Compromised landing page allows unauthorized collection of credit card information.
A holiday weekend will prove more memorial for some visitors to several ecommerce sites. Customers wishing to purchase athletic gear or sign up for a competition risked having their credit card information collected by an unauthorized third party.
Detecting the infection
In the United States, Memorial Day signals the start of summer and the three-day holiday weekend kicks off with numerous large-scale promotions and sales campaigns pitching outdoor-related goods and services. Consequently, the digital advertising ecosystem usually experiences a jump in campaigns to drive traffic to ecommerce sites—a ripe opportunity to leverage.
The Media Trust team detected extraneous JavaScript code executing on the payment landing page for several medium-sized, sports-oriented ecommerce websites.
First detected in the early afternoon of Saturday, May 28, legitimate advertising creative directed users to legitimate ecommerce sites which happened to be compromised. The “angular” domain (angular.club) injected superfluous JavaScript throughout the sites to collect information input by a user, such as race registration or financial details associated with a purchase.

Diagnosing the financial headache
The angular domain injected UTF-8 encoded script throughout the entire ecommerce site and obfuscated itself by adopting the name of the site into its script, i.e., angular.club/js/site-name.js. Searching on the root domain “angular.club” redirects to “AngularJS.org”, a valid Google JavaScript framework and another attempt at misdirection to hide the true intention.
It’s likely the bad actor penetrated the content management system (CMS) or website theme template in order to ensure the code executed on all pages, especially the payment landing page.
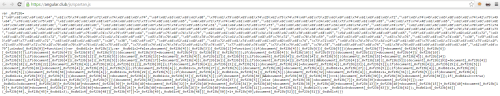
Example of JavaScript
This code collects a range of financial and personally identifiable information (PII) including billing name, address, email, telephone number, credit card number, expiration date, and CVV.
The information is then sent to another server unassociated with the ecommerce site owner. The host of the angular domain and the web service that collects the credit card information are owned by the same entity, whose host server is in Germany and registered to someone in Florida.
Per The Media Trust team, there is no valid coding reason for this JavaScript to be on the website. The script’s sole purpose is to inject a block of code into the web page to collect credit card information and send it to another server where it can be used for future use—purchase online goods, sold on the dark web, used to buy domains to launch additional attacks, etc.
Assessing the health of the ecommerce site
The ecommerce site operators removed the code from there sites late on Tuesday, May 31. Frankly, the damage was already done.
During a strong promotional period, several small- to medium- sized ecommerce sites did not realize their expected traffic. Due to the malicious nature of the landing page associated with these campaigns, The Media Trust alerted our ad tech clients to block the serving of the ads. In one instance, seven different creative supporting more than 200 ad impressions did not execute. In addition, one of the campaigns promoted an event with an expiration date of Wednesday, June 1.
Prescribing the cure
The Internet can be a scary place, full of bad actors looking to make a quick buck by preying on the good nature of others—consumers and website properties alike. Holiday periods are when the online ecosystem experiences a surge in attacks, and no business or organization is immune.
The lesson learned is that brand and corporate websites are just as vulnerable to attack as ad content. And, ecommerce is especially vulnerable due to the direct impact to revenue.
The best defense is to be on constant alert, a security posture that is difficult for most to assume. That’s why many firms leave it up to the experts to continually scan their online and mobile ecosystem. Continuous website monitoring will alert you to an anomalous or unexpected behavior of third-party vendors and first-party, website operator code. Upon detection, these issues can be immediately resolved thereby keeping your ecommerce operation alive and kicking.

