As extreme temperatures scalded the US and other parts of the globe in June, a highly evasive malvertising threat was bringing the heat to the digital media ecosystem. StringRipper phishing redirects exploded in June 2025, growing 15X month over month and becoming one of the most prolific attacks ever identified by The Media Trust.
StringRipper poses a dire and evolving threat across the digital advertising ecosystem, impacting consumers, adtech platforms, and digital media companies alike. This malvertising is particularly insidious because it infects existing, legitimate ad tags, making malicious ads appear perfectly benign even under scrutiny.
It employs advanced obfuscation, dynamic function creation, and randomized timing to mimic genuine user interactions, making it exceptionally challenging for automated systems to detect. Its sophisticated multi-stage process and environment fingerprinting allow it to avoid security checks and disable tracking mechanisms by overriding critical global properties such as XMLHttpRequest and fetch.
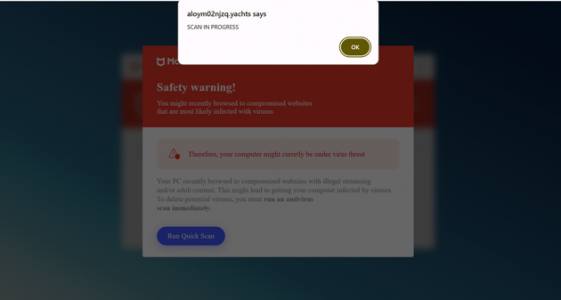
Ultimately, users are redirected to fake virus alerts — often spoofing trusted brands like McAfee — which trick them into downloading malware or revealing personal information.
Thousands of premium publishers and adtech platforms are fighting back against this pernicious threat daily. While at the beginning of 2025, StringRipper was being spread primarily by one DSP with a very large footprint; now it’s being delivereer in numerous The Media Trust has developed new techniques on the fly to identify this dreadful evolution in phishing delivery, while also employing advanced real-time mechanisms on publisher pages to halt redirects before they activate.
In-Depth Analysis
The Media Trust’s Digital Security and Operations team has assembled an in-depth report on StringRipper’s complicated execution. To avoid spreading valuable information to malicious parties, it is only available by request and with a verified email. (You must submit a company email to receive the report.)