Cybercrime has never been more rampant. Too many of us have had family members or friends fall victim to phishing scams or device infections viruses—or maybe you yourself have been burned by online malevolence. Threat actors are using audience profiling techniques including geolocation to prey on senior citizens, minors, and other vulnerable members of society.
As a populace, we feel the effects of cyber attacks when ransomware hits infrastructure like energy and healthcare companies. And rogue states are increasingly using malware and malvertising on everyday citizens as the shadowy world of cyberwarfare evolves.
Digital crime is a plague not only affecting consumers, but also every legit business with an online presence. Cybersecurity Ventures estimates that cybercrime cost the world $7.5 billion in 2024, a figure that will increase by 15% to $10.5 billion in 2025.
Threat actors are leveraging the websites and apps of major media publishers, retailers, e-commerce operations, and even household brands to distribute their attacks to the masses. They exploit the back-end of the Internet by hiding their malignant payloads in cloud storage, hijacking ad code and creatives from everyday advertisers, and compromising domains used for analytics, ad campaign measurement, purchases, and more. All of these treacherous activities cost companies serious revenue, are poison for bottom lines — and often draw unwanted attention from regulators.

Auto-redirects to popups and browser hijacks using fake surveys and/or other malicious content to solicit sensitive data from consumers.
EXAMPLES:
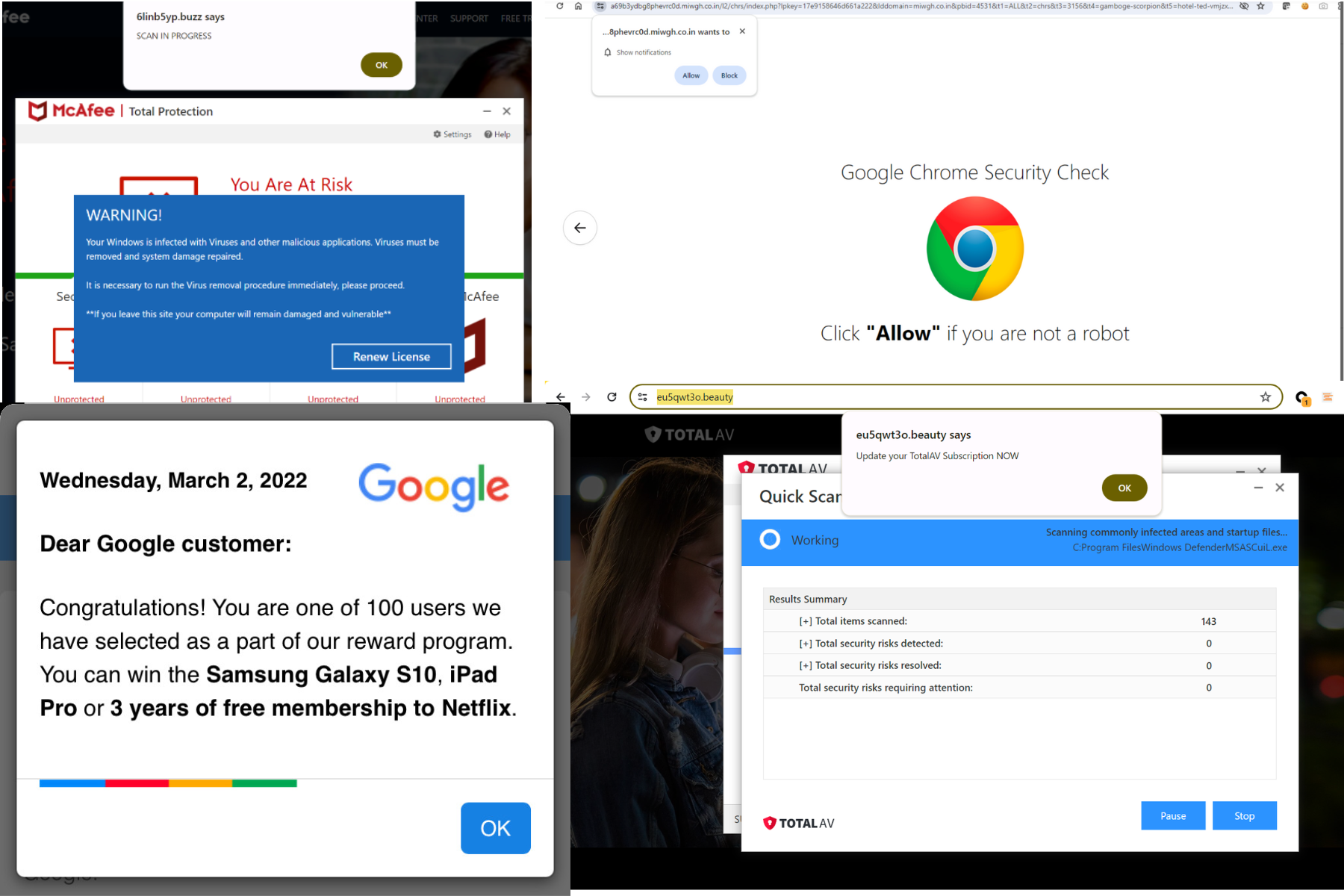
Attacks that deliver a wide variety of malicious payloads to consumers with or without interaction; leave consumer devices vulnerable to future attacks. Often found on compromised advertiser landing pages.
EXAMPLES:
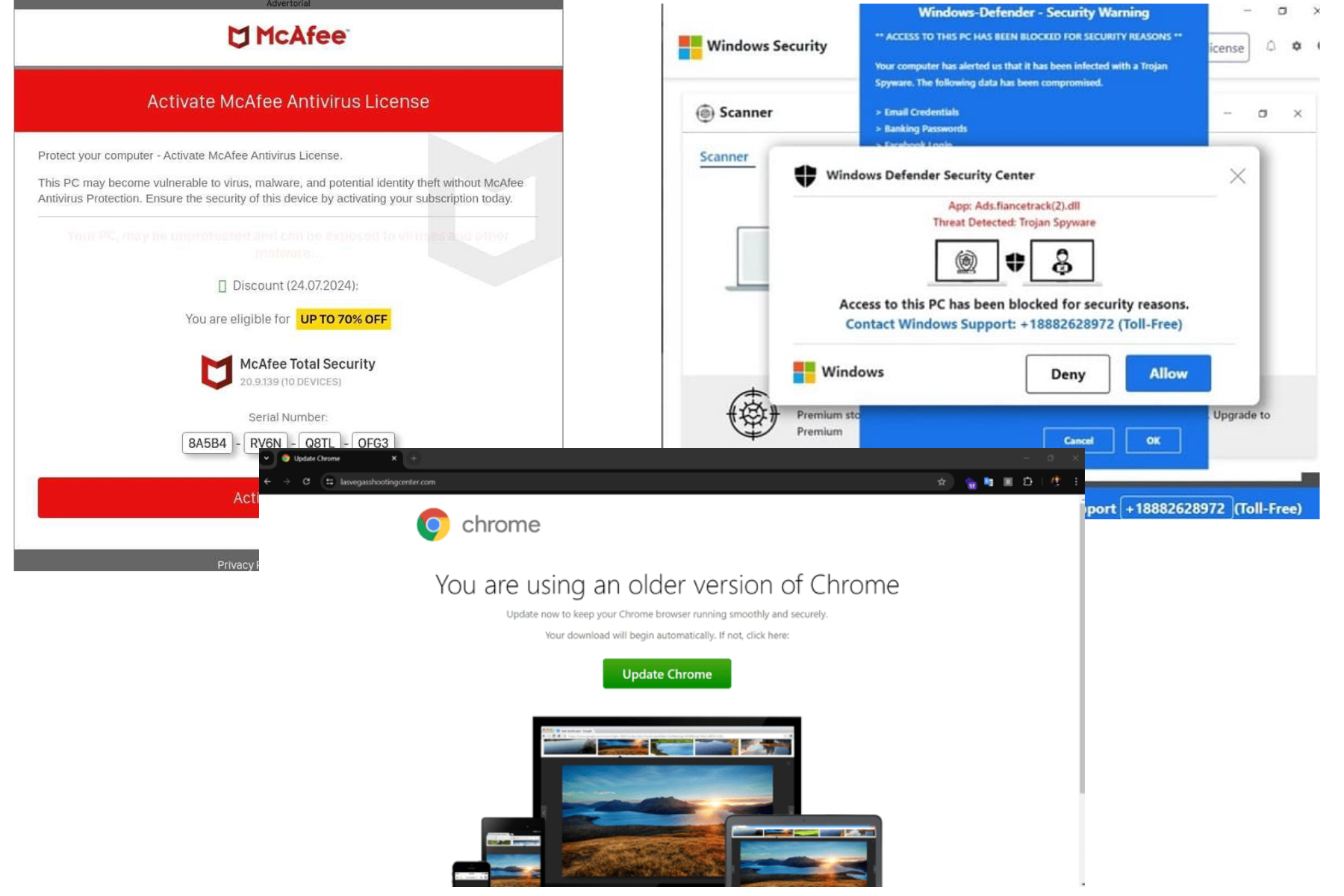
Schemes to defraud consumers or mislead them into sharing personal data that can be leveraged in future attacks. Often hijack celebrity images for fake endorsements.
EXAMPLES:
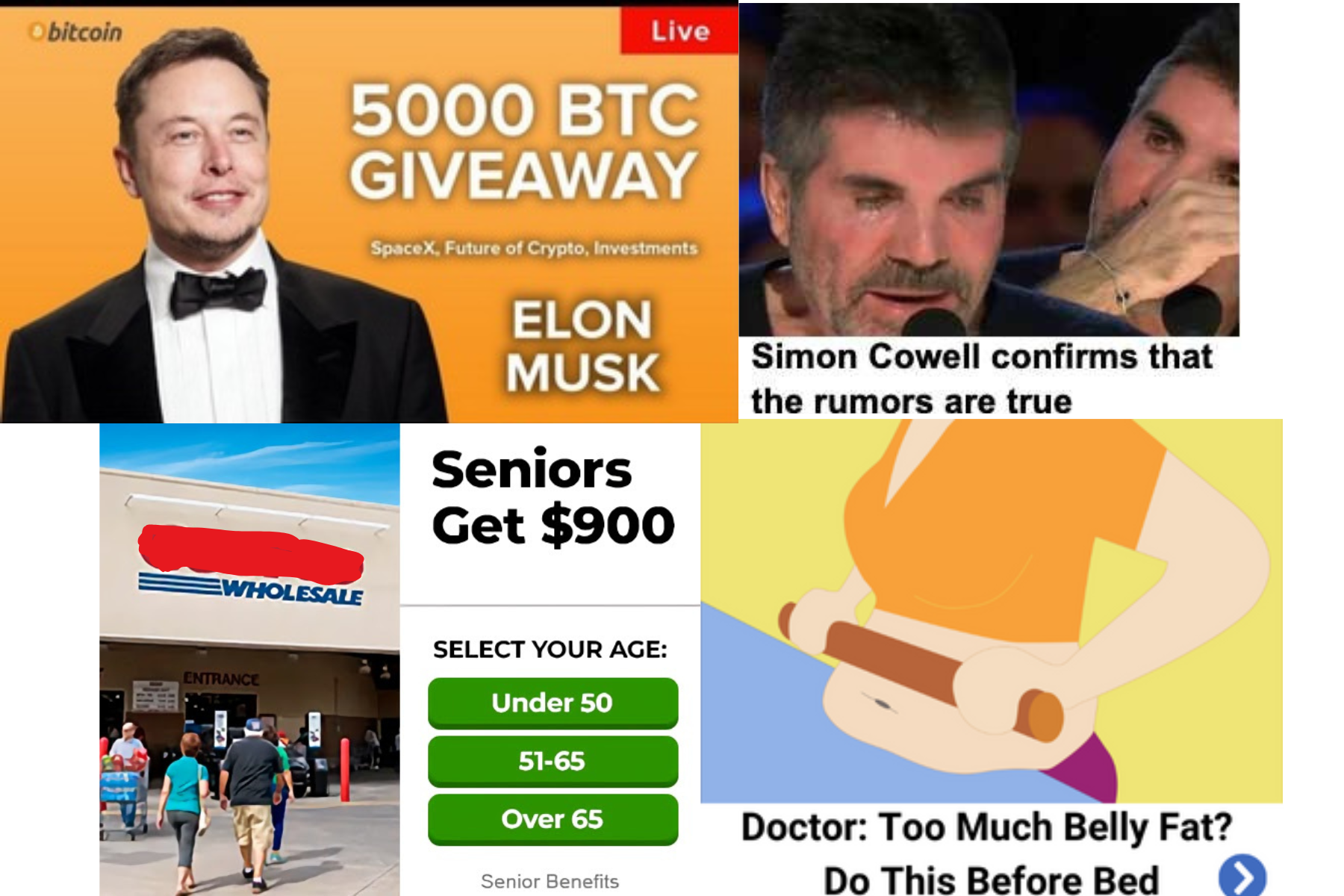
Attacks employing malicious files for theft and/or unauthorized use of consumers’ sensitive data.
EXAMPLES:
Content executing click and/or impression fraud.
EXAMPLES:

Targeted at the most vulnerable groups online (e.g., seniors, minors), this evasive malware convinces consumers that their devices are compromised and to call a bogus tech support operator, who takes remote control to cause financial harm.

Once the bane of mobile display advertising, GhostCat (aka ScamClub) has exploited programmatic video arbitrage to barrage consumers with phishing redirects—often on premium publishers.
Long a plague of email and search, SocGholish has broken into display advertising—via compromised landing pages from legit advertisers—to instantly infect consumer devices with backdoors… And it appears to be targeting governments and infrastructure.
Phishing upstart StringRipper hijacks the creatives and tags from legit advertisers, and then uses advanced levels of fingerprinting and obfuscation to evade detection and hit vulnerable consumers.
Threat actors are increasingly using AI and cloaking to lure consumers into crypto schemes or buy shady health products via fake celebrity endorsements.
PhonyFetcher is a sophisticated, multi-pronged campaign that mimics legitimate websites, browser alerts, and tech support tools to infiltrate user devices—especially those belonging to the most vulnerable internet users: seniors and minors.
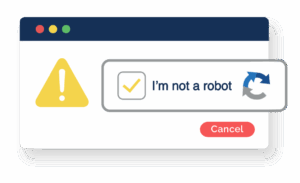
A classic example of social engineering, this attack vector uses CAPTCHAs to manipulate the victim into unknowingly executing malicious commands themselves. This makes detection and prevention significantly more challenging.
YOUR Data. We take privacy seriously. If you’d like to know the data we have about you, all you have to do is ask. You can contact us via email at info@themediatrust.com
© 2025 TMT DIGITAL, INC. | Privacy Policy | Terms of Use