Large-scale video malware attack propagates across thousands of sites
Malware purveyors continue to evolve their craft, creatively using video to launch a large-scale malvertising attack late last week. Video has been an uncommon vector for malware, though its use is on the rise. What’s different is the massive reach of this particular attack and the ability to infect all browsers and devices. Much like The Buggles decried about video changing the consumption of music, this intelligent malware attack used video to orchestrate mayhem affecting 3,000 websites—many on the Alexa 100. Is this the future?
Charting the infection
The Media Trust team detected a surge in the appearance of the ad-based attack late Thursday night and immediately alerted our client base to the anomalous behavior of the malware-serving domain (brtmedia.net). As it unfurled, the team tracked the creative approach to obfuscation. (See image)
First, the domain leveraged the advertising ecosystem to drop a video player-imitating swf file on thousands of websites. The file identified the website domain—to purposefully avoid detection by many large industry players—and then injected malicious javascript into the website’s page. Imitating a bidding script, the “bidder.brtmedia” javascript determined the video tag placement size (i.e., 300×250) and called a legitimate VAST file. As the video played, the browser was injected with a 1×1 tracking iframe which triggered a “fake update” or “Tripbox” popup which deceptively notified the user to update an installed program. (In the example below, the user is instructed to update their Apple Safari browser). Unsuspecting users who clicked on the fake update unwittingly downloaded unwanted malware to their device.
The compromise continued unabated for hours, with The Media Trust alerting clients to attempts to infect their websites. This issue was resolved when brtmedia finally ceased delivery, but only after tainting the digital experience for thousands of consumers.
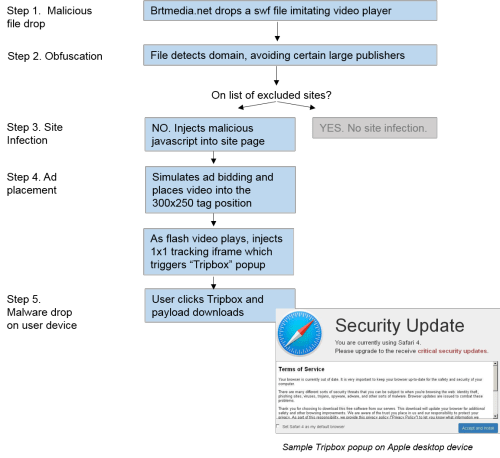
Process flow for video-borne malware infection
The devil in the artistic details
The use of video as a malware vector is increasing. As demonstrated above, video and other rich media provide avenues for compromising the digital ecosystem, impacting both ads and websites.
The clever design and inclusion of multiple obfuscation attempts allowed this attack to propagate across some of the largest, most heavily-trafficked sites. As The Media Trust clients realized, the best defense against this kind of attack is through continuous monitoring of all ad tags and websites, including mobile and video advertising.

