens are counting on digital publishers and platforms that distribute advertising to stop these threats before they hit screens in the besieged country. The stakes could not be higher: the future of Ukraine and the freedom of its people.
The Digital Bombardment of Ukraine
As Russian troops gathered on the Ukrainian border in late 2021, the cyber winds blowing throughout the digital ecosystem were whispering of a different type of war.
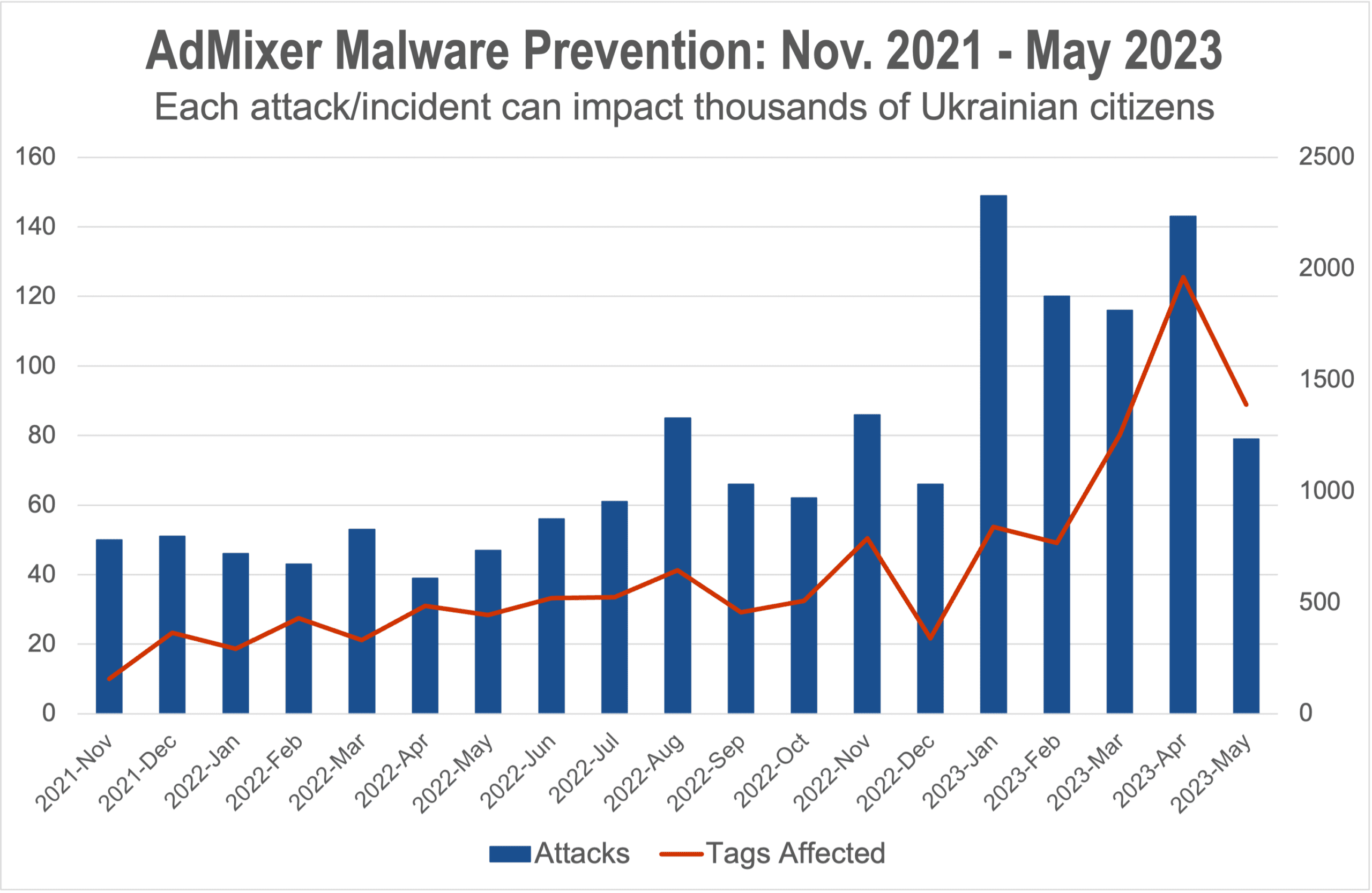
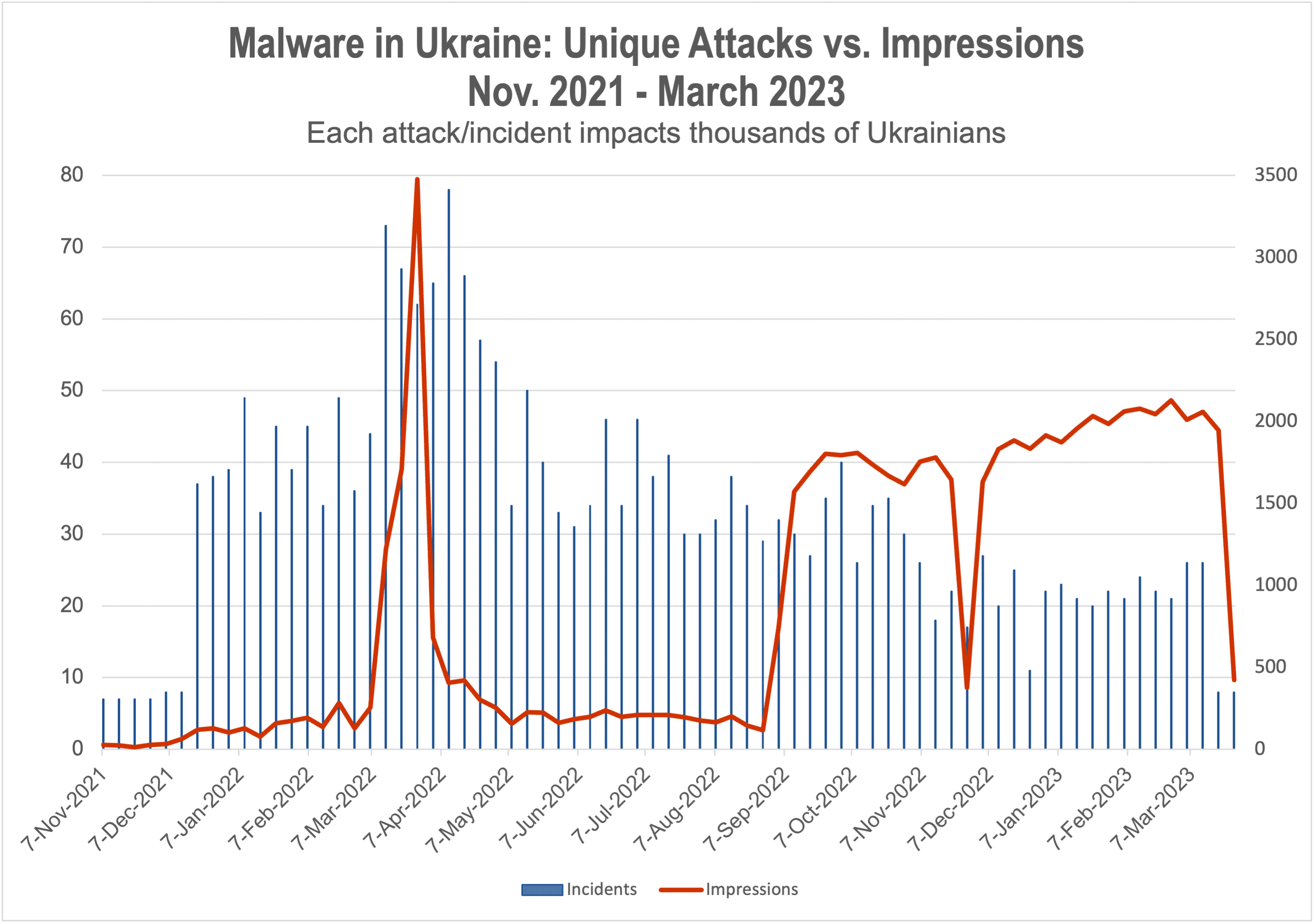
Digital trust and safety specialist The Media Trust, which has a long history of battling malvertising all over the world, detected a growing diversity of unique malware attacks. Monitoring high-traffic Ukrainian sites using devices and emulators within the country’s borders to recreate a citizen’s experience, The Media Trust tracked a 3.3X increase of incidents from November to January—specific, identifiable malware attacks or campaigns aiming to harm consumers via backdoors, e-skimming, scams, or phishing. Each incident can account for thousands of ads reaching millions of consumers.
This behavior is consistent with what The Media Trust considers “testing periods,” in which threat actors probe for vulnerabilities in the advertising supply chain by launching a variety of attacks and then determining which will be most effective. Testing periods are generally followed by volcanic eruptions in malware found on publisher properties—as what occurred in March and April 2022. (Figure 1)
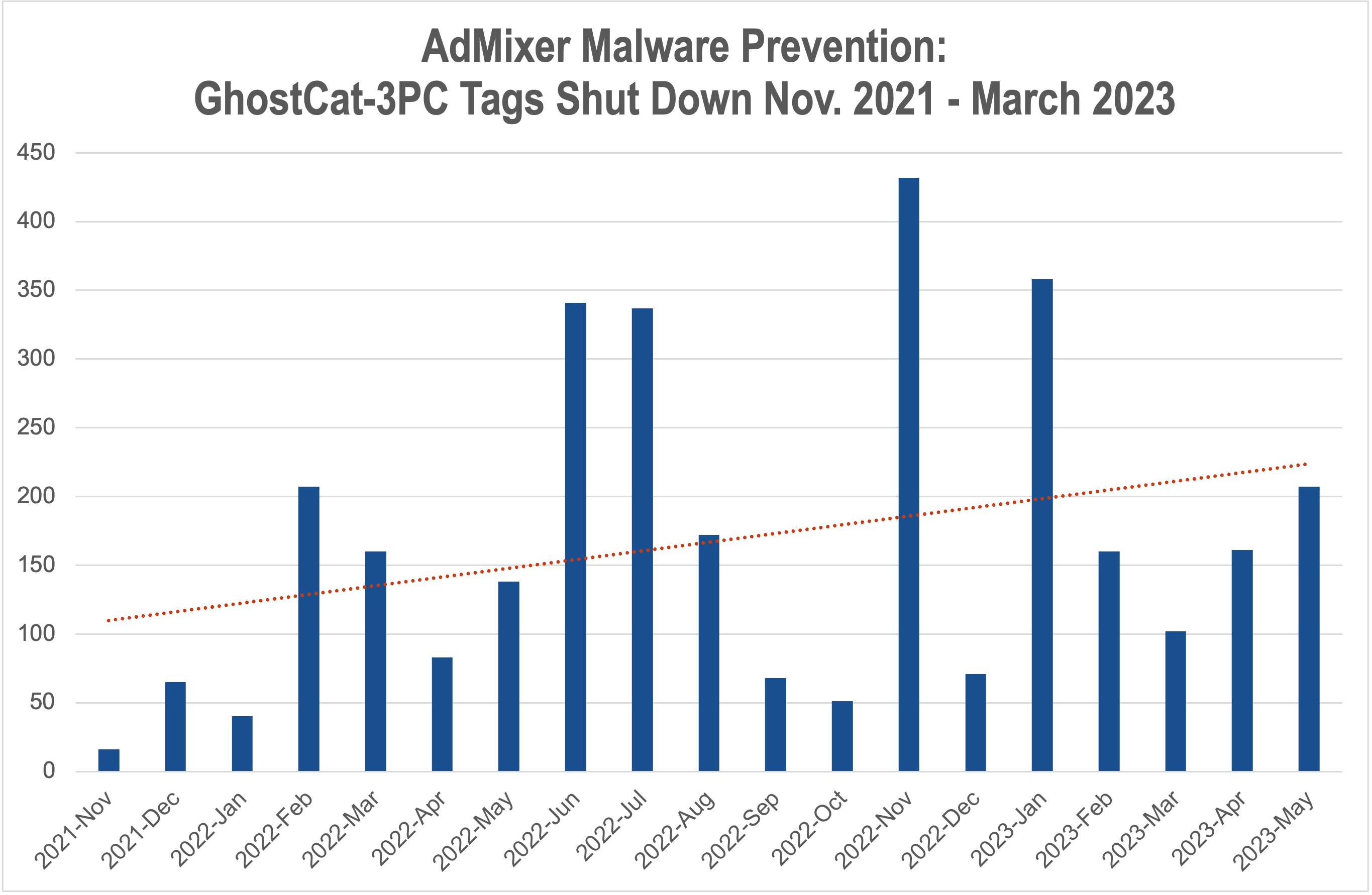
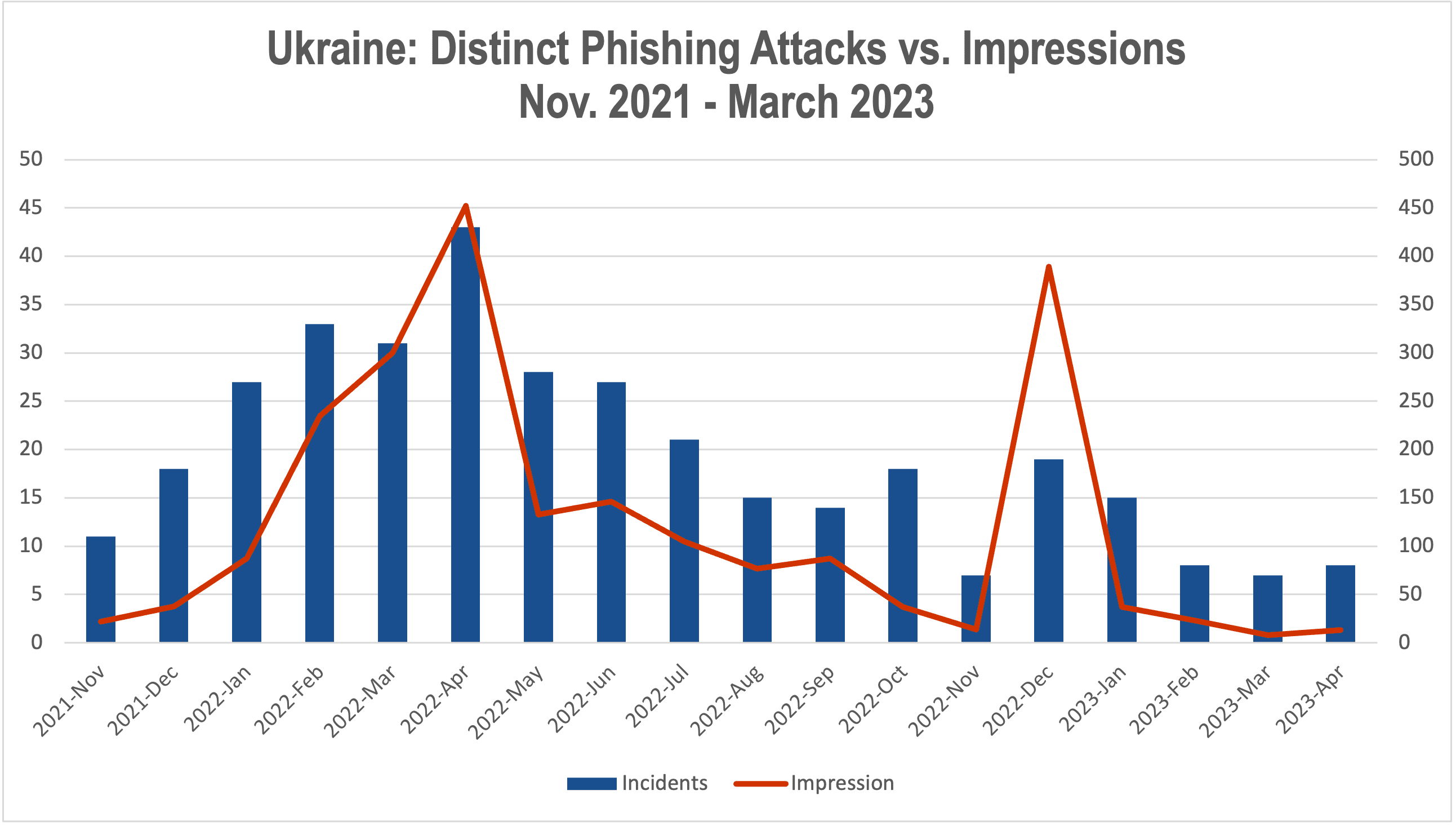
This barrage included high use of phishing campaigns (26% of all attacks), with prominent usage of Ghostcat-3PC, a highly elusive phishing attack aimed at mobile devices and seeking a variety of personal data. (Figure 2)
Distinct malvertising attacks decreased from their March/April peak as Ukrainian publishers and ad platforms enhanced their defenses, but the level remained elevated compared to 2021. However, as the Ukrainian army began retaking territory in the east, malvertising impressions found on publishers surged again and remains high to this day.
This latest assault features a narrower band of unique attacks but greater spread of malicious impressions, suggesting threat actors have found preferred vulnerabilities. In addition, this new barrage is dominated by backdoor attacks that hide unwanted programs opening device access to threat actors for future attacks.
A great deal of these new backdoors are driven by compromised websites such as named threats MimicManager-3PC and MudOrange-3PC that deliver popups and redirects—unbeknownst to the site owner. They are victims as well—many of them are small- and mid-sized brands that unknowingly spread malware in their own advertising.
Shielding Consumers From Malvertising
As a full-stack ad platform monetizing Ukrainian publishers in addition to ones around the globe, AdMixer understands the severity of the current situation. Despite the omnipresent dark cloud of war, life goes on in the Ukraine: citizens still consume digital content and purchase goods, often influenced by advertising.
AdMixer recognized its urgent duty to protect the Ukrainian citizenry from Russian threats—as well as publishers around the globe. At the aggression outset, we prohibited advertisers with a “.ru” A domain (as well as A domains from Russia ally Belarus).
Working with The Media Trust, Admixer developed a list of major Russian advertisers to disallow and increased scrutiny of ad tags sent by advertisers to the AdMixer demand side platform. This helped shut down threatening campaigns before they entered the digital ecosystem and hit Ukrainian devices.
The last item was accomplished by using The Media Trust’s global infrastructure of devices and extensive team of malware analysts to examine all ad tags, creatives, click-throughs, and landing pages. (Figure 3)
The results were dramatic:
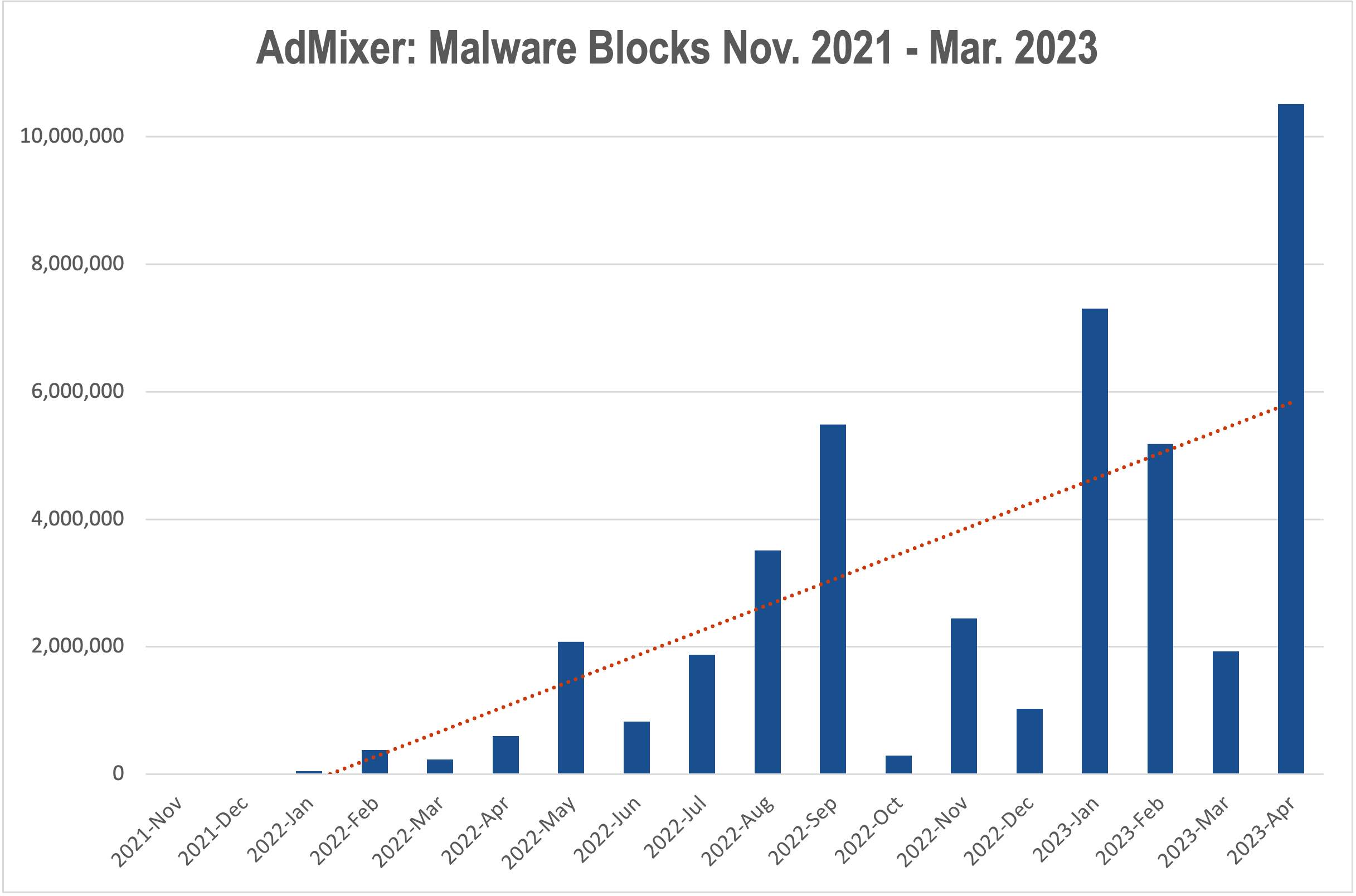
- AdMixer identified more than 12,485 malicious ads and prevented them from attacking consumers between Nov. 2021 and May 2023
- The number of tags with malware detected and halted has grown 11.5X
- The amount of unique malware attacks shut down increased 186%
- 63% of these halted ad tags were phishing attacks
AdMixer stopped more than 5,000 phishing tags from entering the programmatic advertising ecosystem and harming hundreds of thousands of consumers. At least 60% of these were GhostCat (Figure 4), a pernicious named threat that is particularly difficult to detect and stop because malicious creative (a redirect pushing a phishing scheme) only appears in the target environment: a mobile device.
In addition to leveraging clocking technology to hide their malicious intent, the ad tags feature no creative or landing page URL. GhostCat rapidly cycles through JavaScript malicious payloads stored in cloud storage rather than domains like other malvertising.
The work of ad platforms like AdMixer in quickly shutting down phishing attacks has forced threat actors to focus on other ways to attack Ukrainian citizens and other consumers, such as back doors via compromised websites.
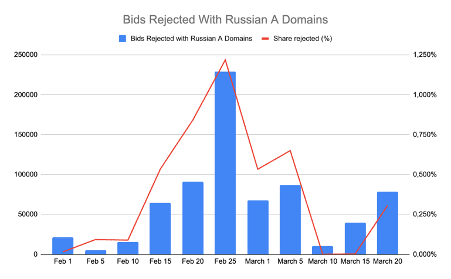
But AdMixer has an additional avenue for protecting consumers. By leveraging The Media Trust’s real-time ad blocking solution, Media Filter, in its supply side platform, AdMixer is able to further halt malware from third-party ad platforms from reaching publishers and ultimately consumers. Since Nov. 2021, AdMixer has blocked ~44 million malicious ads, a quarter of them phishing attempts. Blocks have increased 27X since the beginning of the Russian invasion in February 2022.
The Assault Continues
The first anniversary of the invasion on Feb. 24, 2023, coincided with a massive spike in advertising traffic from Russian domains. It seemed a clear signal that Russia’s cyberwarfare via malvertising would continue and even escalate with the ongoing conventional war. (Figure 5)
The fight against Russian malvertising—in Ukraine as well as the rest of the world—has only just begun, and companies like AdMixer need their fellow ad platforms to step up when it comes to malware prevention. And it goes beyond malware: state actors will also use advertising to push disinformation, and we’ve all learned how crucial information is in swaying the tides of war.
Here are straightforward steps for other companies to help the Ukraine on the digital battlefield:
- Prohibit advertising from Russian A domains, and also consider blocking those from chief Russia ally Belarus.
- When analyzing ad tags, increase your scrutiny of click-throughs and landing pages. Threat actors are increasingly using compromised websites (often those of advertisers, but sometimes publishers too) to deliver malware. Platforms not only need to stop ads attached to compromised websites, but inform the property owners, as they are often unaware they’ve been hacked.
- Share threat intelligence with other ad platforms. Platforms cannot view having less malware as a competitive advantage—consumers are still in danger, and a safer ecosystem is best for the industry overall. The Trustworthy Accountability Group’s Threat Exchange is a great channel for passing critical data on outbreaks big and small.
In the larger scheme of things, supporting Ukraine and protecting its people is crucial for pushing back against a global bully. The AdTech community needs to stand in unison—protecting Ukrainian citizens is about protecting digital consumers worldwide.

