An early summer storm of phishing redirects uses domain-cycling and programmatic complexity to wreak havoc
- Redirects travel through multiple programmatic resellers to hit more than 1,000 publishers
- Malvertiser used dozens of domains to elude ad quality providers and blockers
- Recommendations:
- Continuous client-side scanning leveraging a variety of device and geo profiles to catch hyper-targeted malware
- Precision blocking saves revenue by tracking down end-buyers and keeping paths to legitimate SSPs and DSPs open
As seen in the latest evolution of mobile-targeting malware GhostCat-3PC, rapidly cycling through domains has become a hot malvertising technique to evade detection, bypass creative blocking tools, and prolong an attack. This tactic featured prominently in a May malvertising barrage that swamped more than 1,000 publishers across the US and Europe in redirects. But in addition, the malvertiser took great advantage of programmatic complexity and arbitrage to conceal its origin.
Domains In Every Color
The Not-So-Merry May redirects employed innocuous creatives covering more than 20 subjects to pass initial audits and camouflage malevolent intent. The malvertising further used cloaking to target mobile web environments, where it deployed redirects seeking to phish consumer data.
The barrage gained scale through numerous short-lived campaigns that would end before or soon after they were identified as malicious. But what really aided the attack in achieving scale was constant spinning through domains to elude detection.
This redirect incident used four primary domains inflated by around 10 top-level domains each (e.g, .world, .xyz, .online). As soon as a campaign was recognized as malicious and added to blocklists, the malvertiser would switch domains and ramp up again. The Media Trust’s malware desk identified at least 30 active malicious domains, as well as another 25 dormant ones from the same lineage.
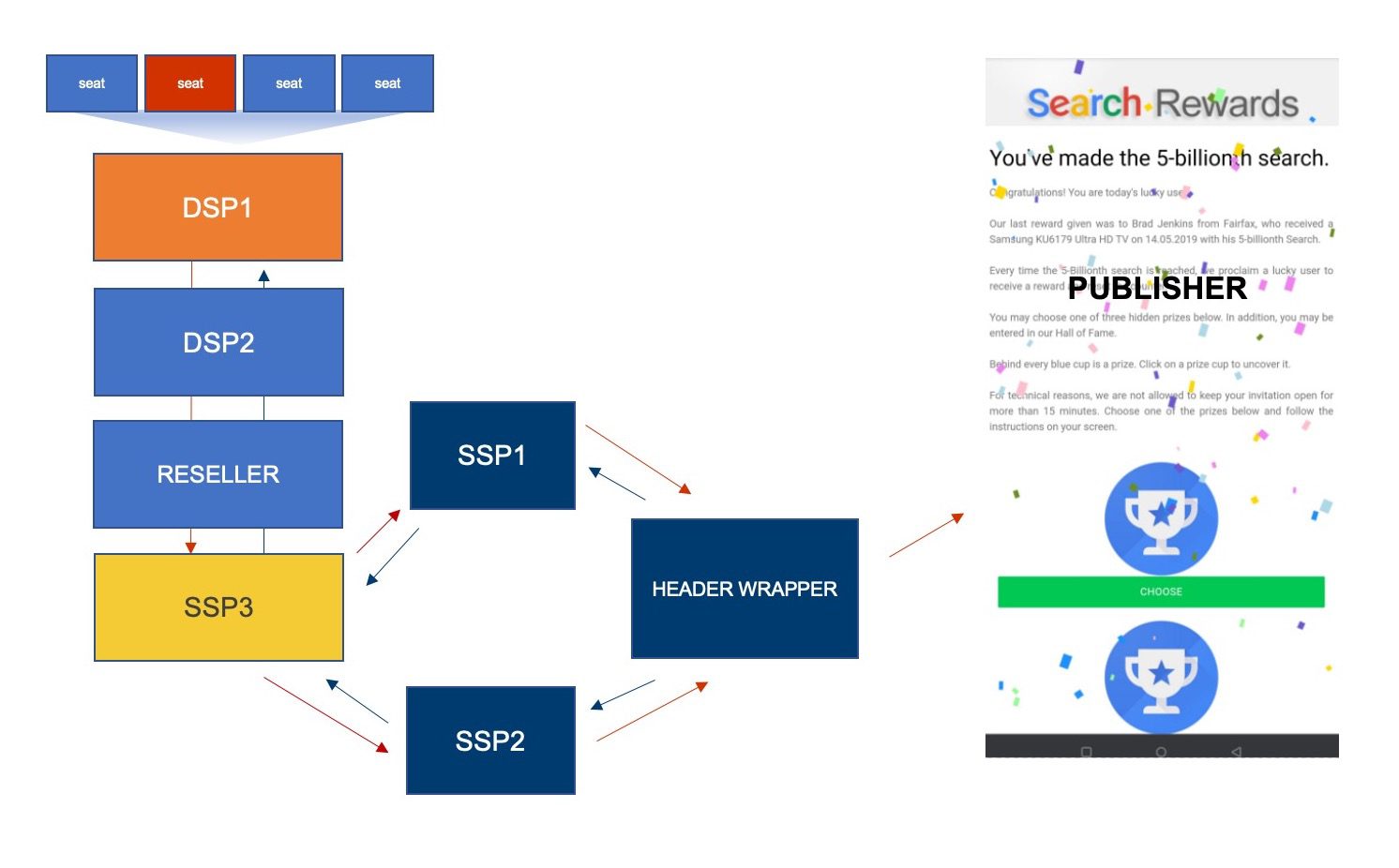
Blunt-Force Revenue Trauma
The redirects took advantage of programmatic complexity, employing at least a few resellers to mask their origin (see Figure 1 above). Because the ultimate source wasn’t easy to suss out, some ad quality providers advised their clients to cut off demand from a legitimate SSP, when the actual malevolent buyer was two to three steps further up the demand chain. This kind of blunt force blocking leaves money on the table and causes strife with beneficial partners who are just as much victims as publishers.
Precision blocking powered by an experienced malware desk can single out the culprit without sacrificing revenue opportunities or damaging relationships with demand partners. You can protect your users from malware and scams without putting a dent in your bottom line.

