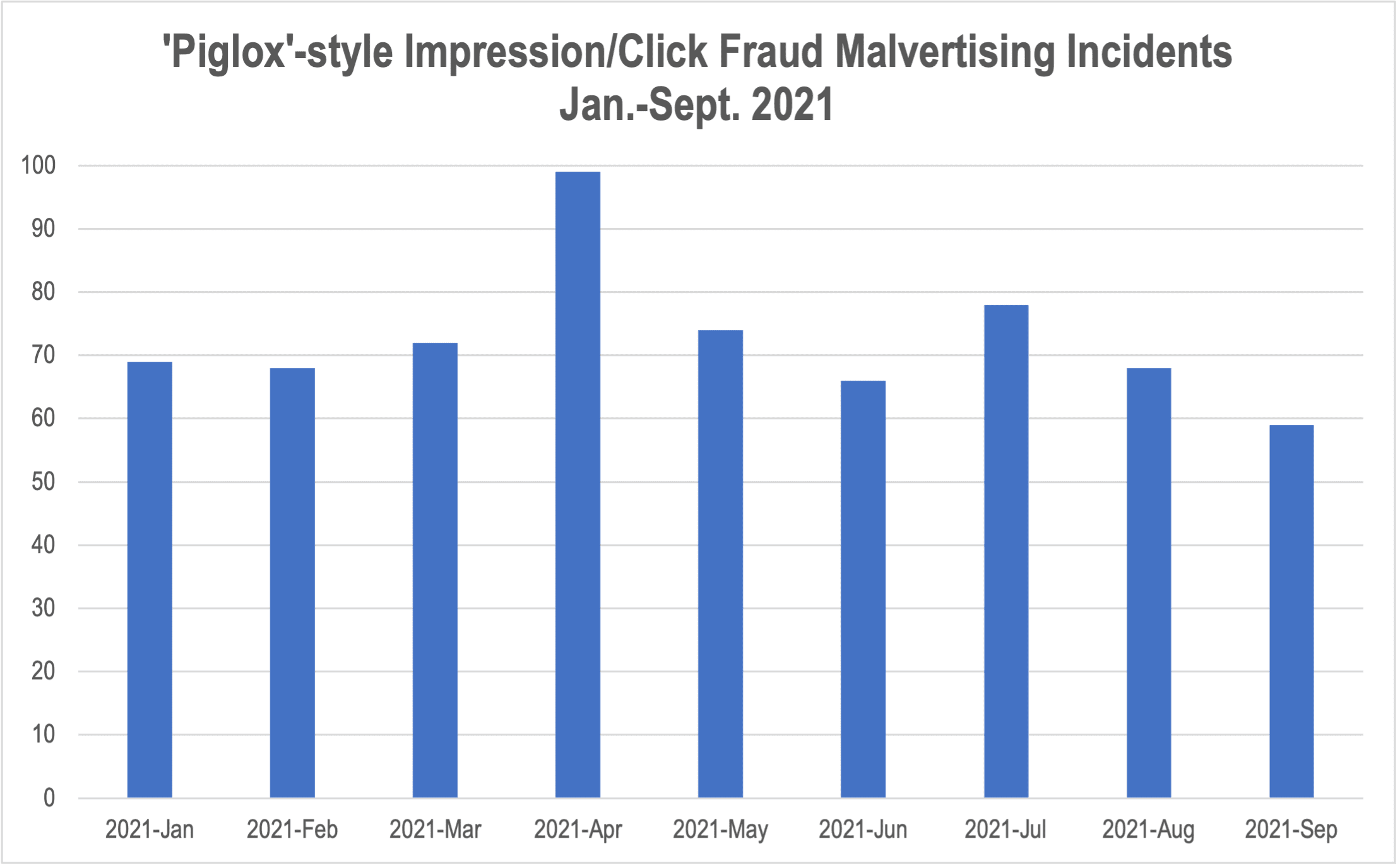
- 110% rise in “piglox”-style click/impression fraud incidents since Sept. 2020
- Excess code within ad executes false impression or click fraud URLs for unrelated campaigns
- Multi-billion dollar in-app video marketplace highly vulnerable
Recommendations
- Leverage blocklists covering known purveyors of piglox-style impression/click-fraud campaigns
- Employ tag-scanning from a variety of device profiles to unlock hidden fraudulent impression and click URL code.
We view malvertising and ad fraud as flip sides of the same coin. Ad fraud uses a variety of means—including bot networks and human-powered click farms—to bilk advertisers by inflating impressions, video views, or clicks. The countless forms of malvertising roaming the digital advertising pipes, on the other hand, aim to exploit consumers—and often fleece them out of money or personal information.
But as bot and invalid traffic detection has greatly improved, it seems ad fraudsters are stealing tactics from their malvertising peers. The Media Trust has detected a 110% increase from September 2020 in so-called “piglox” campaigns that inject excess code into an ad that is unrelated to the functioning of that unit. This code is then used to generate fraudulent impressions or click URLs typically for unrelated campaigns.
Secondary Shenanigans
Piglox campaigns make up 95% of all the impression/click fraud campaigns The Media Trust identifies. As evidenced by the high-profile Vidlox incident—which pumped up major spikes in click/impression fraud in April, June, and July–the $18 billion in-app video advertising market appears to be a prime target. According to DoubleVerify, 2% of all in-app video impressions are fraudulent, an amount that has jumped 50% in the past year.
Like in the Vidlox case (See Figure 2.), piglox-style creative is normally innocuous and unlikely to raise eyebrows. In the first stage of a piglox-style ad fraud execution, the fraudulent URLs usually appear, but the secondary content (including pixels for reporting) will not discharge until the ad code determines it is in the target environment. In Vidlox, this was major mobile apps like Trivia Crack, CBS Sports, and Pin Rescue—the impressions/clicks reported have an aura of authenticity that can deceive the advertisers. The obscured secondary code can be difficult to detect if an ad quality provider isn’t scanning from a variety of device profiles.
Say No to Fraud
It’s an ugly adage that ad fraud is baked into digital advertising pricing. All legit players in the space have a duty to stamp out ad fraud, and hey, it should be to their advantage to free the ad ecosystem of click and impression scammers. Easier said than done, of course.
Publishers and AdTech platforms might be getting a cut of the action from ad fraud delivered via malvertising, but by helping defraud advertisers, you’re potentially taking bigger amounts of cash out of your own pocket. That’s campaign spend that could have been going directly to you, and if the advertiser is fooled by fraudulent results, chances are the bad actor will see even more campaigns in the future. You’re cheating yourself by being a cog in the ad fraud machine.
For AdTech platforms, mitigating impression- and click-fraud campaigns leveraging malvertising techniques firstly requires blocklists that single out known ad-fraudsters. In addition, these platforms need to employ scanning through a variety of device profiles to reveal hidden impressions or click URLs waiting for a target environment. But it’s all for naught unless publishers make sure their malware blockers include impression-/click-fraud campaigns in their blocklists.

