Phonyfetcher-3PC reveals Chrome extension adware is malware targeting elderly consumers
Don’t you hate it when you don’t have the right software when you need it? Like when you need to compile a bunch of scanned documents into a single PDF, yet none of your applications support that.
No worries, you think—you’ll just go online and search for a free tool. Regrettably, that thinking causes more harm than good. Whether you find it through a digital advertisement or online search, many free utilities are browser extensions that install backdoors to consumer devices setting up consumers for future compromises—ransomware, keystroke logging, phishing, and more.
Adware? More like malware
Free online utilities are frequently labeled as potentially unwanted programs (PUPs) by most antivirus and security vendors because they may contain code consumers don’t expect. When associated with a digital advertisement, it may be labeled as adware due to its involvement in the display or download of advertising-related materials. The deceptive tactic of loading additional code beyond what’s expected by the average user is a red flag.
Relying on a “downloader beware” mentality, these security vendors don’t account for the true risk to consumers. Unfortunately, consumers download these browser extensions at an alarming frequency and roughly 70% are malicious.
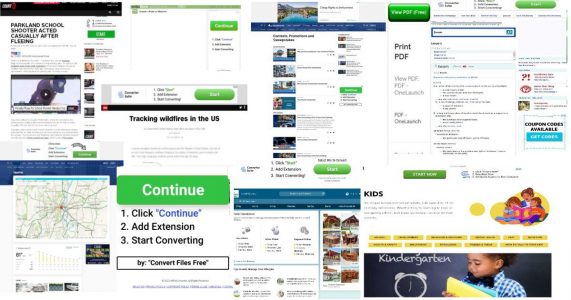
One such productivity utility set off alarms at The Media Trust: document converters. While not new, the 9X increase of these ad-driven Chrome extensions over the past few months spurred a deeper investigation [Figure 1].
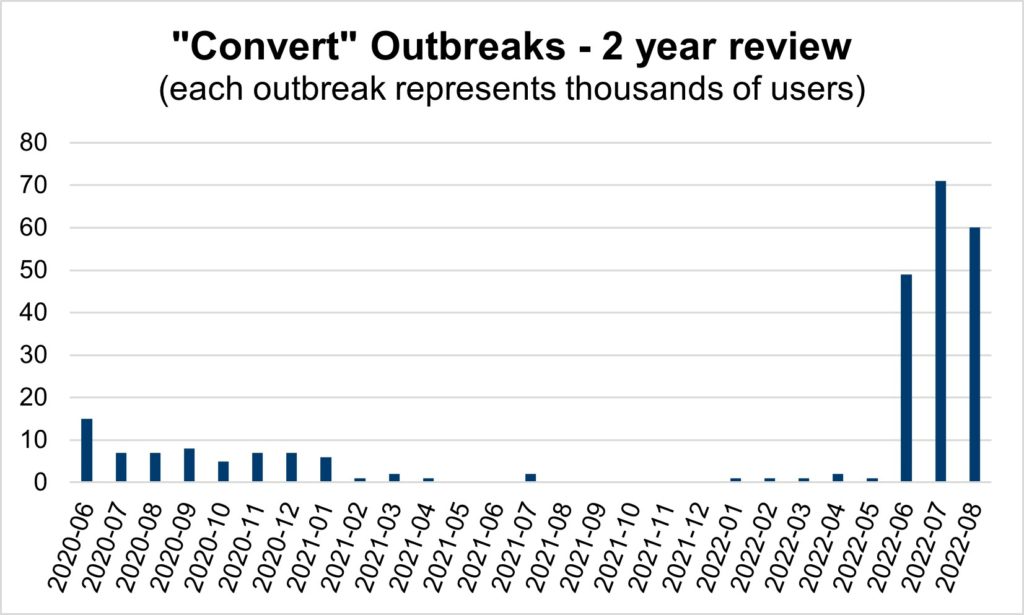
By consumer age group, the data reflects a 3X increase in targeting of elderly consumers while decreasing for teenagers. [Figure 2] These converter incidents are trending higher than the2X increase targeting the elderly across all malware types. It’s likely bad-faith actors believe elderly consumers are more susceptible to downloading the malware-laced extensions.
Phonyfetcher-3PC: adware goes from bad to worse
A review of the domains driving this volume yields more than 10 URLs, each containing the term “convert” and a reference to documents (e.g., files, PDF, suite, etc.). The landing page websites are all clones; they promote Chrome plugins, have 1-year lifespans, and have received plentiful bad reviews and complaints about serving popups. Further inspection confirms the domains all claim the same physical address in Hong Kong, which is likely an offshore registrar to protect a known Beijing-based code farm.
These types of incidents—with similar structure, threat behavior, and source—are now tied together and labeled Phonyfetcher-3PC
The domains were created and/or updated within the past few months. Upon entering the digital advertising ecosystem, these domains were evaluated, confirmed to be installing Backdoors on consumer devices, and added to our blocklist. However, antivirus platforms (e.g., VirusTotal) do not flag any of these domains, and therefore are misleading consumers into believing they are protected from these unwanted attacks.
The malicious domain lifecycle is interesting as well. A sampling of domains with the most activity in 2022 shows that the older domains are likely probing for vulnerabilities in the digital advertising ecosystem. This activity helps bad-faith actors learn what to exploit and paves the way for larger scale attacks—such as the ones starting in June. [Figure 3]
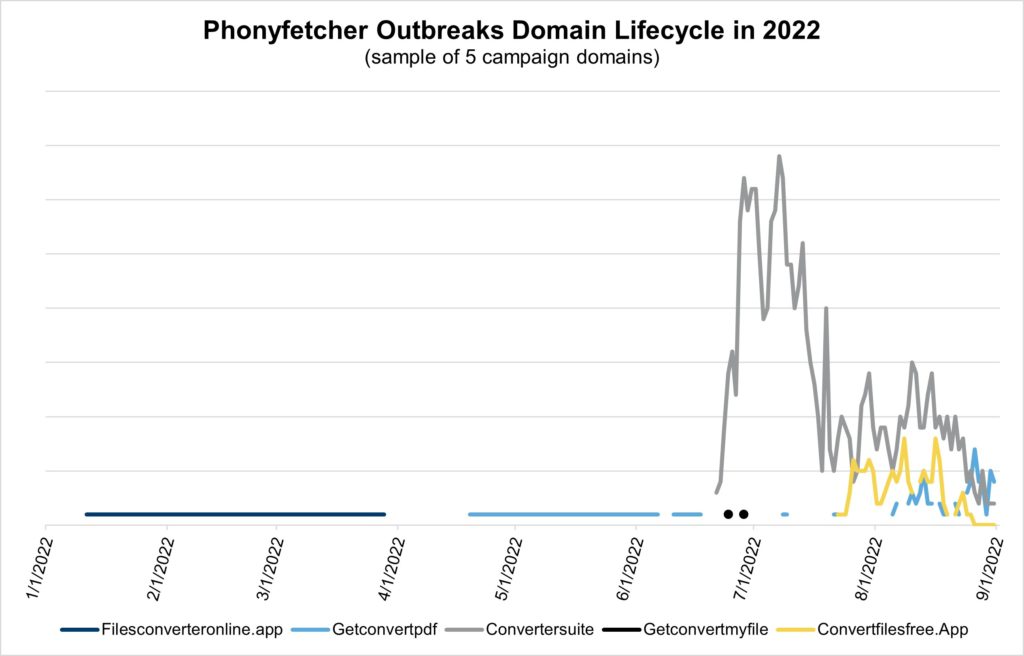
These campaigns thread the needle between PUP and malware. A successful tactic, bad actors are increasing their use of these malware-laden tools. As a result, these malicious domains bypass creative blocking tools, riddling dozens of publishers with unsuspecting malware since June.
Adware risk isn’t worth the reward
In the eternal risk versus reward battle, adware can really complicate things for revenue professionals. The revenue from these Chrome-extension ads can be incremental as long as consumers don’t complain. However, in some instances like the “convert” outbreaks, the risk of malware and overt harm to consumers cannot be ignored. Even worse, no one wants to be accused of helping bad-faith actors target the elderly with malware.
Lucky for you, The Media Trust investigated these outbreaks, added them to our blocklists, and worked with our partners to minimize the impact of these risky ads. Determine your approach to adware, so the next time a consumer looks for these tools it won’t be associated with your business. That’s a process we can all get behind.