Targeted digital content and advertising on websites and apps confirmed at least 2 months before physical invasion.
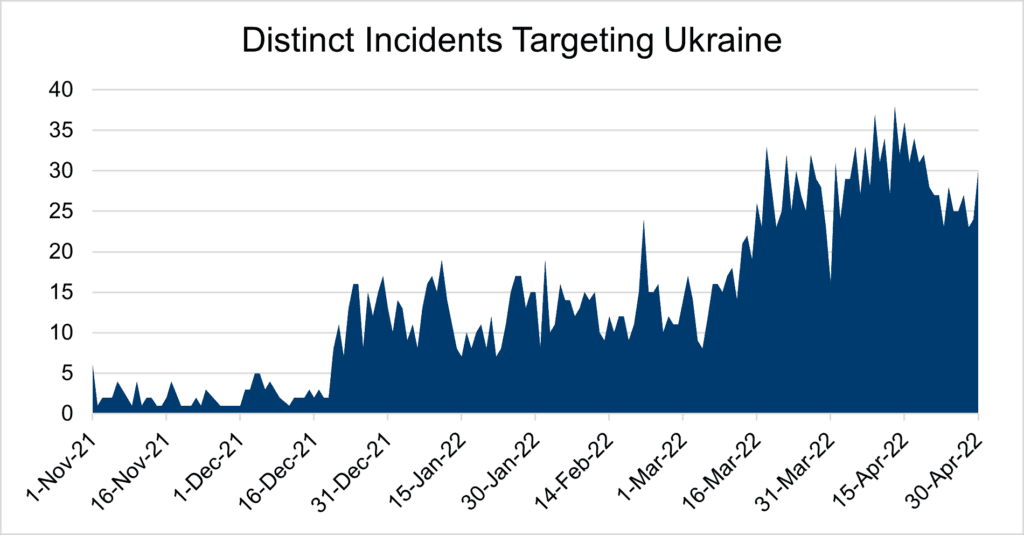
The writing was on the wall in the lead up to the military invasion of Ukraine. Typically experiencing a handful of consumer-directed attacks each month, the country endured a 2X malware surge towards the end of December. The cyber assault continued past the February 24 invasion reaching 5X through April. [Figure 1]
Nothing like a large-scale crisis to bring out bad actors. The emergence of fraudulent donation schemes and cryptocurrency scams are expected. While there are several stories about Ukraine—from military response and government outreach to international solidarity—few examine the effect of digital attacks targeting consumers.
Ukraine consumers remain under attack
Concerns of propaganda and disinformation propagation are natural elements of cyber warfare. Attacks on infrastructure targets are to be expected. What is often overlooked is the role consumers play: their devices are targeted with investigative malware that roots around for valuable information—credentials, system access, contacts, and more—that is then leveraged in future attacks. This is exactly what’s happening in Ukraine.
The malware targeting Ukraine devices is telling. Attack analysis reveals that the malware is discovering consumers, either directly via credential collection or indirectly via device detail capture. A breakdown of attacks by type from January through April unveils [Figure 2]:
- Scams, 54%. Credential collection. This attack is a phishing/credential theft scam enticing users to enter personal information that is then used to harm the consumer/corporate entity the consumer works for in future attacks.
- Phishing/malicious: 28%. This attack auto-redirects to popups and browser hijacks in the form of fake surveys and also redirects to other malicious content. This invasive content forces the user to a new page and produces content that cannot easily be closed, if at all. These fake surveys are a scamming method used to entice people into clicking a fraudulent link and providing sensitive information.
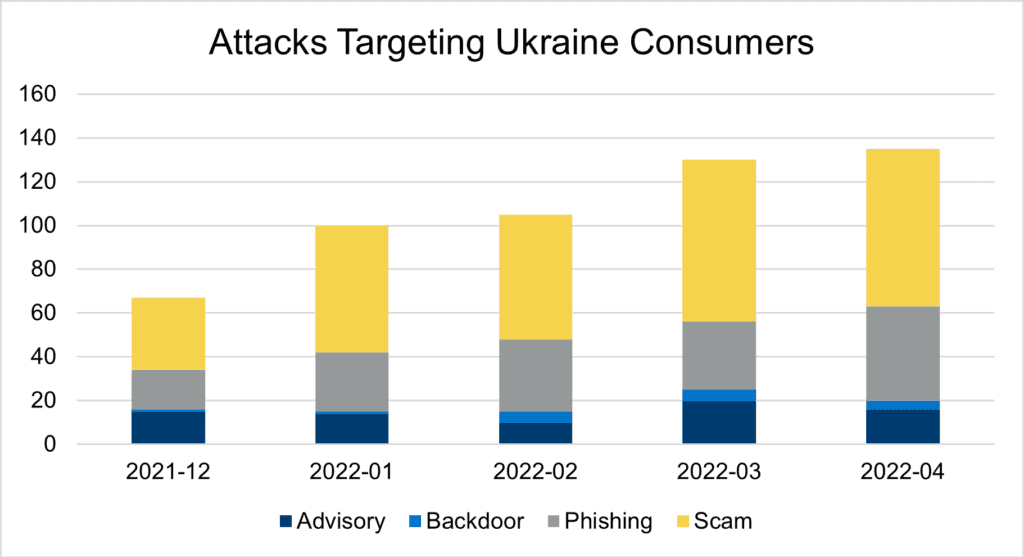
While the remaining attacks contain content that matches previous patterns of known malicious attacks and/or actors, the malware is not overt and, therefore, we advise on its questionable intentions. This advisory is proving prescient as backdoors are emerging.
One significant malware attack is GhostCat. These attacks leverage compromised third-party content (advertising, in this instance) to hijack the browser and redirect to another site, usually malicious. These attacks are successful as not only do they evade ad blocker plug-ins but also creative blockers used by ad-supported sites, e.g., news and media publishers.
Today’s annoyance is tomorrow’s nightmare
This malware directly impacts the digital and personal safety of those in Ukraine. The problem is that they don’t realize when they are being attacked. While cryptomining and resource-intensive incidents drain battery life and slow performance, most malware scenarios are not obvious to the consumer. As a result, their devices—personal and professional–become known for future targeting.
Most concern is directed toward minimizing the spread of misinformation. Little thought has been given to the fact that users in military, government and infrastructure industries are consumers, too. Their personal devices are just as susceptible to malware. Once exposed to malware, these consumers are a path to further, more widespread attacks.
The national security implications of unabated malware delivery are scary. That’s why website/mobile app owners need to know all code executing on consumer devices and removing all unauthorized code. It’s not as difficult as it seems—it just takes a little patience to map your digital attack surface and act on the anomalies.

