It looks like just another ad tag, with a basic banner image and minimal HTML. The creative seems innocuous enough — a no-name fashion brand broadcasting new arrivals or a clearance sale.
But that’s how PopCrawler infests the digital media ecosystem — appearing so boring and plain as not to set off any alarms. A virtual wallflower on the media landscape — only one with malevolent intentions. Once this prolific new phishing attack starts redirecting consumers to bogus reward sites and even tech support scams that can liquidate bank accounts, the sirens begin to blare.
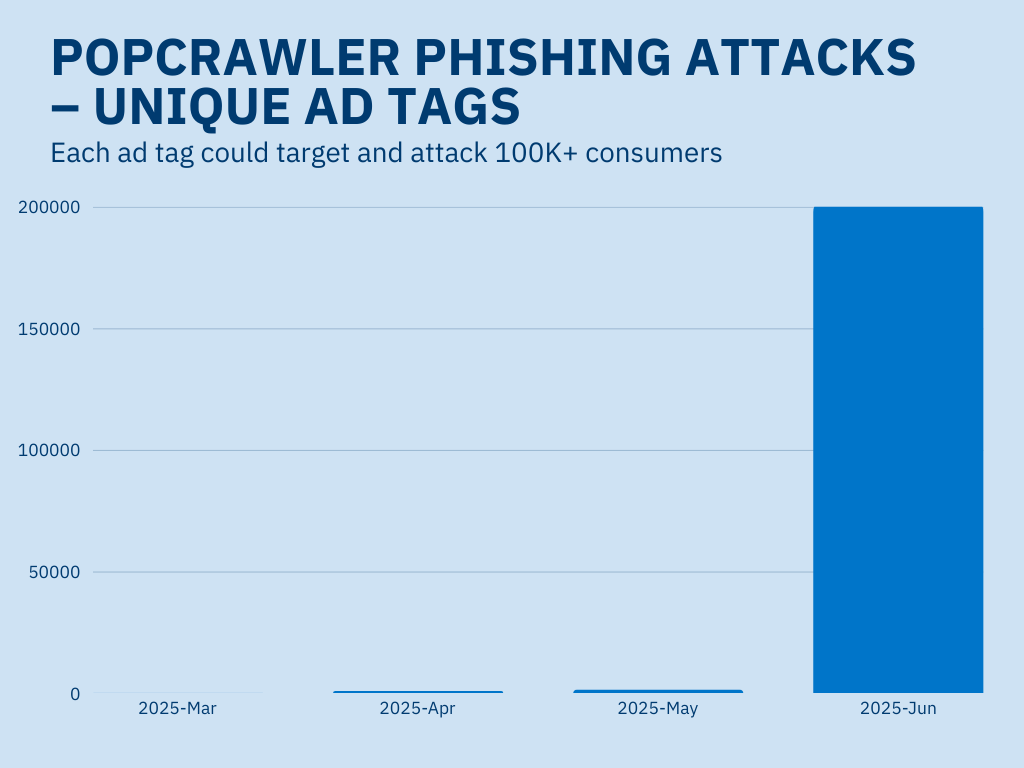
While The Media Trust’s Digital Security and Operations team found a growing number of unique outbreaks across a small amount of ad tags throughout this year, this changed dramatically in June 2025. The amount of ad tags wielding PopCrawler phishing attacks exploded, growing 12.5X month over month — 200,000 malicious ad tags affecting thousands of premium publishers and adtech platforms.

Resilience Through Fingerprinting and Adaptive Behavior
Unlike the pervasive StringRipper phishing attack that has grown dramatically in 2025, PopCrawler’s evasion techniques are surprisingly unsophisticated. Its alarming spread can be attributed to strategic use of fingerprinting, redundancy, and adaptive behavior to bypass common security mechanisms.
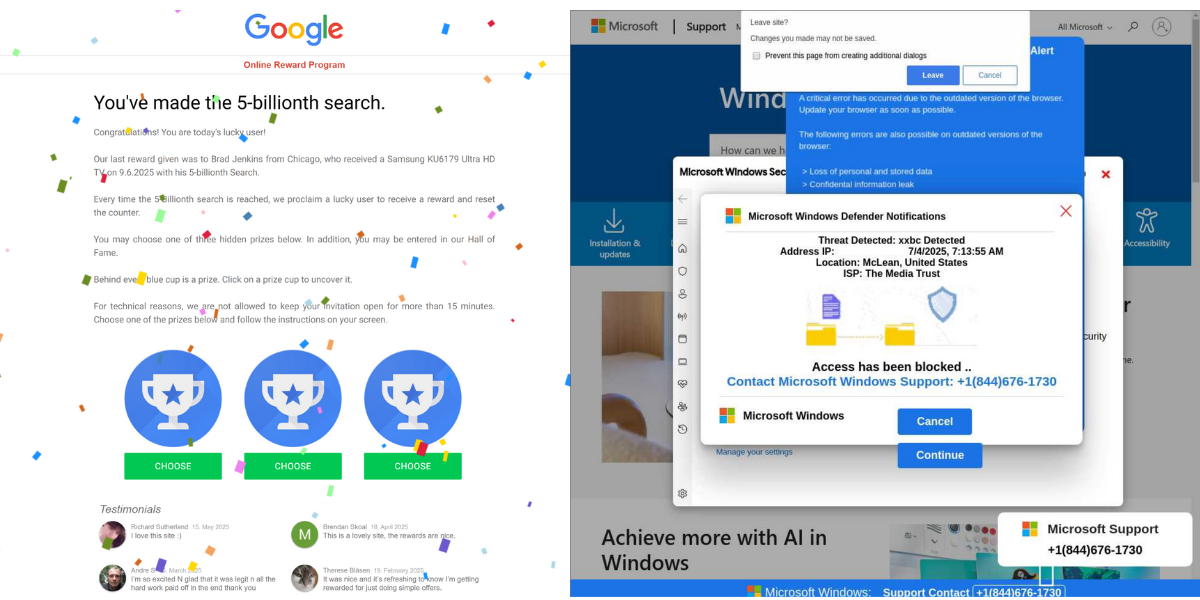
The attacker’s use of multiple redirect techniques, combined with optional Base64 encoding and layered delivery methods, makes the threat particularly resilient and difficult to detect. The inclusion of fingerprinting data in the redirect URL also enables server-side filtering and targeting by the attackers.
The Media Trust’s Digital Security and Operations team has assembled an in-depth report on PopCrawler’s deviously clever execution. To avoid spreading valuable information to malicious parties, it is only available by request and with a verified email. (You must submit a company email to receive the report.)

