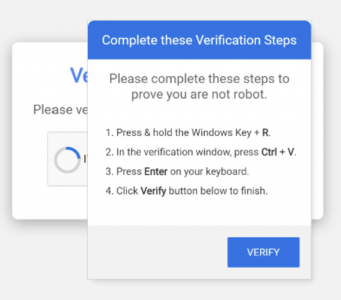
Human verification systems on websites may have long annoyed digital consumers, but they also have reason to fear them — or at least fake ones that could enable threat actors to steal their life savings.
A widespread malvertising attack dubbed ClickFix uses a bold new bogus CAPTCHA scheme to trick vulnerable consumers into running scripts that give remote access to attackers. These threat actors can then execute a variety of malicious programs to steal credentials and cause maximum financial harm.
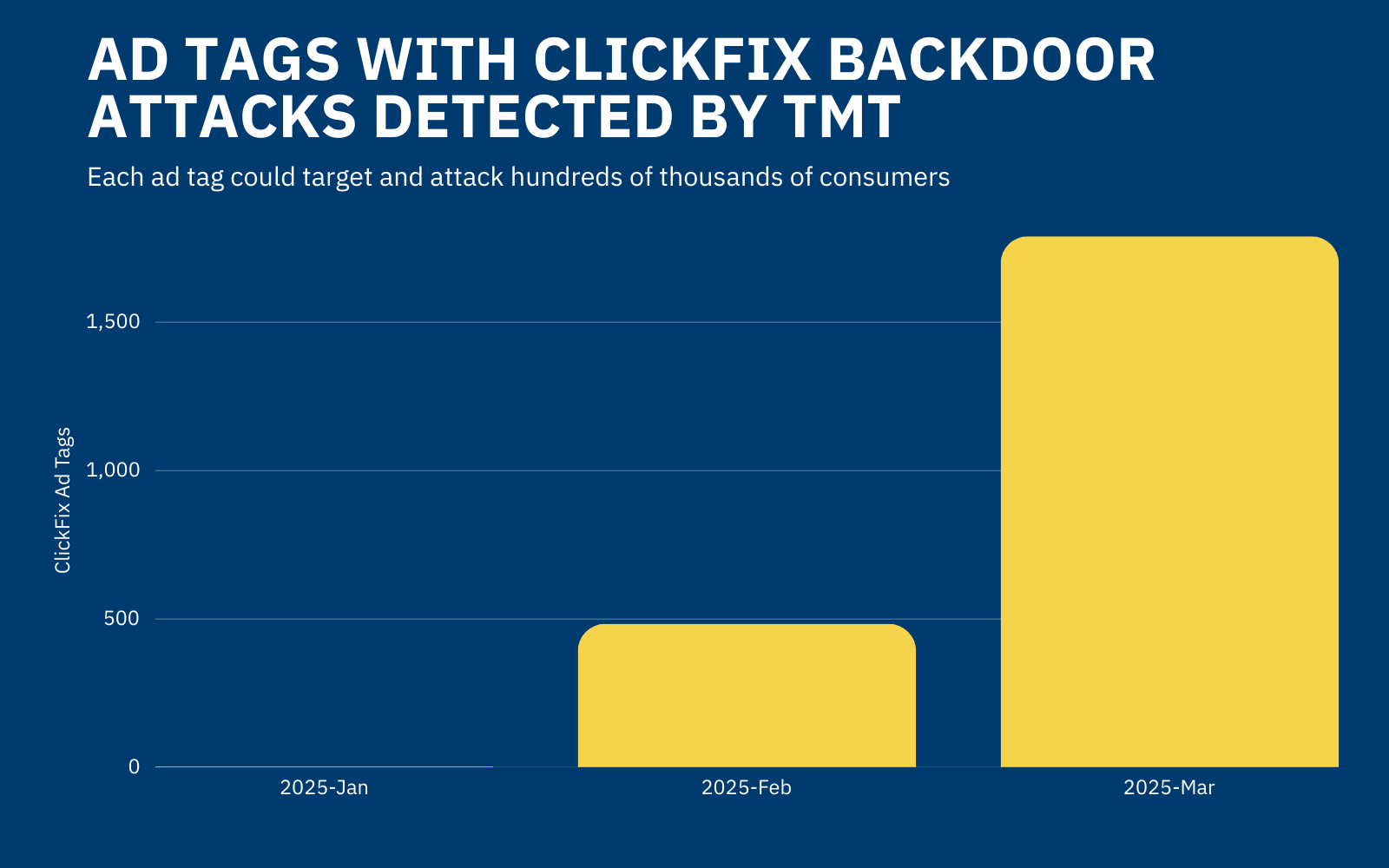
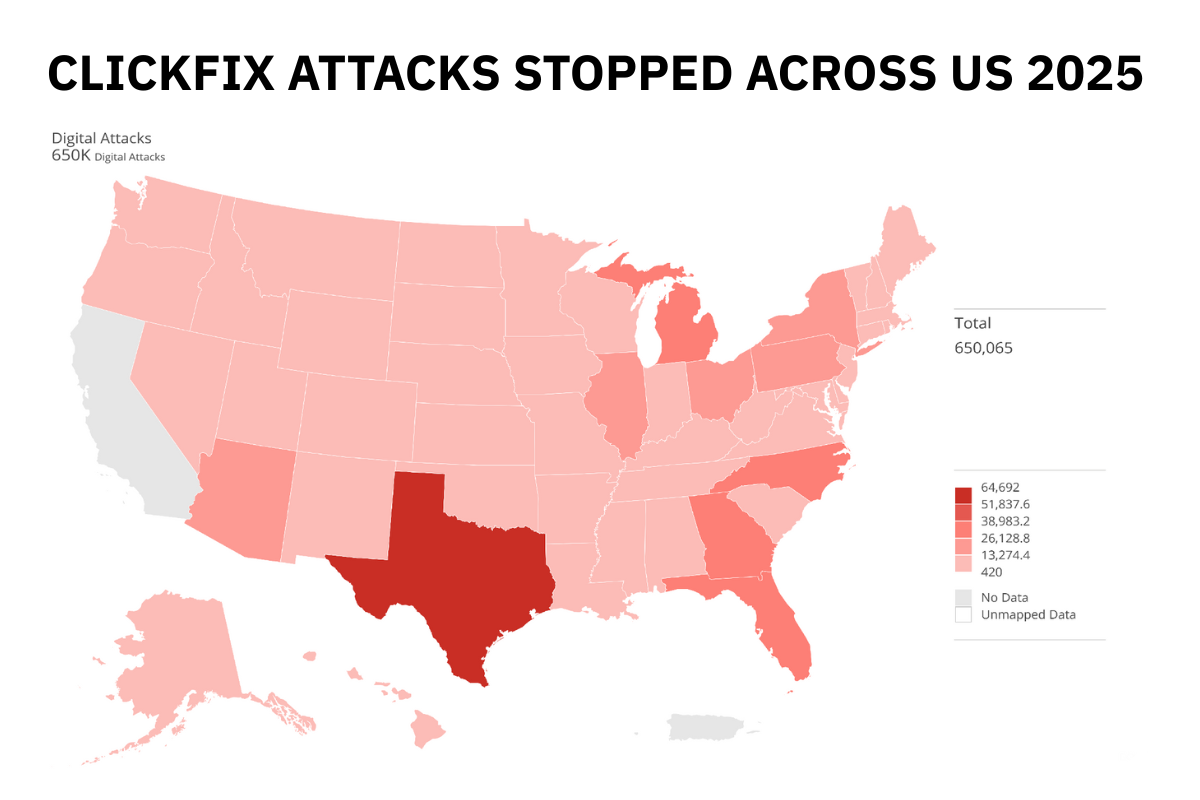
The number of ad tags with ClickFix backdoor attacks skyrocketed 3X+ in March 2025 versus the month before, and the malvertising has been halted from assaulting consumers 600K+ times across hundreds of websites globally.
Multiple Avenues to Mayhem

ClickFix leverages a variety of tactics to lure consumers to fraudulent CAPTCHA pages:
- redirection from innocuous ad creatives
- compromised brand/media websites
- sites using typosquatting to mislead consumers
The malicious code first analyzes the user’s browser and operating system and then redirects them to a payload domain tailored to the target’s environment for maximum effectiveness. Upon redirection, the user encounters a fake CAPTCHA verification page designed to appear legitimate.
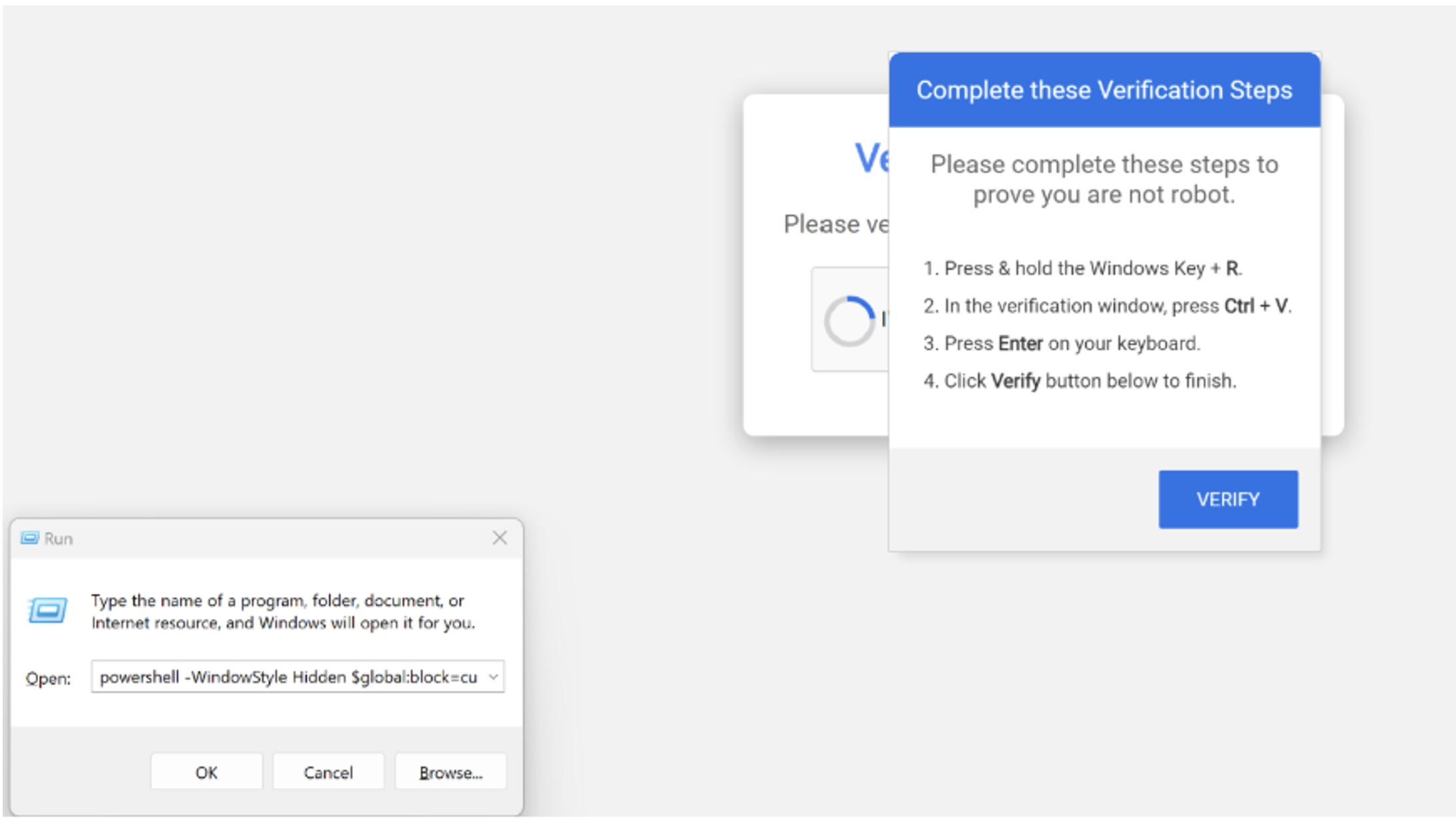
However, instead of selecting images or solving a typical puzzle, the page instructs the user to follow a specific sequence of actions:
- Press Windows + R (opening the Windows Run dialog).
- Press Ctrl + V (pasting a command that was silently copied to their clipboard).
- Press Enter (executing the command).
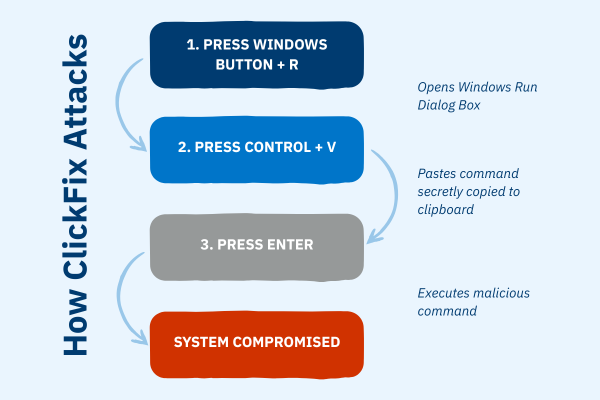
This deceptive process mimics a routine security check, making it particularly effective against less tech-savvy users who may comply without suspicion.
Social Engineering at Its Deadliest
Unbeknownst to the user, the script has already initiated remote code execution (RCE). The command silently retrieves and runs PowerShell instructions, effectively handing over control of the system to the attackers. This foothold allows for the seamless deployment of secondary payloads, including LummaStealer—a highly evasive and dangerous infostealer designed to harvest credentials, financial data, and other sensitive information with ruthless efficiency.
Unlike traditional attack vectors that rely on tricking users into opening malicious documents, enabling macros, or running disguised executables, this attack is a classic example of social engineering. By presenting this seemingly harmless CAPTCHA, the attackers manipulate the victim into unknowingly executing the malicious script themselves, eliminating the need for overly technical, exploit-heavy delivery methods and ensuring a seamless infection.
ClickFix highlights a sophisticated and rapidly growing social engineering tactic that is gaining traction in the malvertising landscape. Threat actors are manipulating users into executing malicious commands themselves, making detection and prevention significantly more challenging.
Defending Against ClickFix
The attack’s broad scope and widespread impact extend across various industries, affecting businesses of all sizes—including corporations, local enterprises, newspapers, and publishing outlets. The deployment of info-stealer malware presents a severe threat to individuals, their families, and their businesses, leading to proprietary data theft and significant financial consequences.
As malvertising campaigns grow more complex, a proactive, multi-layered defense strategy is essential to safeguard both users and businesses from financial loss and reputational damage. Protecting consumers (and businesses) from ClickFix requires actions across the digital advertising ecosystem:
- Advertisers need to perform regular monitoring of their sites through a variety of devices and personas to find hidden threats. They must constantly update plugins, especially if using an open-source CMS like WordPress, as this is a primary method for infecting digital properties.
- Adtech platforms need to scrutinize ad tags, creatives, clickthroughs, and landing locations for threats from a variety of devices (particularly Windows OS) and personas to unearth cloaking and compromised advertiser landing pages.
- Publishers need to ensure their upstream adtech partners are checking for cloaking technology and scrutinizing landing pages for hacked websites. They should also deploy real-time on-page/in-header malware blocking with blocklists continuously updated by security professionals.
Read more ClickFix analysis—including the PowerShell commands used to secretly copy code to user clipboards—from The Media Trust’s Digital Security and Operations team in the report below. (Please share your company email so we ensure this data does not fall into the wrong hands.)