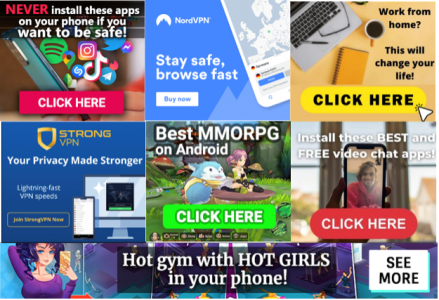
Gaining reach via ad platforms, this fast-spreading malware compromises brand websites to lure consumers into downloading backdoors.
As demonstrated by the dramatic rise of MimicManager-3PC in late 2022, threat actors are finding compromised brand websites an economical way to spread malware to the masses. However, a new threat ups the ante by delivering malicious creatives that appear far too realistic for any consumer’s good.
Dubbed MudOrange-3PC* (MudOrange), this sprawling and evolving threat with a sophisticated execution entices consumers to install backdoors on their devices. In addition to enabling ransomware, keyloggers and cryptojackiing, these backdoors expose millions of consumer devices to future attacks.
Gestating on long-tail and adult websites since late 2021, MudOrange is now compromising brand websites and spreading to consumers via brand advertising campaigns. Large AdTech providers and dozens of premium publisher websites have already been affected by the threat. [Figure 1]
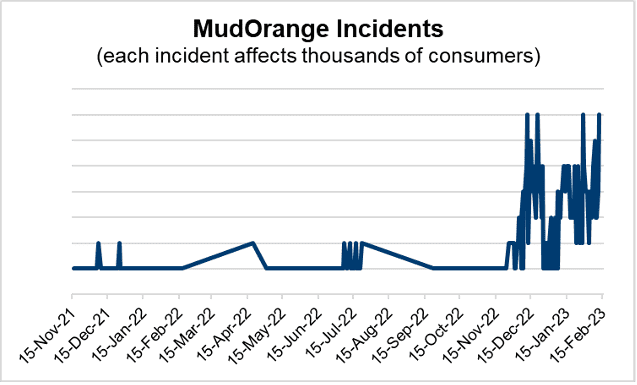
As of February 2023, MudOrange used more than 40 IOC (indicators of compromise) and multiple malicious payloads, helping it evade detection and maximize reach. While detected in 10 of the most populous countries in the world, MudOrange appears to affect U.S. consumers 3X more often than those in Brazil, India, France, Germany, and Japan.
Dirty Delivery
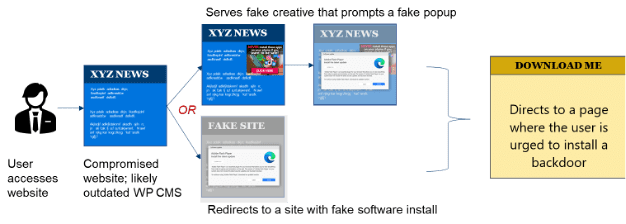
In most cases, the websites affected by MudOrange use outdated content management systems (CMS), but in some cases cross-site scripting and direct web server access can lead to infection. Once a vulnerable website is identified, it is injected with malicious code through a JavaScript library. The “atOptions” object configures “invoke.js” and dictates the behavior and type of malicious content served to users.
After using fingerprinting to ensure it is being served to an actual person rather than to an emulator or into a test environment, invoke.js executes a convoluted series of scripts to deliver a pop-up creative on top of the actual brand’s website. [Figure 2]
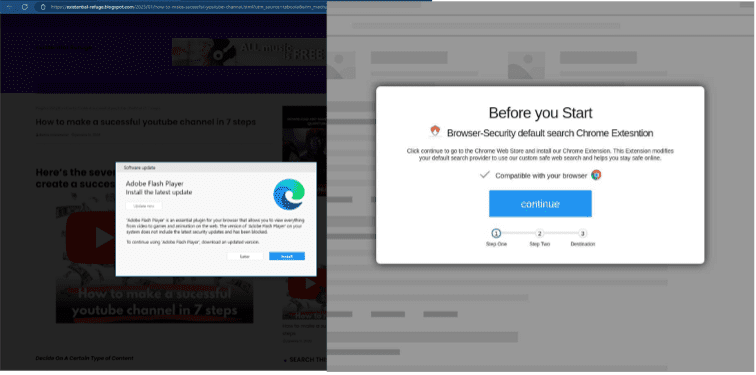
These pop-ups resemble actual interstitials consumers might come across on various publishers, using well-known brand names for products like VPNs, security tools, and multiplayer online role-playing games. [Figure 3]
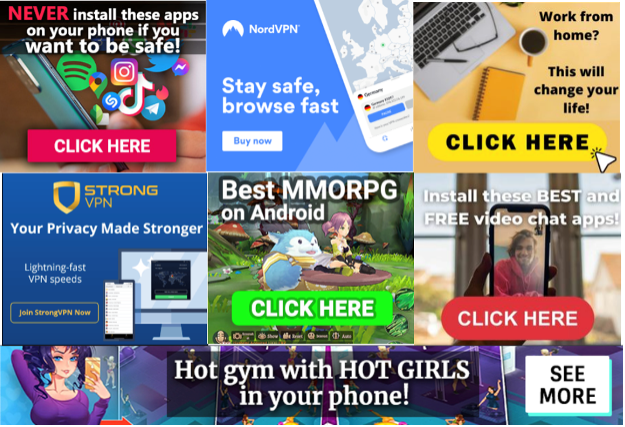
The creatives lead to landing pages that push warnings about viruses and fake software updates to lure consumers into downloading backdoors that can be accessed for future attacks like ransomware and cryptojacking. [Figure 4]
Cleaning Up Compromised Brand Websites
Unlike the highly targeted MimicManager, MudOrange does not appear to target specific devices or browsers. However, it’s still an elevated threat due to its breadth and ability to actively evade detection by automated browsers and scanners. It’s critical to identify and remediate by following these steps:
- Search for invoke.js operating on client side
- Update CMS administrator credentials
- Harden your website
- Audit plugins to ensure they are up to date. If using a WordPress CMS, pay particular attention to core files too
- Update web servers to the latest version and review configuration files
- Disable cross-site scripting, SQL injection in your firewall
- Add the 40+ IOCs to your blocklist (Note, this is already in place with our Media Filter tool)
Not only do auto-redirects and popups mar user experience, they lead consumers straight to dangerous situations. To avoid this in the future, website operators should constantly review client-side code and remove unauthorized domains/vendors. Ensure you monitor your properties via multiple device profiles and actual devices as MudOrange actively combs for emulators and other threat-detection tools. If your properties are ad-supported, ask your upstream partners how they address this unauthorized domain and the malvertising it enables.
Download our detailed report diving into the specifics of MudOrange’s complicated pop-up delivery.
* Naming Convention Note: Backdoors are represented by earth-related themes. Color represents the gravity of the threat using the ROYGBIV scale, where red signifies major and violet signifies minor impact. 3PC refers to the use of third-party code to distribute the malware; in this instance, it involves two channels: a compromised CMS and the digital advertising ecosystem.