ID syncs between websites and AdTech partners expose a growing malware vector
Key Learnings
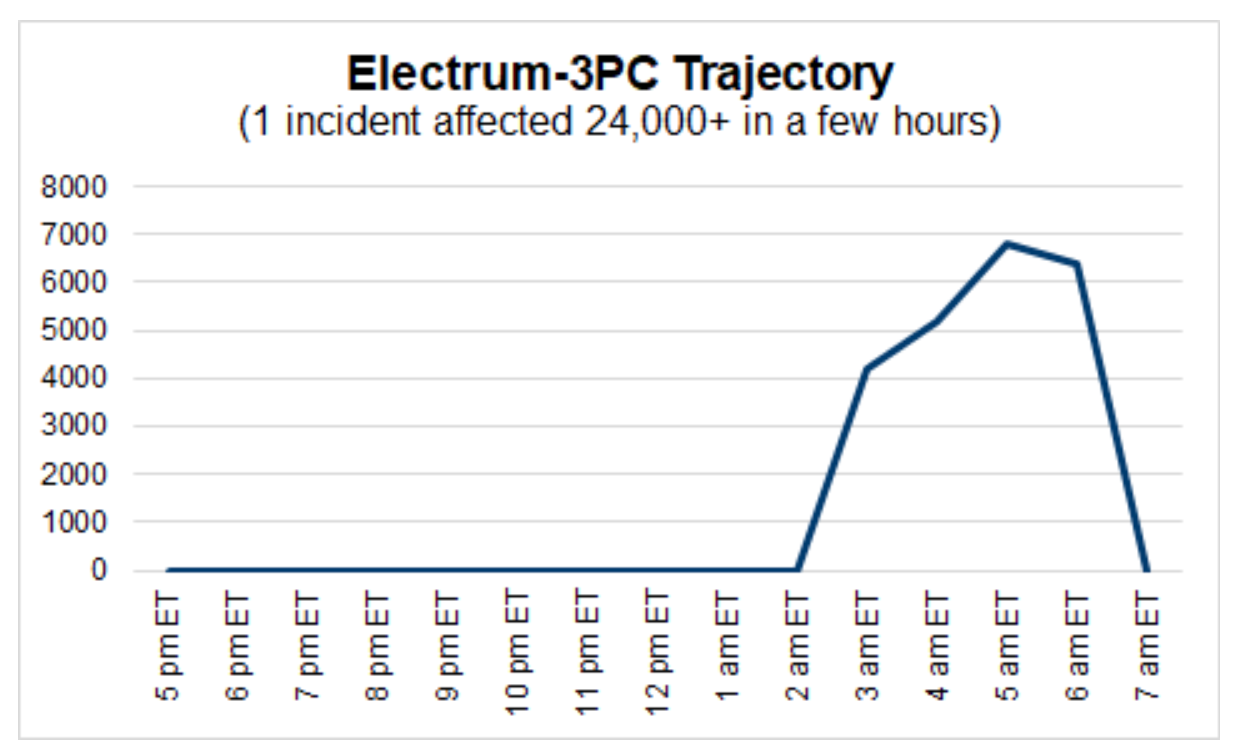
- 24K+ malicious events detected in four hours, encompassing 450+ publishers and Ad Tech providers
- Malware delivered through user sync URLs, not ad server
- Challenges in both identifying attack source and mitigating with creative blocker
Recommendations
- AdTech: Be vigilant in cleaning your code, and swiping out partners no longer in business
- Publishers: Ensure user and pixel syncs in headers are up to date and employ constant site and landing-page scanning to detect potential breaches
In the last six months, threat actors have been deploying malicious code—from phishing redirects to adware—not through ad servers, but ID syncs between websites and their AdTech partners. These attacks are not limited to ad-supported publishers—advertiser landing pages are infected with malware when performing user syncs with their AdTech partners.
Mid-February brought a brief and brutal malware attack dubbed Electrum-3PC. In the span of four hours, this malicious code appeared more than 24,000 times and affected 450+ publishers and AdTech providers (See Figure 1).This malware was completely detached from the ad server, with the malicious code delivered through the ID sync URL of an SSP with a compromised partner.
Anatomy of a hijack
ID syncs are common tools for media publishers to match user identifiers with their AdTech partners, including SSPs, DSPs, and DMPs. Most commonly performed with cookies, many ID syncs are managed with a dedicated partner URL that is sent syncing data (e.g., cookies) when a user hits the page.
In a user-sync hijack, an AdTech platform attempts a partner sync but finds a threat actor in its place (see Figure 2). In other scenarios, domains that were previously managed by the defunct AdTech partner had expired, and had been taken over by scammers that used an innocuous connection to deliver malicious code.
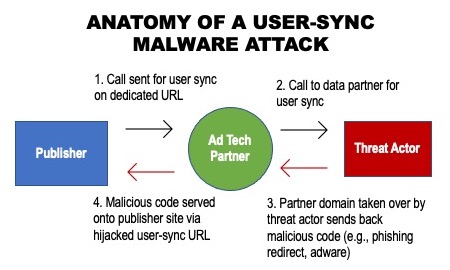
This method of malicious code delivery makes it more difficult to immediately identify the source of the malware. Creative blocking is limited by each blocker’s methodology—if the blocker is integrated into the ad server or around the publisher ad tag, it won’t be able to stop a bombardment coming through an ID sync. A vendor that blocks based on buyer IDs would never see this attack coming because there is no buyer.
Vulnerabilities aplenty
ID syncs are a critical element in the programmatic marketplace; however, the channel is vulnerable to hijacking, and this kind of malware attacks everyone in the affected digital supply chain.
Malware delivered through a hijacked user sync is not a new attack vector. In late October, more than a thousand malicious code deliveries were hijacked ID syncs from a domain associated with ChoiceStream—a DSP that ceased operations in 2017. In January, more than 5,000 malware events served via a compromised user sync from a domain associated with the firm Telemetry—a now-defunct digital campaign measurement company focused on fraud prevention.
The proximity of these three attacks is worrisome, especially considering the surgical nature of the Electrum campaign—a massive assault delivered in a matter of hours. Expired domains from defunct, rebranded, or acquired AdTech companies can be bought in certain marketplaces for a limited amount of time—enough to execute a malware barrage and then move on to the next target.
Recommendations
- Ad Tech:
- Check all user syncs to make sure domains are up to date.
- Remove any calls to defunct partners or ones you no longer have active relationships with.
- Publishers:
- Check your pages and headers and remove code from expired partnerships or defunct partners.
- Employ continuous tag scanning and page scanning—not just of your own site but also ad landing pages.

