This article was authored by Pat Ciavolella, Director of Digital Security & Operations at The Media Trust.
Gathering information and making the right choice has never been easier, thanks in large part to a host of applications that put information at the fingertips of smartphone users. In March, a compromised iPhone app, which had been downloaded by millions of users around the world, did more than deliver information to its users; it infected their devices with persistent malware that hid within an ad’s style sheets and called to 22 known malicious domains in order to deliver a variety of payloads.
Anatomy of a scam
The malicious code, referred to by The Media Trust’s Digital Security & Operations team as FourthColor-3PC, made its way to the app through a small Demand Side Platform (DSP) with a poor reputation for vetting ads. Such DSPs are frequent targets of bad actors who want a convenient entry point into the digital ad supply chain and, ultimately to millions of app users. As soon as the user opened the app, a malicious code serving as a prime mover would activate and call to several malicious domains even as the app was loading. (See Figure 1.)
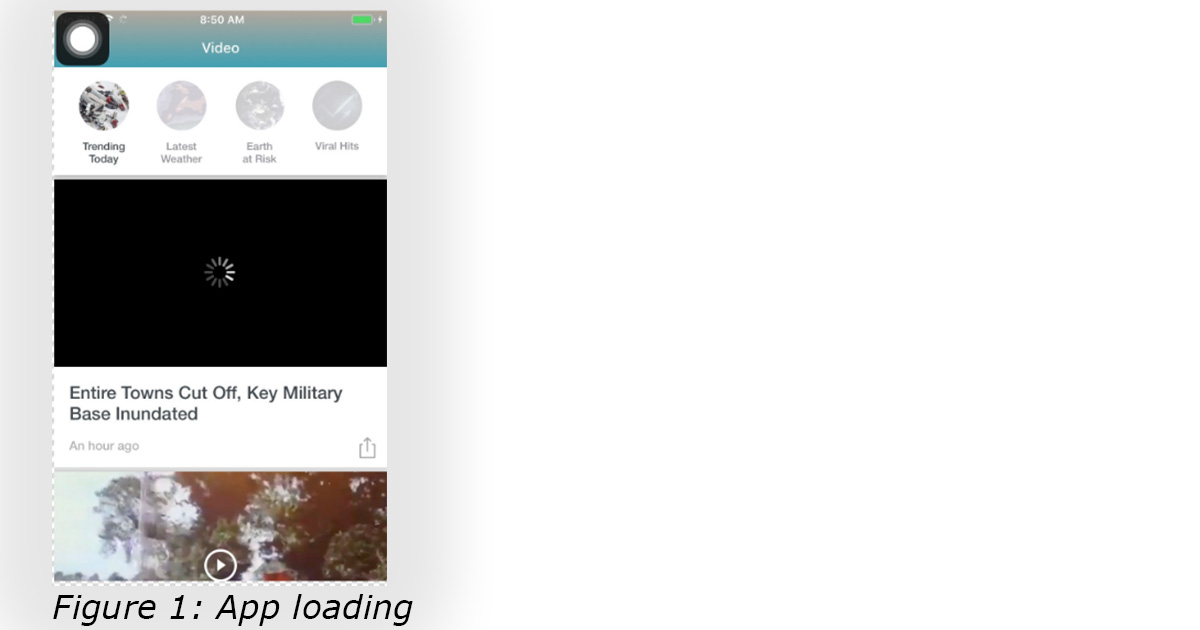
Without any user interaction, the code would redirect the user out of the application itself, and into a malicious site or through a series of auto‐redirectors until the user landed on a fake reward popup or survey. Users unable to close the malicious content would unknowingly receive the payload.
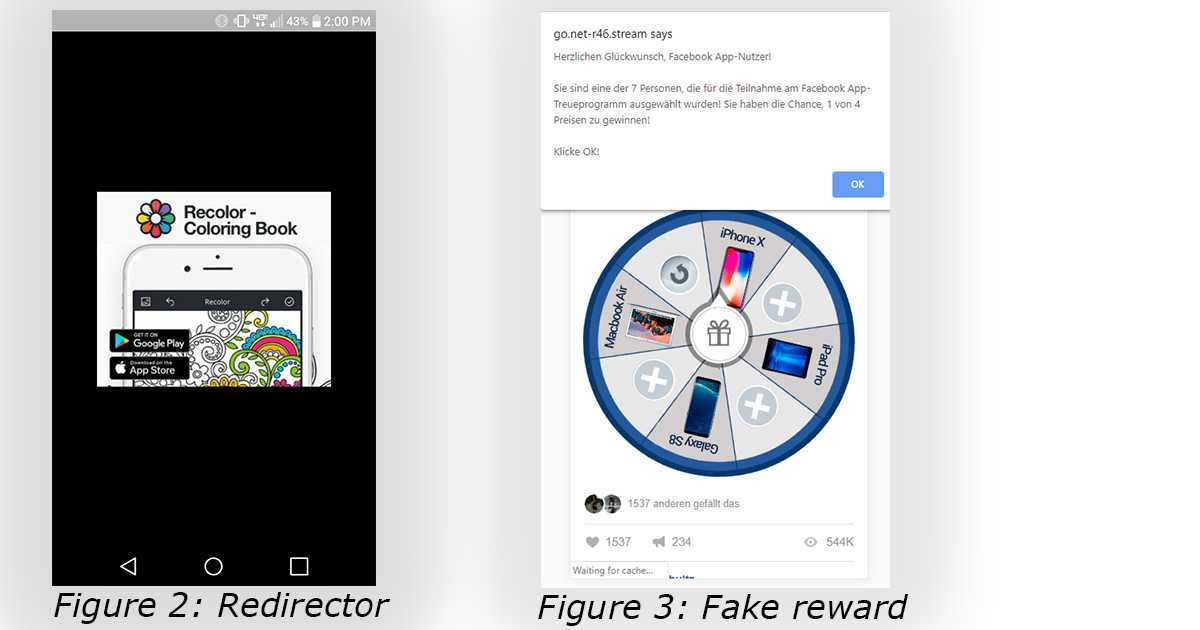
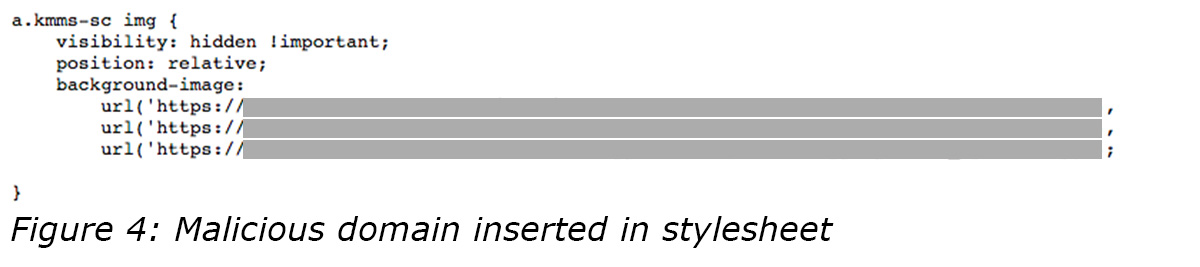
The Media Trust had seen and block-listed most of the malicious domains, a few of which had been sighted in earlier campaigns that targeted desktops. One redirector featured a malicious ad for a coloring book. (See Figure 2.) One landing page offered the user the chance to win one of a selection of Apple devices. (See Figure 3.) The objective of the code was to deliver a new or different payload each time. The malicious code was embedded in the style sheets and loaded in the background to elude users and anti-malware. (See Figure 4.)
The malicious campaign’s orchestration of more than 20 malicious domains, the challenge or impossibility of closing malicious content, and the use of stylesheets to sneak in the malware, all reflect the continuing innovation of cybercriminals. The use of malicious domains across platforms shows bad actors are upgrading their campaigns to target popular apps.
The app publisher’s risks were not limited to security. The Media Trust discovered 34 other domains and more than 30 cookies that operated outside the app publisher’s infrastructure. If these domains and cookies collect and distribute user information without the latter’s consent, a publisher could be liable to a heavy penalty under GDPR, the California Consumer Privacy Act, or a growing number of privacy laws.
Most publishers have little to no visibility of the third-party code that enable their apps to function. The code is even harder to monitor and manage when it’s linked to in‐app advertising. These vulnerabilities, born out of the digital environment’s dynamism and lack of transparency, are what make malvertising campaigns lucrative investments.
To catch a cyber thief
The Media Trust’s continuous improvements on application scanning has enabled the team to find unusual activities across entire apps launched within a variety of devices. When the DSO checked the array of suspicious domains against primary source attack data, they discovered that the majority of the malicious domains had been flagged and block-listed in previous years. The few malicious domains that had not been seen before were identified by the DSO while reviewing app scans for any unsanctioned domains. In this case, the team discovered the domain lurking in the background within the stylesheets.
As cybercrooks turn their sights on apps, publishers should ensure they keep close tabs on what happens to users from the second the app launches until well after it closes. It’s the best way to protect app users, including those whose devices previously considered invulnerable to hackers.

