In late September, The Media Trust Digital Security & Operations team began tracking a malicious campaign targeting mobile devices. The tag-delivered malware enables ad fraud by generating 150+ hidden iframes to serve unviewable impressions and execute non-human clicks. Not only are these ads not viewable by humans, but the device owner experiences unacceptable latency due to the extensive iframe and impression volume.
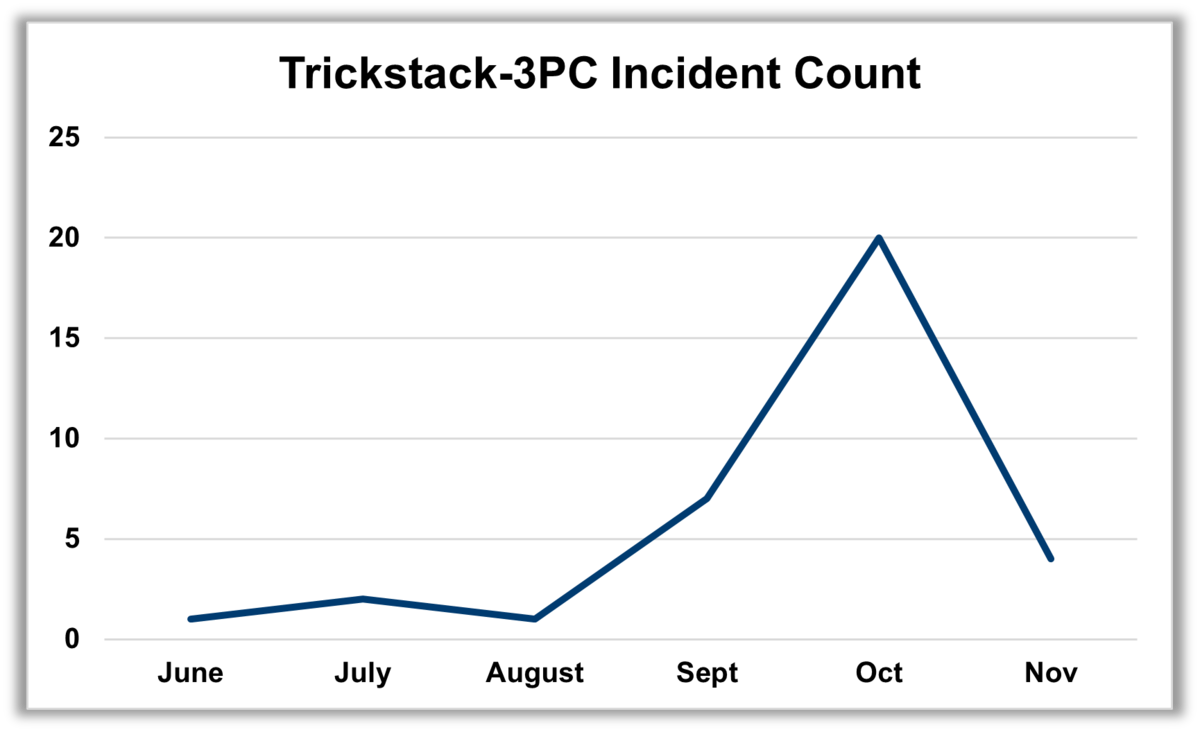
Quickly tripling in scale in 14 days, a third-party actor employed extensive code obfuscation, and spread ad buys across dozens of small-scale DSPs to bypass malware blockers and evade detection. [Figure 1] Because these nonviewable impressions drive ad fraud—a multibillion dollar problem for all players in the digital advertising industry—our DSO worked directly with Google, Trustworthy Accountability Group (TAG) Threat Exchange, and affected AdTech partners to address the escalating outbreak. This industry cooperation is crucial; as of late November, the attack has slowed down significantly.
When a test probe becomes a threat
The DSO first detected the primary malicious domains in early June affecting a broad range of AdTech providers around the world. For a period of 6 weeks, a few small campaigns were launched containing compromised ad tags that simply redirected to malicious content.
In late September, the attack morphed and became more sophisticated. When the correct conditions are met, a creative is delivered and an auto-redirect triggers the fraud. This fraudulent content is housed inside the URLs responsible for delivering the creative. The campaign is affecting primarily small DSPs—many with self-serve platforms—and campaigns in the United States, Japan and South Korea. While limited to mobile devices, the campaign targets iPhone and Android devices which comprise more than 95% of the world’s estimated 3.5 billion mobile users.
Trickstack-3PC: How it works
This two-stage malicious campaign is delivered via compromised tags attached to campaign creative. [Figure 2] These tags have a JavaScript extension “js”, which executes additional functions before allowing the creative to be delivered.
- Stage 1: Conducts preliminary checks to verify a real user
- https://tpc.googlesyndication.com/pimgad/[string of numbers]/[file name].js OR
- https://captive.tpc.googlesyndication.com/pimgad/[string of numbers]/[string of numbers].j
- Stage 2: Executes Ad Fraud by creating and clicking on ad impressions
In Stage 1, the ad tag code is heavily obfuscated, a fairly common technique used to legitimately minimize code. However, in this instance, the obfuscation is more than 1,000 lines of code and requires use of a debugging tool (and patience). The code verifies the device is a phone and using https, and then creates a new script:
https[:]//ce.googher.xyz/js/tmp/dyp.min.js
In Stage 2, the script creates a JavaScript object with various key value pairs (12 confirmed to date) associated with campaign information and device type (Android, iOS). The script can call 12 different functions. Most importantly, these value pairs:
- constructURL creates an impression URL by device which generate hidden iframes to serve ads:
- Android: api.jumpraw[.]com; 161+ iframes
- iOS: api.yausiu[.]com; 151+ iframes
- AddClickTrack initiates the non-human clicks on the ads served via the iframes

Creative used in Trickstack-3PC campaigns
The creative associated with the campaign runs the gamut from name brand consumer products to innocuous promotions. While we do not believe these are legitimate campaigns, it appears the bad actor is hijacking existing creative, appending the malicious ad tags, and then placing dozens of campaigns via small DSPs. [Figure 3]

Tackling Trickstack-3PC
Once again, the rapidly changing nature of this attack allowed it to bypass user-facing malware blockers. Continuous, real-time scanning via rotating profiles uncovered the evasion techniques allowing the DSO to analyze the attack structure and feed the malicious vectors into Media Filter, our real-time malware blocker.
Tactics to mitigate your digital supply chain’s exposure to this type of ad fraud include:
- Real-time scanning to detect changing attack vector, especially
- Buyer relationship analysis to closely monitor and throttle campaigns from new buyers or those without an established reputation
- Blocking appliance needs to use real-time data to maintain efficiency
- TAG certification programs for both Malware and Fraud. TAG certified channels experience 90% less fraud