Authored by Michael Bittner, Digital Security & Operations Manager
A growing number of consumers have sworn off cash and credit cards for the convenience and perceived security of digital wallets. A recent malvertising campaign involving Apple Pay should make them think twice about their rush to judgement. In mid-November, the Digital Security & Operations (DSO) team helped the client, a winner of several Pulitzer Prizes and one of the largest daily newspapers in the West Coast, thwart a large-scale phishing and redirect campaign targeting iPhone users visiting premium newspapers and magazines.
The malware, referred to by the DSO as PayLeak, is disguised as a legitimate ad. When a newspaper or magazine visitor clicks on the ad, the malware will call to a malicious domain registered in China and check the visitor’s device for the following conditions:
- Whether in motion or at rest
- Whether upright or lying down
- Whether the browser platform in use is any of the following: Linux x86_64, Win32, or MacIntel
- The presence of specific malware detection technology
- Whether the device is an Android or iPhone
Android Devices
If the device is an Android, the user is redirected to a phishing site congratulating the user for winning an Amazon gift card.
Apple Devices
If the device is an iPhone, the code checks whether the device supports Apple Pay. It does this by creating an Apple Pay session object then calling the function “canMakePayments,” which determines whether Apple Pay is supported. If it is, the code takes a rare, deeper dive with the following succession of steps:
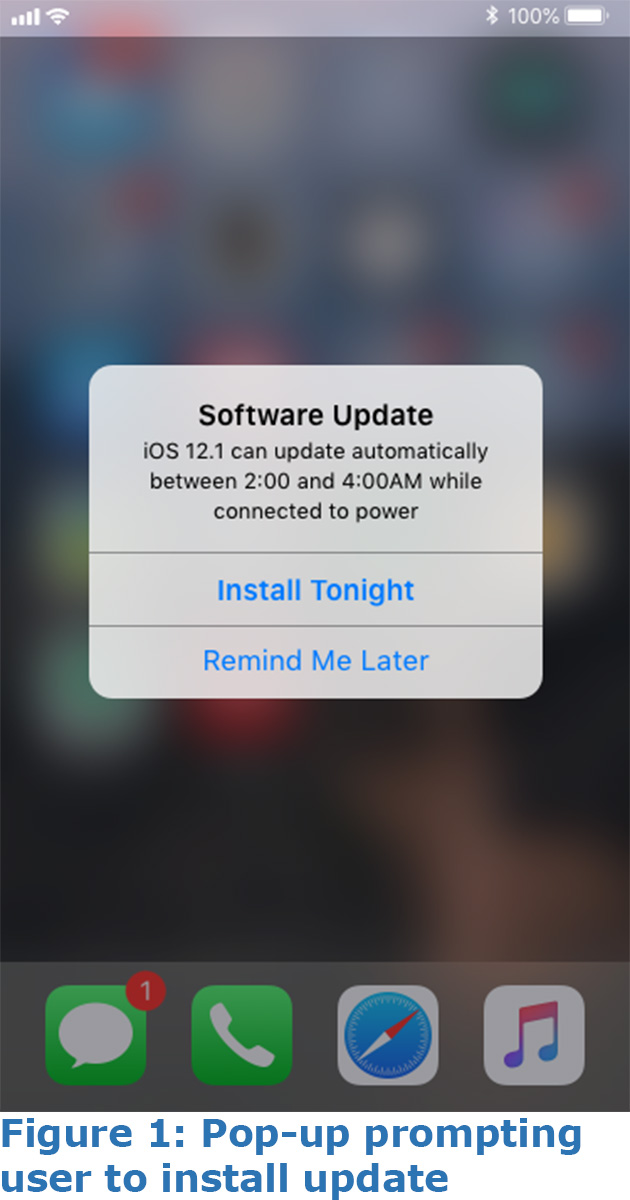
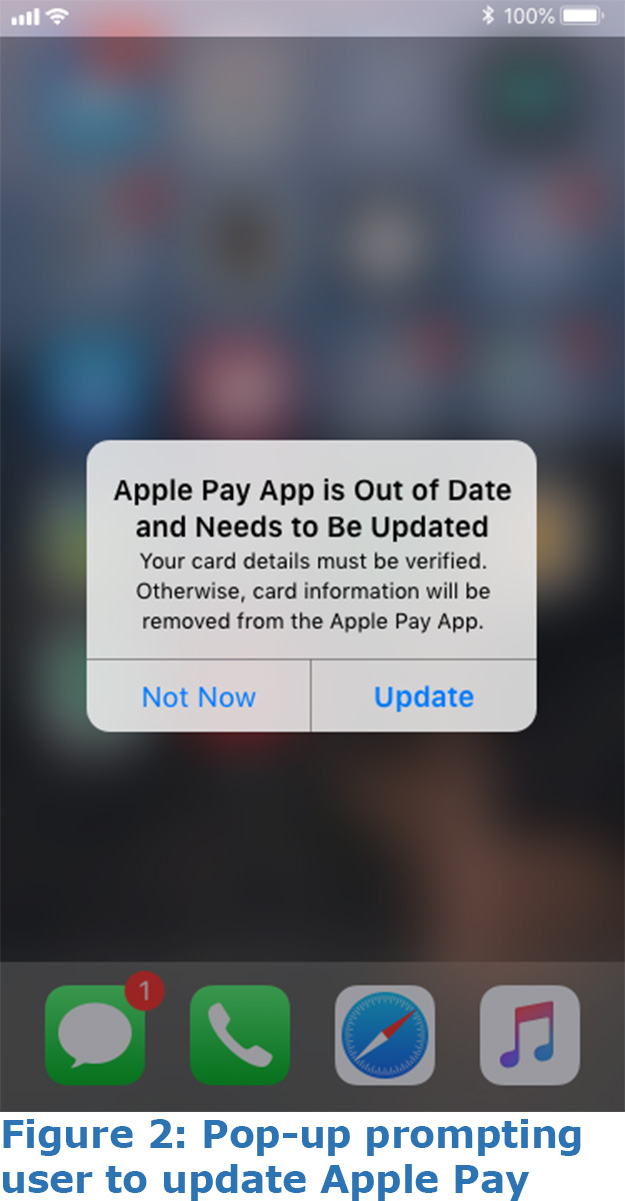
- The user receives two successive popups: one indicating the device needs updating (see Figure 1), and another indicating the Apple Pay app needs updating (see Figure 2).
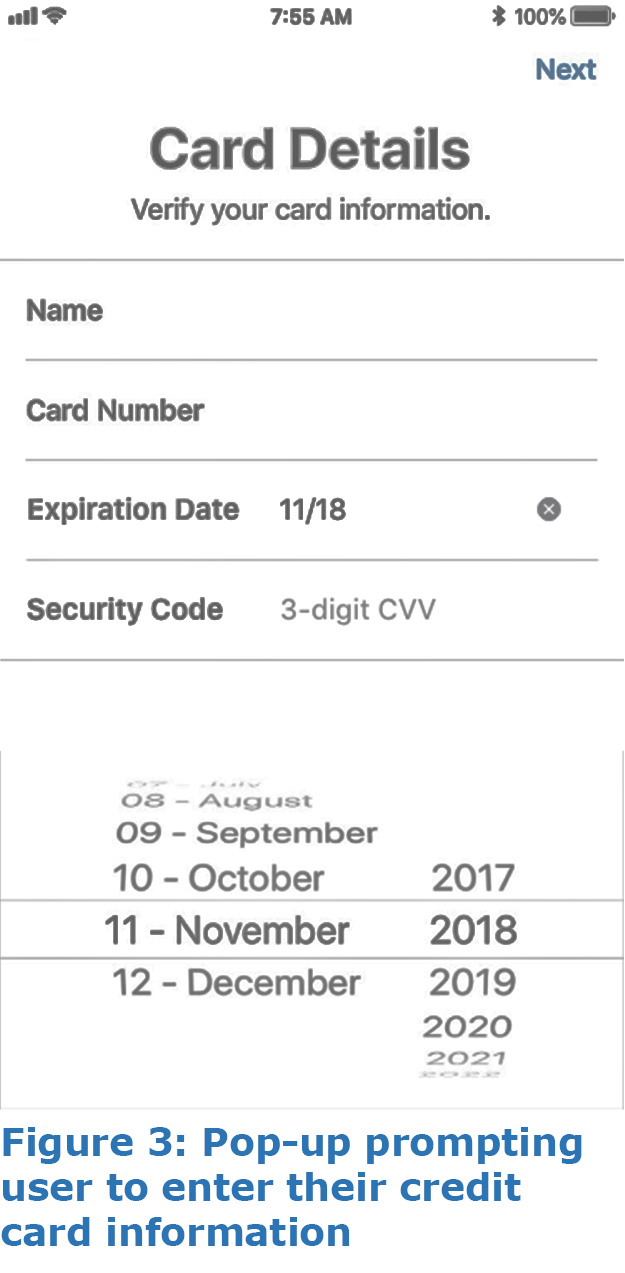
- A screen (see Figure 3) almost identical in appearance to that of the Apple Pay credit card information screen prompts the user to enter their credit card details.
- The malware logs the credit card information, device information, iOS version, IP, etc. and sends it back to a malicious command and control server. This information can potentially be used for a future man-in-the-middle attack.
This detailed, multistep method of defrauding users of a widely used digital wallet like Apple Pay is new. Previously identified attack methods involved intercepting transaction traffic between an Apple device and the Apple server. The use of an ad to infect devices gives bad actors more bang for their efforts: it enlarges the scope of the attack and makes it easier to escape detection by conventional anti-malware solutions and most commercial blockers.
Days before the attack on visitors of the online newspaper, the DSO had flagged the malware for its use of an obfuscation pattern the team had detected in previous malware incidents, and added it to The Media Trust’s real-time, original source malware data. Using The Media Trust’s Media Filter, which makes use of this data, the client was able to catch the malware and prevent it from executing in their digital ecosystem.
Other clients using alternative malware blockers were immediately notified of the attack, so they could in turn alert providers that the malware had slipped past their blockers, as well as terminate the source of the malware within their environment. But targeted sites with weaker security measures, such as those that do not monitor their digital environments for unauthorized code, could risk leaking their users’ sensitive information and leave the latter exposed to future attacks.

