It’s an old malvertising trick to slip excess, unwanted code alongside a creative in an ad slot. While those bad actors are typically trying to drop various types of malware, The Media Trust detected a campaign that drove a video ad fraud scam nearly 5,000 times across more than 10 third-party AdTech providers since April 2021 that affected dozens of popular mobile apps.
Malvertising and ad fraud often seem like two sides of the same coin, and this recent campaign shows how the tactics of the former can fuel the latter. Dubbed VidLox-3pc (VidLox), this malware-driven ad fraud campaign uses a fake creative—typically repeating the logo of well-known social, gaming, or streaming apps—and injects multiple tracking URLs to generate at least 25 non-viewable impressions for in-app video ad campaigns. The fake impression reporting is delivered to at least 10 demand and supply side platforms (DSP, SSP). The campaign relies on extensive obfuscation to successfully bypass creative blockers in multiple app environments to divert ad spend from legitimate AdTech and publishers.
In-app video is a hot market, with eMarketer estimating more than $18 billion in US ad spend alone in 2021. That kind of cash attracts bad actors—according to DoubleVerify, in-app video fraud has jumped 50% in the last year and accounts for about 2% of all in-app video impressions globally.
How VidLox enables video ad fraud
Legitimate ad-supported mobile apps are the campaign target. When users in the US, Canada, Germany and Spain access an app serving this campaign they will see an innocuous creative featuring well-known app logos like those from Hulu, SnapChat, and SoundCloud. [Figure 1]
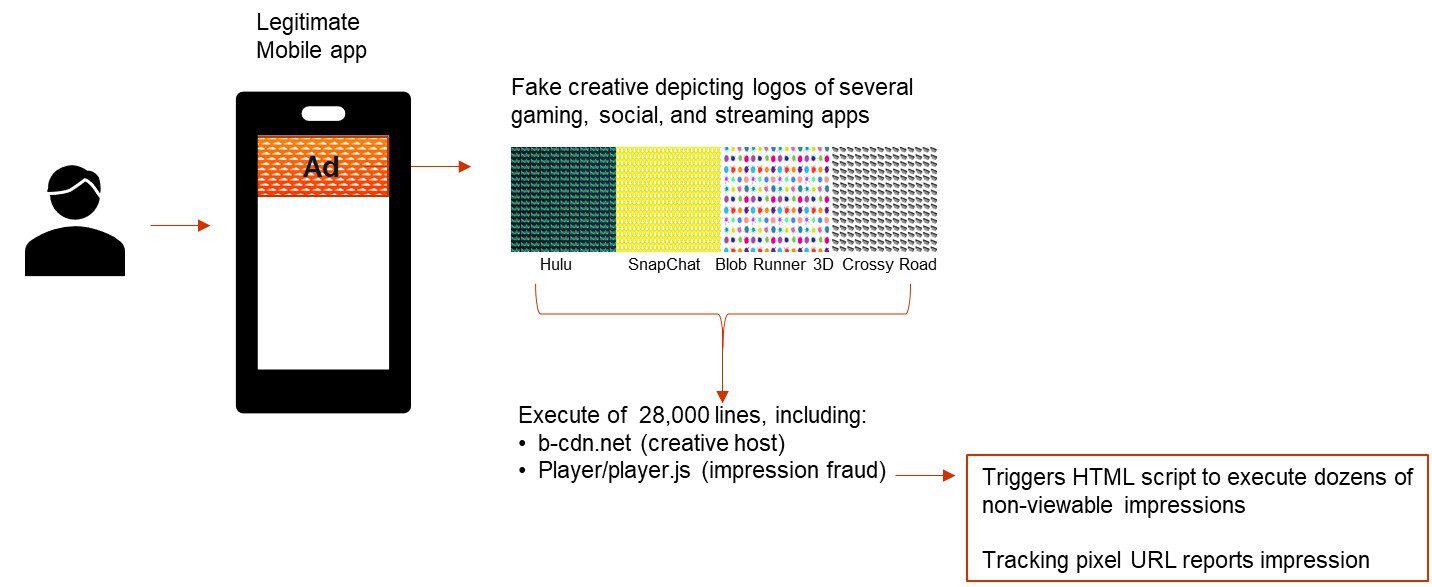
Behind the scenes, the VAST (primarily) and HTML5 tags contain an ad serving URL that delivers inline JavaScript with more than 28,000 lines of code and advanced levels of obfuscation. Within this code are two anomalous URLs enabling the impression fraud:
- one contains the string “.b-cdn.net”, which hosts the compromised creative
- another contains “/player/player.js,” which delivers the impression fraud URLs.
There are more than 30 different domains used in the delivery of these non-viewable impressions (aka, indicators of compromise, IOC), making it difficult to keep creative blocking tools updated. Fake impressions are being recorded for more than 20 apps including Trivia Crack, CBS Sports, and Pin Rescue.
VidLox isn’t over
The campaigns slowly emerged in April and then rapidly grew in mid-May. [Figure 2] The campaign cycle through domains and creatives to evade detection as our team worked to identify the bad actor and isolate the three primary DSPs trafficking the campaigns.
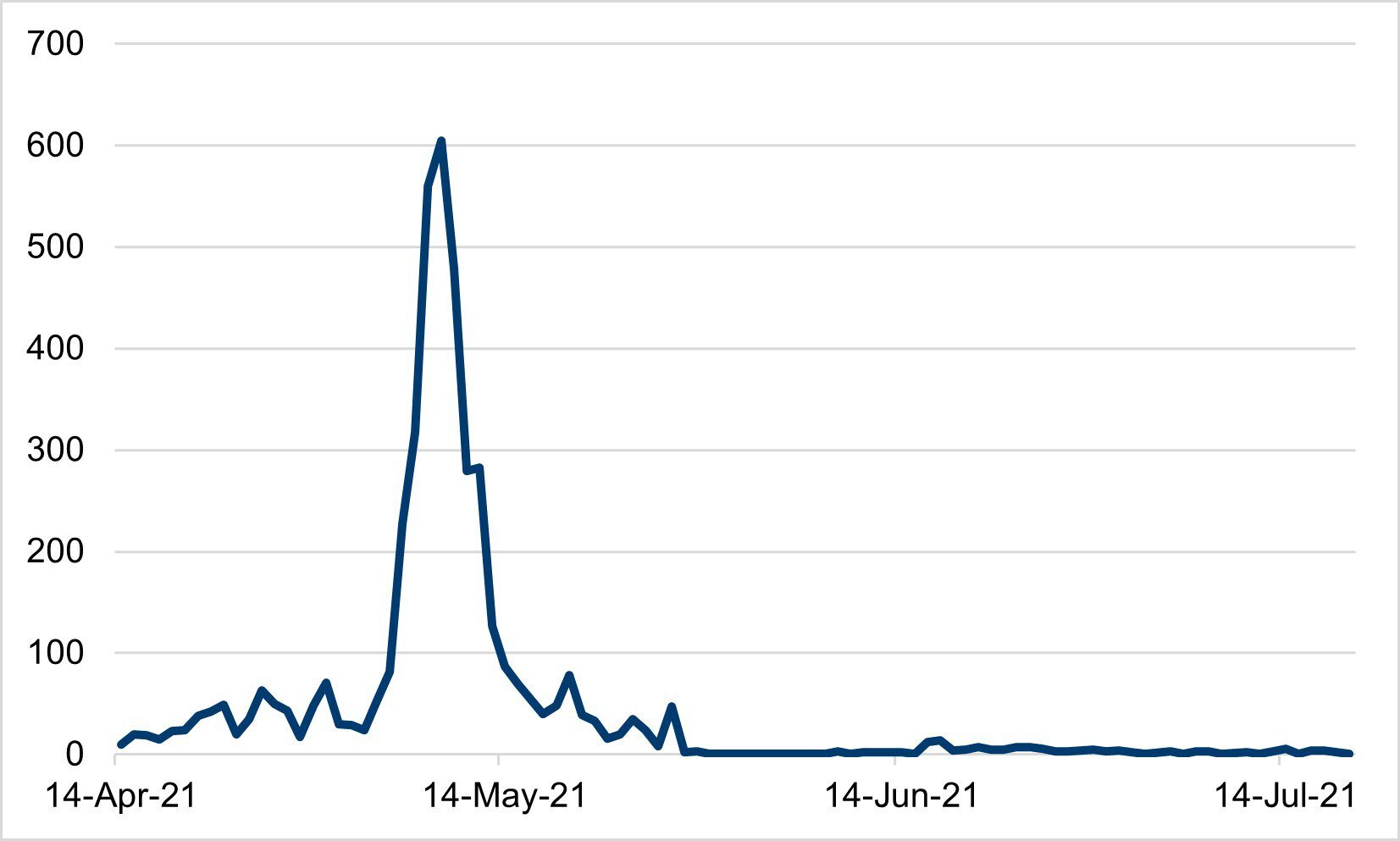
The campaign lingers with multiple detections every day; however, the bulk of the attack has subsided for now. While the campaign does not currently appear to be directly harming users, the compromised domains could easily be repurposed to deliver malware—e.g., redirects, phishing, drive-by downloads, etc. It’s happened before.
Say No to Malvertising-enabled Ad Fraud
Adware is frequently a precursor to malicious activity, often leading to issues across the broader cyber security spectrum like phishing and placing backdoors on devices that lead to ransomware and keystroke loggers among others. In this example, VidLox exemplifies how malvertising tactics fuel ad fraud.
Key tactics to thwart this type of ad fraud:
- Real-time client-side monitoring to capture evolving threats
- Blocking of known malicious domains and associated creative
- Share details with upstream partners to terminate the bad buyer, not the partner
AdTech companies and publishers should avoid playing a part in this impression-fraud scheme by blocking the campaign. As the speed of domain cycling makes in-app blocking difficult, The Media Trust recommends discussing with your upstream partner to ensure policies are followed. Otherwise, spend is being diverted from legit AdTech companies and publishers. The consequences of letting VidLox through the pipes is higher than it seems.
Summary
- 3 DSPs are the primary entry point of the campaigns into the digital advertising ecosystem*
- 30 domains/ IOCs used to host the malicious content including:
/player/player.js?p
0748bb5a7517492.b-cdn.net
64ab13125ce14d6.b-cdn.net/58d8825d-6b70-42d4-a815-5c676b101551.js
8f203032-ffdc-47ca-b1b2-73c7b295daad.js
aiserver.xyz
analyticad.xyz
analyticapp.xyz
analyticbidder.xyz
auctionservem.xyz
bidad.xyz
bidbidder.xyz
bidlog.xyz
bidservious.xyz
echorock.xyz
getparallax.xyz
infinitehub.xyz
openwrd.com
reportermarket.xyz
servious.xyz
sourceai.xyz
topvidsrv.com
tryelement.xyz
trytap.xyz
useecho.xyz
useulti.xyz
- 28k lines of code obfuscate the malicious activity
- 25 false impressions recorded, on average, per served ad
- 20+ apps recorded as receiving impressions including:
Brain Master
Bricks Ball Crusher
CBS Sports
Drawing Games
Escape Jail
Food Games
Harmony Melody Mirror
Home Design Makeover
Pin Rescue
Toilet Games
Trivia Crack
What the Forecast
Widgetpet
Words of Wonders Crossword
- 10 SSPs/DSPs had non-viewable impressions reported*
- 5,000+ detections of this malicious activity since April
NOTE: The Media Trust directly notifies affected AdTech and publishers; we do not publicly release their names unless they are unresponsive and the malicious activity continues unabated.
Download: VidLox technical analysis

